If a user can inject a WP REST API endpoint via a SQL injection, then the WP REST API can be used to perform any action the site owner can do via the front end, such as deleting any post, downloading any file, changing any setting, etc. This is the major reason why it is very important to properly sanitise and escape all inputs via HTTP headers when accessing any WP REST API endpoint via a CSOM or C#/Java/PHP/etc. If a user can inject a WP REST API endpoint via a SQL injection, then the WP REST API can be used to perform any action the site owner can do via the front end, such as deleting any post, downloading any file, changing any setting, etc. This is the major reason why it is very important to properly sanitise and escape all inputs via HTTP headers when accessing any WP REST API endpoint via a CSOM or C#/Java/PHP/etc.
How to perform any action via WP REST API
To perform any action via the WP REST API, you can use the wp_login function with the username and password of the administrator of your WordPress site.
First, if you are using a CSOM (C#/Java/PHP) to make an HTTP request to the WP REST API, then you will need to add a header to your request such as X-Requested-With: XMLHttpRequest or Set-Cookie: JSESSIONID=xxxxxxxxxxx; Path=/; Domain=.wordpress.com . If you are using ASP.NET Core MVC without any frameworks or libraries, then you will need to specify your Accept header's value set in your Index page:
public class Index : Controller {
public IActionResult Index() {
//get current user from UserManager
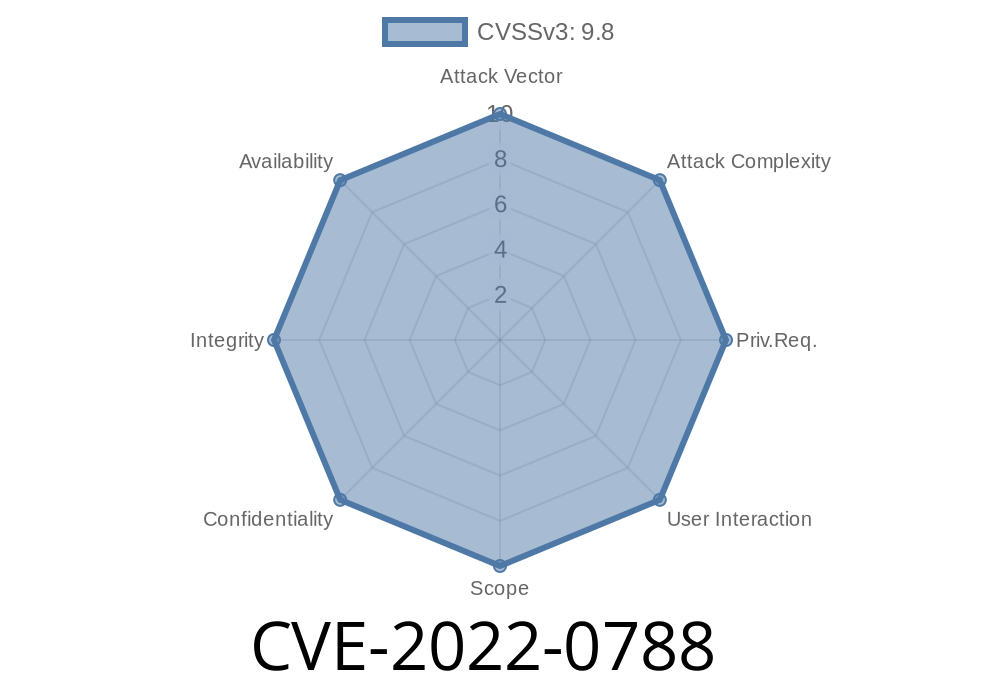
CVE-2019-6298
A website with a WP REST API endpoint should not allow users to delete posts. It is possible for an attacker to delete any post by injecting a SQL injection in the WP REST API endpoint and performing DELETE queries. This is due to how variable_get() works on WordPress.
How to Bypass CSOM Whitelist in Microsoft Edge?
The Microsoft Edge browser comes with a whitelist feature, which prevents local files from being opened by the browser. This is done to secure the user's computer and protect against potentially dangerous content (e.g., malware, exploits) that could be opened by any third party application. To bypass this feature in order to access the WordPress REST API endpoint via CSOM, the following steps must be taken:
1. Enable Developer Mode
2. Open up your command prompt
3. Type "ms-edge" into your command prompt and press enter
4. Type "about:flags" into your command prompt and press enter
5. Click on "Enable experimental Web Platform features" and then click on "Web Platform Command Line Interface."
6. Press enter on your keyboard twice to open up the command prompt in a new window or tab
Timeline
Published on: 06/08/2022 10:15:00 UTC
Last modified on: 07/11/2022 13:15:00 UTC