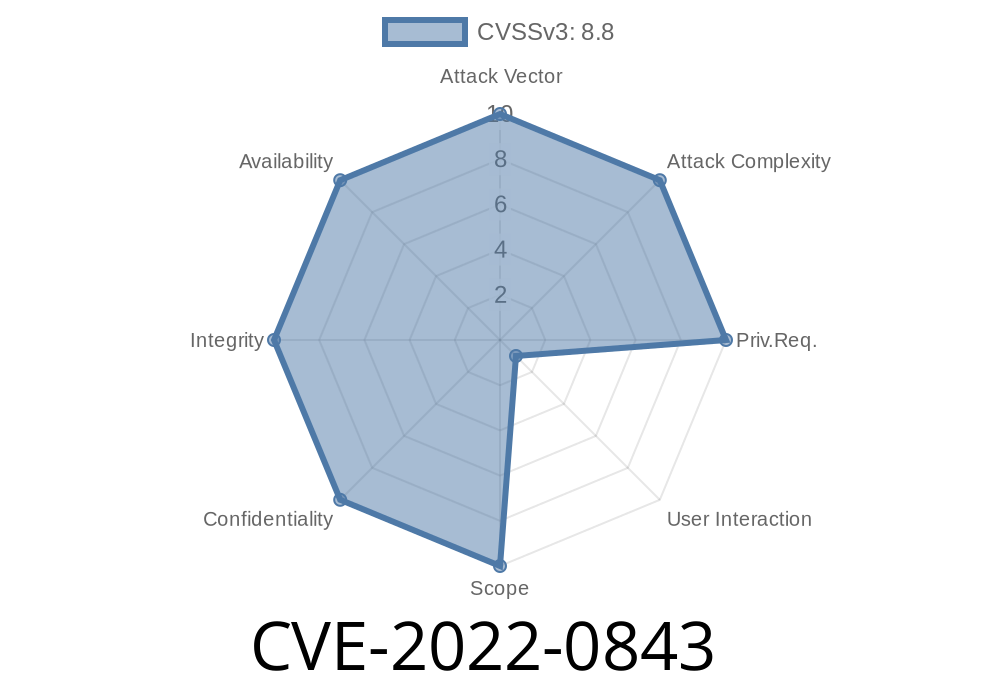
In early 2022, Mozilla patched several memory safety bugs in their popular Firefox web browser. These flaws mostly flew under the radar for a lot of users, but are serious: they could allow an attacker to run their own code—potentially letting them take control of your computer. Let’s break down CVE-2022-0843, a memory safety bug discovered by Mozilla developers Kershaw Chang, Ryan VanderMeulen, and Randell Jesup, explain how it works with code samples, and show why updating Firefox is important.
What Is CVE-2022-0843?
CVE-2022-0843 is a memory safety vulnerability found in Firefox versions earlier than 98. The official Mozilla Security Advisory reads:
> “Mozilla developers Kershaw Chang, Ryan VanderMeulen, and Randell Jesup reported memory safety bugs present in Firefox 97. Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code.”
In simple terms, if a hacker finds the right way to “poke” at memory in Firefox, they can trick the browser into doing something it shouldn’t—like running a malicious program on your computer.
Background: Memory Safety in Browsers
Browsers like Firefox are huge and complex. They constantly deal with HTML, JavaScript, images, and data from all over the internet, which can be unpredictable. If the code handling all this isn’t careful with how it uses computer memory, bugs can creep in.
The program leaks memory pointers that could let hackers manipulate memory layout.
Often, these bugs can be triggered by making the browser process specially crafted web pages or files.
What Did the Researchers Find?
The specifics of CVE-2022-0843 are not all public, but Mozilla’s bug trackers and security blog give us clues.
Relevant bug tracker for more technical users:
- Mozilla Bug 1758028 – CVE-2022-0843 (may require access)
The developers found several cases where Firefox 97 mishandled memory — probably in how it handled certain web content or media streams.
Here’s a (generalized) C++ code snippet demonstrating what a typical memory corruption bug might look like in browser code:
void processInput(const char* data, size_t length) {
char buffer[64];
if (length > sizeof(buffer)) {
// Error! data is too large, returns early.
return;
}
// Fails to check if 'length' is negative or huge, can overflow buffer
memcpy(buffer, data, length);
}
If an attacker creates input that tricks processInput into copying too much data, they can overwrite the buffer, potentially controlling browser execution.
Exploit Details
The Mozilla advisory states that “with enough effort” an attacker could exploit this bug to run arbitrary code. Typically, these attacks work like this:
1. Preparation: An attacker sets up a web page with malicious code or data that triggers the memory corruption bug in Firefox.
2. Trigger: The browser, while parsing or displaying the attacker's content, makes a memory error like an out-of-bounds read/write or a use-after-free.
3. Control: If the attacker can precisely control the memory layout (using so-called “heap spraying” or similar techniques), they might overwrite critical areas of memory.
4. Payload: The attacker injects and executes their own code—this might be a simple “calc” pop or something more dangerous, like a backdoor.
In practice, these steps are very technical and require deep knowledge of browser internals. But, history shows that determined attackers, especially with state-level resources, can pull it off.
Here’s a proof-of-concept (PoC) pseudocode for exploiting such bugs (note: illustrative, not actual exploit code):
// attacker-controlled web page
let spray = [];
for (let i = ; i < 10000; i++) {
// Fill browser memory with controllable data
spray.push(new Array(100).fill(x41414141));
}
// Trigger bug with crafted input
fetch('/malicious-file').then(response => response.arrayBuffer())
.then(buffer => {
// Send this data to vulnerable browser API
unsafeBrowserApi(buffer);
});
Real-World Impact
If a user visited a malicious website with an outdated Firefox version (before 98), there was a theoretical risk that hackers could exploit this bug to install malware or steal data.
Good news:
No known attacks have been reported in the wild so far.
- The bug was patched quickly by Mozilla in Firefox 98.
How To Stay Safe
- Update Firefox: Always keep your browser up to date. Go to “Help” > “About Firefox” to check for updates.
- Be careful with unknown sites: Don’t click suspicious links or download files from untrusted sources.
Additional References
- Mozilla Security Advisory for CVE-2022-0843
- NIST NVD CVE-2022-0843 entry
- Firefox 98 Release Notes
In Summary
Memory safety bugs like CVE-2022-0843 show how complicated and risky modern browsers can be under the hood. Even everyday browsing could be dangerous with an unpatched browser. Keeping your software updated and being aware of what these vulnerabilities mean is your best defense.
Timeline
Published on: 12/22/2022 20:15:00 UTC
Last modified on: 12/29/2022 18:50:00 UTC