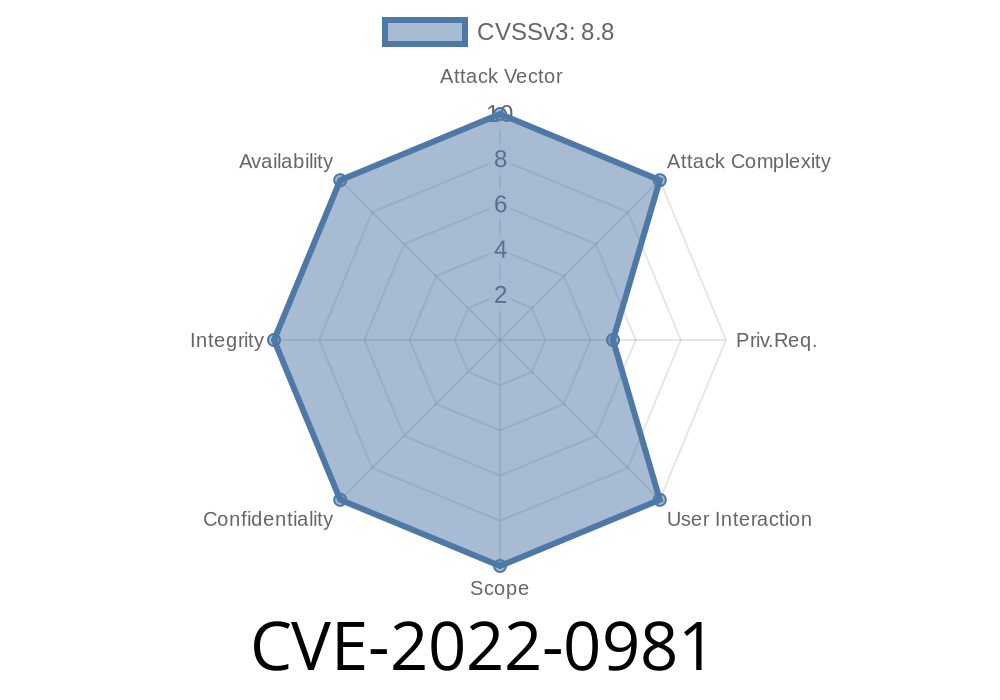
This issue could be exploited remotely by injecting malicious requests into the application’s communication channels. In certain configurations, it’s also possible for an authenticated low-privilege user to escalate their privileges to a higher-level role.
To learn more about this vulnerability and download the CVE number, check out the Quarkus security advisory.
Quarkus is an Open Source content management system that’s licensed under the GNU Affero General Public License (AGPL).
Quarkus was found to have a Cross-Site Request Forgery (CSRF) vulnerability. An attacker could exploit this weakness by sending a malicious request from the victim’s browser to the application’s server. An attacker could make this type of request look like a legitimate request sent by the user.
Summary of Quarkus Security Advisory
An attacker could misuse the Cross-Site Request Forgery (CSRF) vulnerability in the Quarkus Apache2 module.
Quarkus is an open source Content Management System under the GNU Affero General Public License (AGPL). Quarkus was found to have a CSRF vulnerability that could be exploited by malicious requests sent from a victim's browser to the application's server.
Timeline
Published on: 03/23/2022 20:15:00 UTC
Last modified on: 03/29/2022 18:02:00 UTC