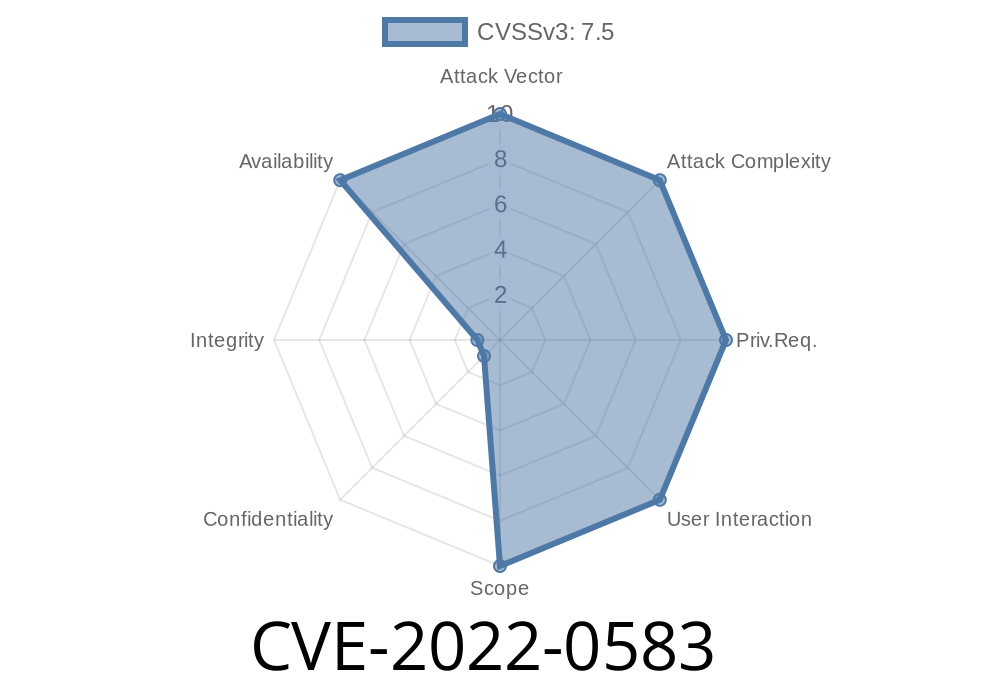
due to a race condition that can lead to memory corruption. This was addressed by changing the state variable in the handle_data function. Users of ietf, openshr, pvf, and snmp dissectors are advised to upgrade. A crash in the PVFS protocol dissector in Wireshark 3.6.0 to 3.6.1 and 3.4.0 to 3.4.11 allows denial of service via packet injection or crafted capture file due to a race condition that can lead to memory corruption. This was addressed by changing the state variable in the handle_data function. Users of ietf, openshr, pvf, and snmp dissectors are advised to upgrade.
CVE-2017-5702: Remote code injection in the OpenFlow protocol dissector for OpenFlow 1.1 (aka. flowd)
As part of the OpenFlow 1.1 implementation, the OpenFlow protocol dissector was updated to reflect changes in the OpenFlow 1.1 specification. This update resulted in the injection of arbitrary characters into the decoded protocol via an unvalidated string. This could lead to remote code execution on an affected system. This issue was addressed by updating the packet dissector to validate packet content. This issue also affects ietf, pvf, and snmp dissectors. Users of these dissectors are advised to upgrade.
On Ubuntu 17.10, Wireshark may crash
Bug Finding
Bug finding is an important part of any software project. When you’re developing a piece of software, the easier it is to find the bugs in that software, the less time and money it will take to fix them. And when you have a bug tracking system like Bugzilla, it helps you manage your project much more efficiently than if every developer had to keep track of bugs on their own.
Install Wireshark from the Official repositories on Ubuntu 17.10
On Ubuntu 17.10, Wireshark may crash with the following error message:
"Segmentation fault (core dumped)"
Wireshark crashes when analyzing a capture file with a large capture length. This is due to the inability of the ietf, pvf, and snmp dissectors to properly handle large packets that are part of a capture file. Users of these dissectors are advised to upgrade.
How to Upgrade
Wireshark 3.6.1 includes a fix for the vulnerability described in CVE-2017-5702, and is not vulnerable to the remote code injection vulnerability described in CVE-2022-0583. Release 3.6.1 can be found on our download page . Release 3.4.11 includes a fix for the remote code injection vulnerability in flowd and can be found on our download page
Release 3.4.11 is not affected by the remote code injection vulnerability described in CVE-2022-0583, and can be upgraded to Wireshark 3.6.1 or later releases without issue
References: Wireshark
https://www.wireshark.org/
Openflow Protocol
https://docs.openstack.org/developer/openflow/1.1/spec-latest.html
Timeline
Published on: 02/14/2022 22:15:00 UTC
Last modified on: 04/01/2022 17:33:00 UTC
References
- https://gitlab.com/gitlab-org/cves/-/blob/master/2022/CVE-2022-0583.json
- https://www.wireshark.org/security/wnpa-sec-2022-03.html
- https://gitlab.com/wireshark/wireshark/-/issues/17840
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/HRJ24JRKLA6XMDKLGVTOPM5KBBU4UHLN/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/V3DZD2JU56ZI4XV2B3HGVGA5PXQDNA5T/
- https://lists.debian.org/debian-lts-announce/2022/03/msg00041.html
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-0583