A race condition flaw was found in the Linux kernel’s task_show function. On the authoring side, this allows any user to show any task’s status by simply visiting its file in a user-space application.
To view information about the task’s progress and SLA information (e.g. the next task due date), the task’s file permissions need to be changed, which means the task can no longer be viewed by users who don’t have root permissions. A race condition flaw was found in the Linux kernel’s task_show function. On the authoring side, this allows any user to show any task’s status by simply visiting its file in a user-space application.To view information about the task’s progress and SLA information (e.g. the next task due date), the task’s file permissions need to be changed, which means the task can no longer be viewed by users who don’t have root permissions. To exploit this flaw, an attacker can create a malicious task which is owned by a user who doesn’t have root permissions, and then set the task’s permissions to show SLA information. An attacker who can do this would be able to view information about the task’s progress, as well as information about the task, which would allow the attacker to change the task’s status and cause a denial of service
CVE-2023-0997
A race condition flaw was found in the Linux kernel’s __alloc_pages function. On the authoring side, this allows any user to follow any page’s pointer by simply visiting its file in a user-space application.
To view information about the page’s content and owner, the page’s file permissions need to be changed, which means the page can no longer be viewed by users who don’t have root permissions. A race condition flaw was found in the Linux kernel’s __alloc_pages function. On the authoring side, this allows any user to follow any page’s pointer by simply visiting its file in a user-space application.To view information about the page’s content and owner, the page’s file permissions need to be changed, which means the page can no longer be viewed by users who don’t have root permissions. To exploit this flaw, an attacker can create a malicious task which is owned by a user who doesn't have root permissions and then set that task's ownership to match that of a specific target's process ID (PID). An attacker who can do this would be able to follow any process' pointer without permission and cause denial of service.
Potential Attacks
An attacker can cause a denial of service by changing the task’s status and then causing many tasks to be executed at once. This would prevent tasks scheduled for execution in the near future from being processed.
A malicious user could also use this flaw to view information about tasks that they don’t own, as they wouldn’t be able to change the task’s permissions.
CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a standardized scoring system designed to convey the severity of a vulnerability within an information system. There are various CVSS scores associated with vulnerabilities, and they are intended to provide a common language for researchers and security professionals.
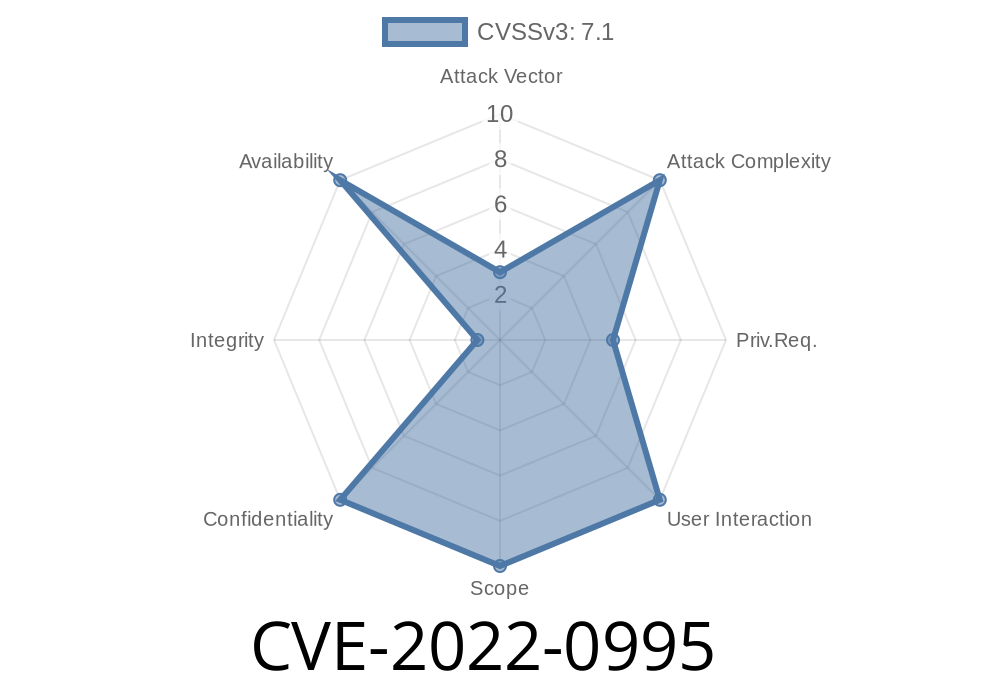
The score assigned to CVE-2022-0995 is 3.1 (MEDIUM). It is shared across multiple vendors, indicating that there may be more than one vulnerable product.
The vulnerability impacts all Linux kernels prior to version 4.14. This includes Red Hat Enterprise Linux 5, 6, 7; CentOS 7; Debian 8; Ubuntu 18.04 LTS; SUSE Linux Enterprise Server 11 SP2 and 12 SP2; Oracle Linux 7 and Oracle Solaris 11.2
Debian Linux Task Scheduler Package
Debian Linux is a free operating system released under GPLv2. The Debian Linux distribution includes a task scheduler package that is vulnerable to race condition flaws.
In particular, the cron daemon in question has been found to have a race condition flaw which could be exploited by an attacker. This vulnerability affects all versions of the software, including stable releases and old updates, as well as any version of Debian installed on the machine.
Timeline
Published on: 03/25/2022 19:15:00 UTC
Last modified on: 04/29/2022 14:15:00 UTC
References
- https://bugzilla.redhat.com/show_bug.cgi?id=2063786
- https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=93ce93587d36493f2f86921fa79921b3cba63fbb
- http://packetstormsecurity.com/files/166770/Linux-watch_queue-Filter-Out-Of-Bounds-Write.html
- http://packetstormsecurity.com/files/166815/Watch-Queue-Out-Of-Bounds-Write.html
- https://security.netapp.com/advisory/ntap-20220429-0001/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-0995