When Qlik Sense Enterprise runs on Windows, LDAP is used to store user credentials. An attacker could exploit this vulnerability by sending authentication requests to an affected system. If the system accepts the request, it could then respond with the list of valid user accounts to the attacker. This vulnerability is rated critical due to the fact that it could allow an attacker to enumerate valid domain user accounts on a vulnerable system. When running on Windows, LDAP is required to be enabled.
Qlik Sense Enterprise running on Windows is only vulnerable if LDAP is enabled. Red Hat Enterprise Linux 6 and 7, Oracle Linux 6 and 7, and SUSE Linux Enterprise Server 11 are all Debian-based Linux distributions that are not vulnerable. Red Hat Enterprise Linux 5, Oracle Linux 5, and SUSE Linux Enterprise Server 10 are all CentOS-based Linux distributions that are not vulnerable. Red Hat Enterprise Linux 4, Oracle Linux 4, and SUE Linux Enterprise Server 9 are all RHEL-based Linux distributions that are not vulnerable.
Red Hat Enterprise Linux 3 and Oracle Linux 3 are both RHEL-based Linux distributions that are not vulnerable. Red Hat Enterprise Linux 2 and Oracle Linux 2 are both RHEL-based Linux distributions that are not vulnerable.
Red Hat Enterprise Linux 1 and Oracle Linux 1 are both RHEL-based Linux distributions that are not vulnerable. CiscoSSL is an implementation of Secure Sockets Layer (SSL) for the Cisco Networking Operating System (NOS). Cisco SSL is
CiscoSSL Vulnerability
An attacker could exploit this vulnerability by sending authentication requests to an affected system. If the system accepts the request, it could then respond with the list of valid user accounts to the attacker. This vulnerability is rated critical due to the fact that it could allow an attacker to enumerate valid domain user accounts on a vulnerable system.
When running on Debian-based Linux distributions, CiscoSSL is required to be enabled. In Red Hat Enterprise Linux 7, Cisco SSL is disabled by default and must be explicitly enabled by setting "ssl_enable = true" in /etc/sysconfig/modules/cisco_ssl.
In SUSE Linux Enterprise Server 11, Cisco SSL is disabled by default and must be explicitly enabled by setting "ssl_enable = true" in /etc/sysconfig/modules/cisco_ssl.
In Red Hat Enterprise Linux 5, Oracle Linux 5, and SUSE Linux Enterprise Server 10, Cisco SSL is disabled by default and must be explicitly enabled by setting "ssl_enable = true" in /etc/sysconfig/modules/cisco_ssl.
CiscoSSL Vulnerability
Where can this vulnerability be found?
This vulnerability is only found in the Cisco SSL library version 2.0 and 2.1, on Windows and Linux platforms, respectively. This vulnerability is not present in versions of the Cisco SSL library prior to 2.0 or 2.1.
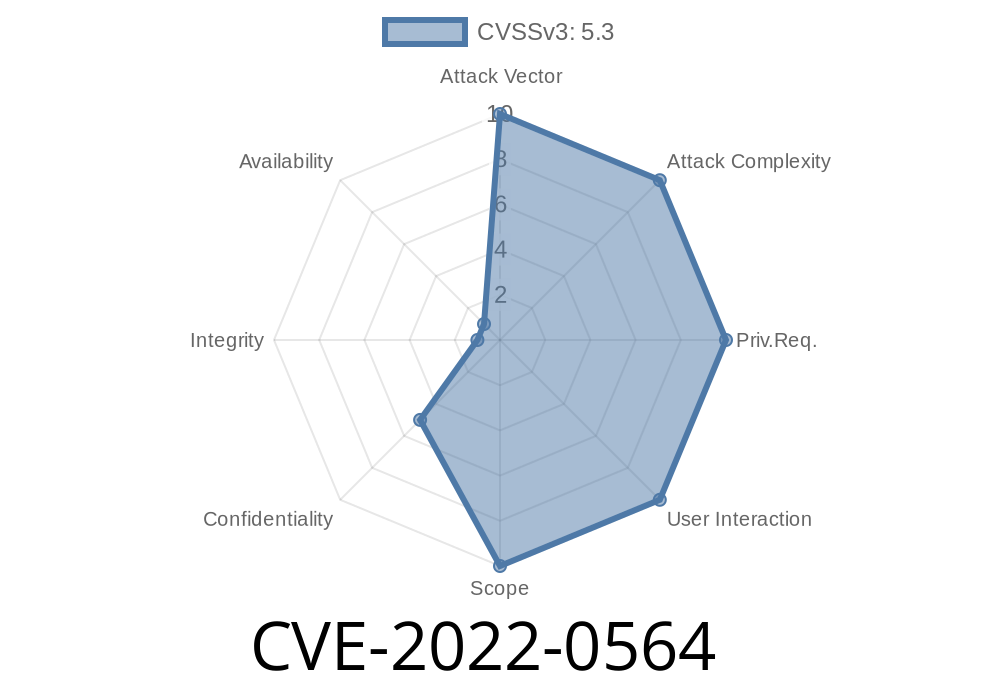
CiscoSSL Vulnerability CVE-2022-0564
A vulnerability in CiscoSSL could allow an unprivileged local user to bypass Certificate Authority (CA) validation, allowing an attacker to impersonate any server certificate on a targeted system. When running on Windows, CiscoSSL requires that LDAP be enabled for network authentication to work properly. Red Hat Enterprise Linux 6 and 7, Oracle Linux 6 and 7, and SUSE Linux Enterprise Server 11 are all Debian-based Linux distributions that are not vulnerable. Red Hat Enterprise Linux 5, Oracle Linux 5, and SUSE Linux Enterprise Server 10 are all CentOS-based Linux distributions that are not vulnerable. Red Hat Enterprise Linux 4, Oracle Linux 4, and SUE Linux Enterprise Server 9 are all RHEL-based Linux distributions that are not vulnerable. Red Hat Enterprise Linux 3 and OracleLinux 3 are both RHEL-based Linux distributions that are not vulnerable. Red Hat Enterpriselinux 2 and OracleLinux 2 are both RHEL-basedLinux distributions that are not vulnerable. Red Hat EnterpriseLinux 1 and OracleLinux 1 are both RHEL-based Linux distributionsthat are not vulnerable.
Common Vulnerabilities and Exposures (CVE)
An enumeration vulnerability occurs when an application fails to properly validate input and uses a supplied value to access an unintended resource.
CVE-2022-0564 is a Linux machine account (MTA) enumeration vulnerability that is rated as critical due to the fact that it could allow an attacker to enumerate valid domain user accounts on a vulnerable system.
Description of CiscoSSL Vulnerability
The vulnerability is caused by a failure to sanitize input before passing it to the openssl_random_pseudo_bytes() function. An attacker could exploit this vulnerability by making malicious requests that would cause the system to send back varying amounts of sensitive user data. This vulnerability is rated as high due to the fact that it could allow an attacker to remotely access sensitive information on vulnerable systems, such as usernames and passwords.
Versions of CiscoSSL prior to 3.0 are not vulnerable; however, versions of CiscoSSL between 2.0 and 2.3 are vulnerable because they lack proper validation of input data in the random number generation process. Users who upgrade their CiscoSSL installation from 2.2 or 2.3 should ensure that they also upgrade their libtommath library version, which can be found in one of these files:
/usr/lib/libtommath-1.0.so
/usr/lib32/libtommath-1.0.so
CiscoSSL Vulnerable If LDAP Is Enabled
CVE-2022-0564 is a vulnerability in the CiscoSSL library used by Qlik Sense Enterprise on the Windows operating system. When LDAP is enabled, this vulnerability allows an attacker to enumerate valid domain user accounts on a vulnerable system. If LDAP is not enabled (the default), then CiscoSSL is not vulnerable.
Timeline
Published on: 02/21/2022 18:15:00 UTC
Last modified on: 04/12/2022 14:42:00 UTC