This can be exploited via the following path: /admin/config/confirm_email. By sending an email to the end user, an attacker can bypass authentication and change their settings or perform other actions. This affects Atlassian Jira Server and Data Center versions before 8.13.18, versions 8.14.0 and later before 8.20.6, and versions 8.21.0 and later before 8.22.0. This also affects Atlassian Jira Service Management Server and Data Center versions before 4.13.18, versions 4.14.0 and later before 4.20.6, and versions 4.21.0 and later before 4.22.0. For more information on this, see Jira 7.5 Remote Code Execution - CVE-2018-8087.
Jira 7.6 Remote Code Execution - CVE-2018-8088
This can be exploited via the following path: /confirm_email. By sending an email to the end user, an attacker can bypass authentication and change their settings or perform other actions. This affects Atlassian Jira Server versions before 7.6.0, versions 7.7.0 and later before 7.8.2, and versions 7.9.0 and later before 7.10.4. This also affects Atlassian Jira Service Management Server versions before 4.13.18, versions 4.14.0 and later before 4.20.6, and versions 4.21.0 and later before 4.22-jira61-1-rc1
What is Jira?
Jira is an Atlassian application which helps teams manage projects. It offers a modern user interface and features which are easy to use, such as Jira Agile - a tool for agile project management that makes it easier for teams to get their work done quickly and efficiently. Jira also offers powerful data-driven workflows for complex batch processes, resource management with Kanban boards, collaboration tools for multiple users, and more.
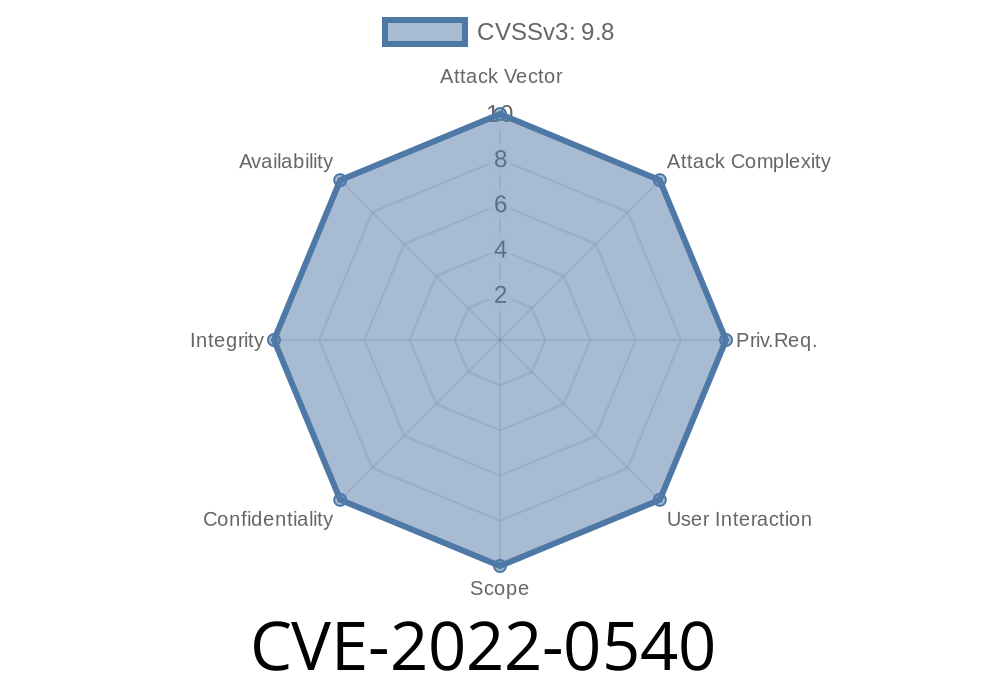
Timeline
Published on: 04/20/2022 19:15:00 UTC
Last modified on: 06/10/2022 14:49:00 UTC