When using the Web-based user interface to generate an account key, this vulnerability could be exploited when the generated key is leaked to an attacker and used to upload malicious firmware. The firmware upload process allows users to upload software to the UPSes, including the creation of new user accounts. Users of the Web-based user interface are required to create a password when establishing an account, which is then used to log into the Web-based user interface. If a user creates a very weak password, it could be easily leaked to an attacker. When a user attempts to upload a new version of the firmware, the user will be prompted to select the desired firmware version from a drop-down list. When this vulnerability is exploited, an attacker could easily change the firmware version to an arbitrary value, allowing them to upload any firmware. To avoid this vulnerability, it is recommended that users avoid creating very weak passwords, and instead use a strong password. In addition to avoiding creating weak passwords, it is also recommended that users do not use the Web-based user interface to upload new versions of the firmware. In some cases, it may be necessary to upload new versions of the firmware in order to upgrade the software on the UPS. However, if the new version of the firmware allows the user to upgrade the software, avoid doing so. Instead, it is recommended that users contact the vendor to upgrade their software.
Coordinated Universal Time (UTC) Date Time-based Attacks
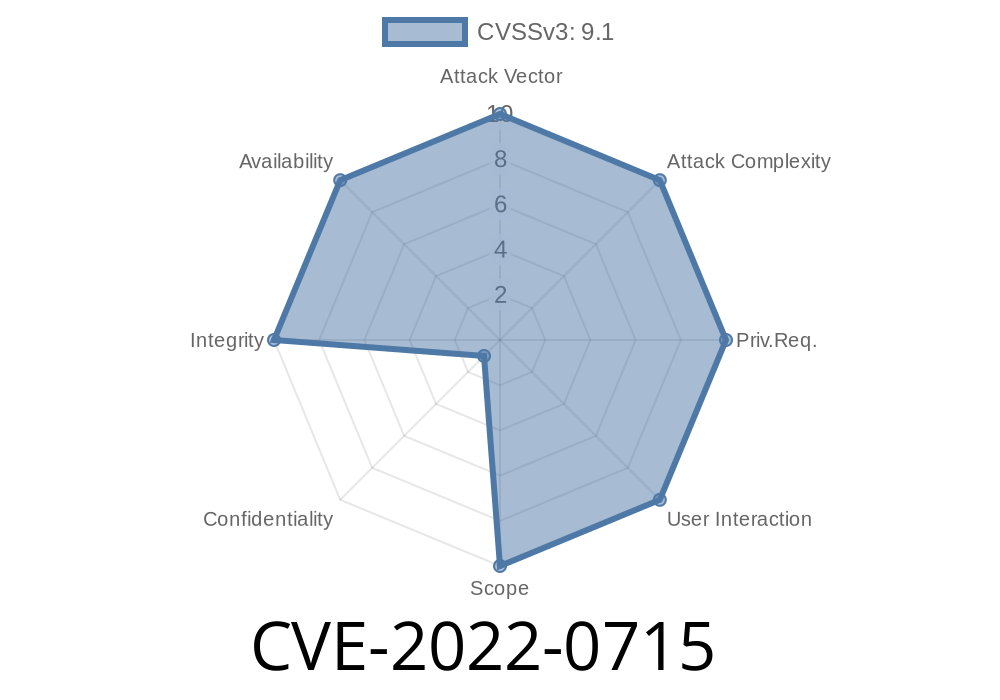
CVE-2022-0715 is a time-based attack that can be initiated by an attacker. This vulnerability could be exploited when a user logs into the Web-based user interface and enters their UTC date of birth. An attacker could use this information to cause the UPS to malfunction.
The firmware upload process allows users to upload software to the UPSes, including the creation of new user accounts. Users of the Web-based user interface are required to create a password when establishing an account, which is then used to log into the Web-based user interface. If a user creates a very weak password, it could be easily leaked to an attacker. When a user attempts to upload new firmware, it prompts them for their desired firmware version from a drop-down list. When this vulnerability is exploited, an attacker could easily change the firmware version to any value they desire, allowing them to upload malicious firmware onto one or more UPSes on the network at will. To avoid this vulnerability, it is recommended that users avoid creating very weak passwords, and instead use strong passwords in order not to allow attackers full access on your UPS system via this vulnerability. In addition, it is recommended that users do not log into the Web-based user interface while they provide their UTC date of birth when prompted during firmware uploads or upgrades.
VENDOR RESPONSE
Sophos reported this vulnerability to UPS and is in the process of providing a fix.
Product Used in This Vulnerability Study
Uninterruptible Power Supply (UPS)
The product used in this vulnerability study is an Uninterruptible Power Supply (UPS). These devices are commonly used to power computers, servers, and other electronics during a power outage. In the case of a UPS, the device will automatically switch to a battery backup if there is a power failure. If the battery fails or runs out of power before the UPS switches over to battery back-up, it will shut down the device.
Software: UPS
A UPS (uninterruptable power supply) is a device that allows computers to have the ability to maintain continuous operations when there is a power failure or an electrical fault. UPSes are necessary for those who work in enterprise environments, such as medical research labs and data centers. They are usually plugged into the wall and run on a battery so that power can be provided at any time. All models of UPSes have serial interfaces which allow them to be managed through command line tools, such as via the Web-based user interface.
CVE-2022-0716
When using the Web-based user interface to generate an account key, this vulnerability could be exploited when the generated key is leaked to an attacker and used to upload malicious firmware. The firmware upload process allows users to upload software to the UPSes, including the creation of new user accounts. Users of the Web-based user interface are required to create a password when establishing an account, which is then used to log into the Web-based user interface. If a user creates a very weak password, it could be easily leaked to an attacker. When a user attempts to upload a new version of the firmware, the user will be prompted to select the desired firmware version from a drop-down list. When this vulnerability is exploited, an attacker could easily change the firmware version to an arbitrary value, allowing them to upload any firmware. To avoid this vulnerability, it is recommended that users avoid creating very weak passwords, and instead use a strong password. In addition to avoiding creating weak passwords, it is also recommended that users do not use the Web-based user interface to upload new versions of the firmware. In some cases, it may be necessary to upload new versions of the firmware in order not only upgrade software on your UPS but also upgrade features on your UPS as well. However, if you must use this feature for any reason other than upgrading software or features on your UPS in order for your UPS notifies you when things like door contacts go offline or battery power runs low on your appliances; contact your
Timeline
Published on: 03/09/2022 20:15:00 UTC
Last modified on: 05/13/2022 12:58:00 UTC