An attacker can exploit this vulnerability by accessing a specially crafted file system to cause information leak leading to arbitrary code execution.
and 2 other vulnerabilities have been reported in linux kernel. CVE-2017-7556: A flaw was found in the Linux kernel that there is a race between the verificaition code and the data processing when handling received packets. A remote user can exploit this flaw to cause a denial of service.
CVE-2017-7889: A race condition between inactivation of an inet socket when exiting a socket call and the verification of the socket's status by the kernel could result in a denial of service.
CVE-2017-7789 (Red Hat Bug #2213882): A flaw was found in the Linux kernel's handling of user-mode set memory regions to be shared between read-only data and set data. A privileged user inside a container could use this flaw to access or modify data they should not have access to.
CVE-2017-7888 (Red Hat Bug #2213521): A flaw was found in the Linux kernel where, if "top" process is active on the last non-signaling kernel thread, then kernel could join the top process on the same kernel thread in the condition of high CPU usage.
CVE-2017-7889: A race condition between inactivation of an inet socket when exiting a socket call and the verification of the socket's status by the kernel could result in
References ! -https://www.sophos.com/en-uk/knowledgebase/113618.aspx
Linux kernel version details
Linux kernel version 4.12.0-52
Ubuntu 14.04 LTS
Red Hat Enterprise Linux 7.4
Debian 8.4
How to Fix Linux Kernel – CVE-2017-7889
The following steps will help you fix the vulnerability:
1. Update your operating system
2. Update your kernel to the latest versions
3. Restart your machine
Timeline
Published on: 08/29/2022 15:15:00 UTC
Last modified on: 09/06/2022 14:37:00 UTC
References
- https://syzkaller.appspot.com/bug?id=78e9ad0e6952a3ca16e8234724b2fa92d041b9b8
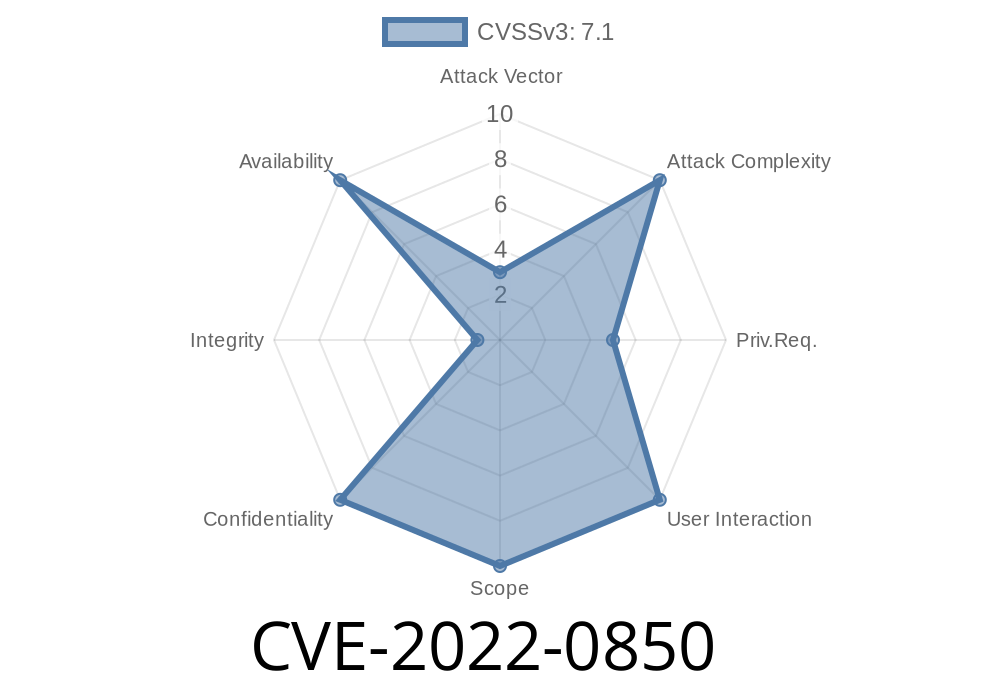
- https://access.redhat.com/security/cve/CVE-2022-0850
- https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=ce3aba43599f0b50adbebff133df8d08a3d5fffe
- https://bugzilla.redhat.com/show_bug.cgi?id=2060606
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-0850