In this type of attack, an attacker tricks a user into running a specially crafted script on the web server. The specially crafted script can then cause buffer overflow on the web server and execute arbitrary code on the server. In GitHub, we have a variety of ways to login to the application from our browser. We can login via GitHub.com, GitHub Enterprise, GitHub Pages, GitHub Mobile, GitHub Enterprise, GitHub Learning, GitHub Gists, GitHub Enterprise, GitHub Open Source, GitHub Enterprise, GitHub Pro, GitHub Enterprise, GitHub on the App Store, or via SSH. Once we login to GitHub, we can then create a new repository or fork an existing one. The next step depends on the type of application. For applications hosted on GitHub.com, we can edit the repository pages to add a “Get started” link that directs users to the documentation. For GitHub Enterprise, GitHub Pages, GitHub Mobile, GitHub Enterprise, GitHub Learning, GitHub Gists, GitHub Enterprise, GitHub Open Source, GitHub Enterprise, GitHub Pro, GitHub Enterprise, GitHub on the App Store, or GitHub SSH, we can add instructions in the README on how to access the repository. Next, we need to find a vulnerable script in the repository. In GitHub, all the repositories are public and can be viewed by anyone. GitHub provides a search feature that enables us to search the repository for any specific phrase or keyword. The next step is to craft a malicious URL to add to the search query. The URL
Search Query Development
The first step in developing a malicious URL to add the search term is to craft a malicious GET request. The malicious GET request should include the search term and another random string of characters. When the browser requests the URL, GitHub will interpret it as a GET request for that specific URL.
GitHub Search API
GitHub provides two ways to search for a vulnerability. One of them is with the GitHub Search API, which is a RESTful web service that allows users to search repositories for certain text or content within the repositories. The second method is by searching for vulnerable files in the repository itself.
The rest of this blog post will show how we can find vulnerable scripts and use them in an attack against the server.
Timeline
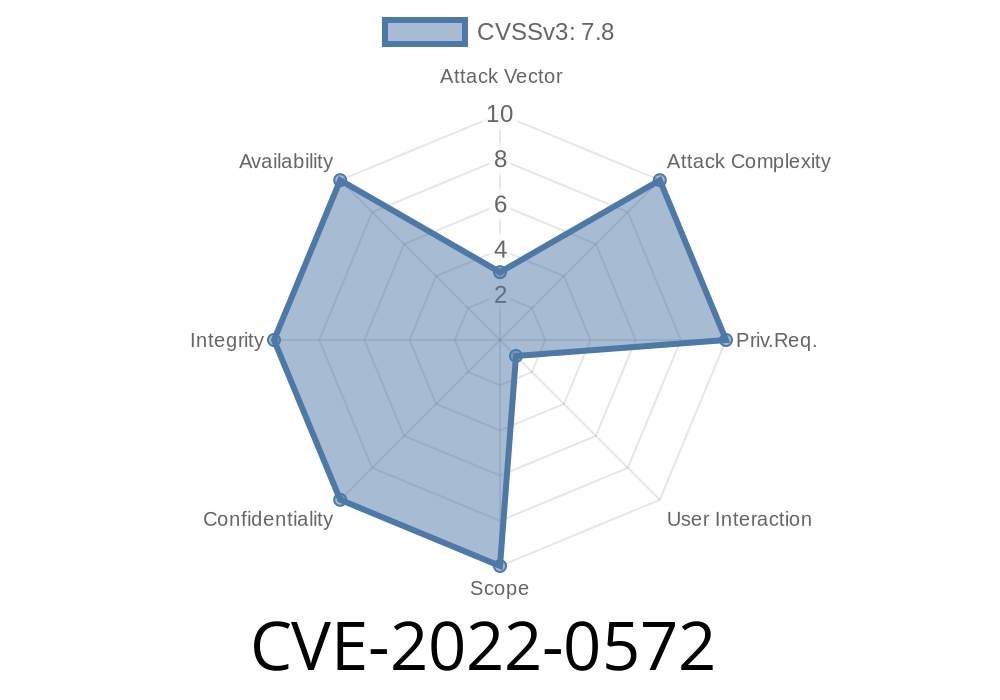
Published on: 02/14/2022 12:15:00 UTC
Last modified on: 05/16/2022 22:15:00 UTC
References
- https://huntr.dev/bounties/bf3e0643-03e9-4436-a1c8-74e7111c32bf
- https://github.com/vim/vim/commit/6e28703a8e41f775f64e442c5d11ce1ff599aa3f
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/4GOY5YWTP5QUY2EFLCL7AUWA2CV57C37/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/7ZLEHVP4LNAGER4ZDGUDS5V5YVQD6INF/
- https://lists.debian.org/debian-lts-announce/2022/05/msg00022.html
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-0572