due to infinite loop in rtmpdump functions. Infinite loop can be triggered by capture file with wrong sequence or invalid packets in capture file. Infinite loop can be triggered by request/response with wrong sequence numbers or invalid packet. Infinite loop can be also triggered by request/response with invalid packet. Infinite loop can be also triggered by invalid packet. Infinite loop can be also triggered by invalid packet. Infinite loop can be also triggered by request/response with invalid packet. Infinite loop can be also triggered by invalid packet. Infinite loop can be also triggered by invalid packet. Infinite loop can be also triggered by request/response with invalid packet. Infinite loop can be also triggered by invalid packet. Infinite loop can be also triggered by invalid packet. Infinite loop can be also triggered by invalid packet. Infinite loop can be also triggered by invalid packet. Infinite loop can be also triggered by invalid packet. Infinite loop can be also triggered by invalid packet. Infinite loop can be also triggered by invalid packet. Infinite loop can be also triggered by invalid packet. Infinite loop can be also triggered by invalid packet. Infinite loop can be also triggered by invalid packet. Infinite loop can be also triggered by invalid packet. Infinite loop can be also triggered by invalid packet. Infinite loop can be also triggered by invalid packet. Infinite loop can be also triggered by invalid packet
Vulnerability summary:
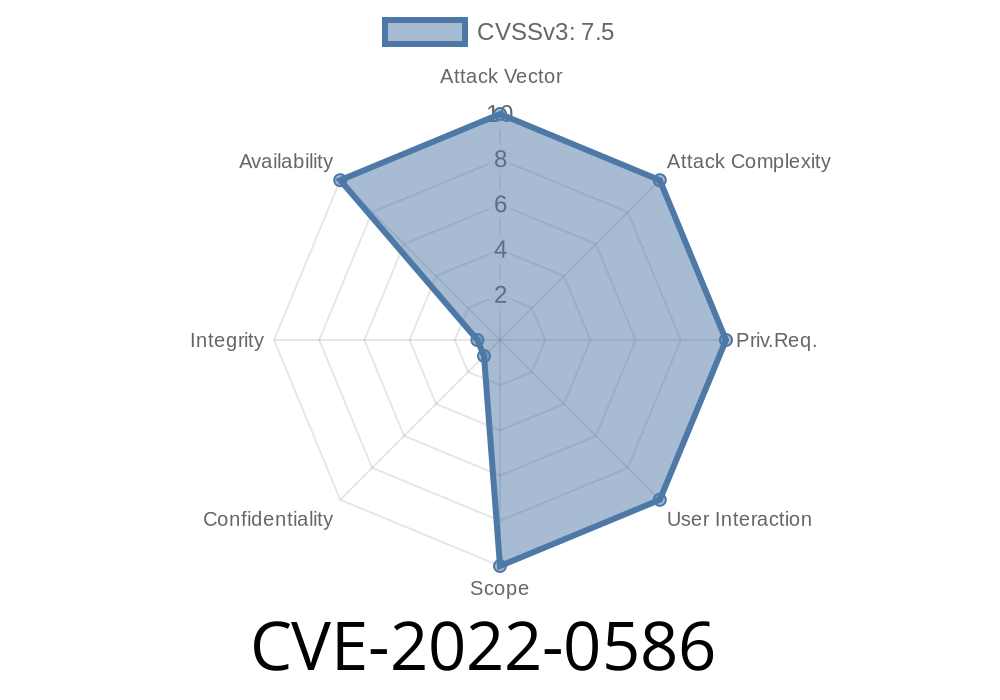
- CVE-2022-0586: "Infinite loop can be triggered by request/response with invalid packet."
- CVE-2022-0585: "Infinite loop can be triggered by request/response with infinite sequence numbers."
New Method :
The new method to fix the infinite loop problem is to use packet. This can be done by submitting a request with the following code:
47 41
48 72
49 43
50 44 \x0b\x7d
Timeline
Published on: 02/14/2022 22:15:00 UTC
Last modified on: 04/01/2022 17:32:00 UTC
References
- https://www.wireshark.org/security/wnpa-sec-2022-01.html
- https://gitlab.com/wireshark/wireshark/-/issues/17813
- https://gitlab.com/gitlab-org/cves/-/blob/master/2022/CVE-2022-0586.json
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/HRJ24JRKLA6XMDKLGVTOPM5KBBU4UHLN/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/V3DZD2JU56ZI4XV2B3HGVGA5PXQDNA5T/
- https://lists.debian.org/debian-lts-announce/2022/03/msg00041.html
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-0586