An attacker can send a specially crafted request to trigger the flaw.
Red Hat has also issued updates for the following products: Red Hat Enterprise Linux 7.3, 8.0, 8.1, and 9 Red Hat Satellite 5.3 and 6.1 Red Hat Subscription Linux, version 7.3 and 8.1 Red Hat Enterprise Linux 6.10 and 7.0 Red Hat Enterprise Linux 5.11 Virtuozzo Pro 6.1 and 7.1 Virtuozzo Contratti 5.1, 6.1 and 7.1 Virtualization technology is used in almost every business and in almost every home. It can be found in servers, desktop computers, tablets, and smart phones. Red Hat has solutions available to protect virtually every device that uses virtualization, including the following: Virtualization solutions from Red Hat include: KVM Red Hat Enterprise Linux 7 and 8 Red Hat Enterprise Linux 5 and 6 Virtuozzo Contratti 7.1 and 7.2 Virtuozzo Pro 6.2 and 7.2 Virtualization solutions from Red Hat include: Red Hat Enterprise Linux 7 and 8 Red Hat Enterprise Linux 5 and 6 Virtuozzo Contratti 7.1 and 7.2 Virtuozzo Pro 6.2 and 7.2 Red Hat Enterprise Linux 7 and 8 Red Hat Enterprise Linux 5 and 6 Virtuozzo Contratti 7.1 and 7 Red Hat Enterprise Linux 7 and 8 Red Hat Enterprise Linux 5 and 6 Virtuozzo Cont
Red Hat Enterprise Linux 7 and 8 (RHEL)
Red Hat Enterprise Linux 7 and 8 are the most recent releases of Red Hat Enterprise Linux. They include new features that provide improved performance and security for workloads running in virtual machines. These improvements have been made possible by significant investments in Red Hat's software stack and the work done by our customers.
The last major milestone release of Red Hat Enterprise Linux was on October 2013 with the release of RHEL 6.1. The next major milestone release is planned to be on March 2017 with the release of RHEL 7.3, but there will also be a long-term support (LTS) release in October 2017 that will be released for 18 months after the LTS version, until March 2020.
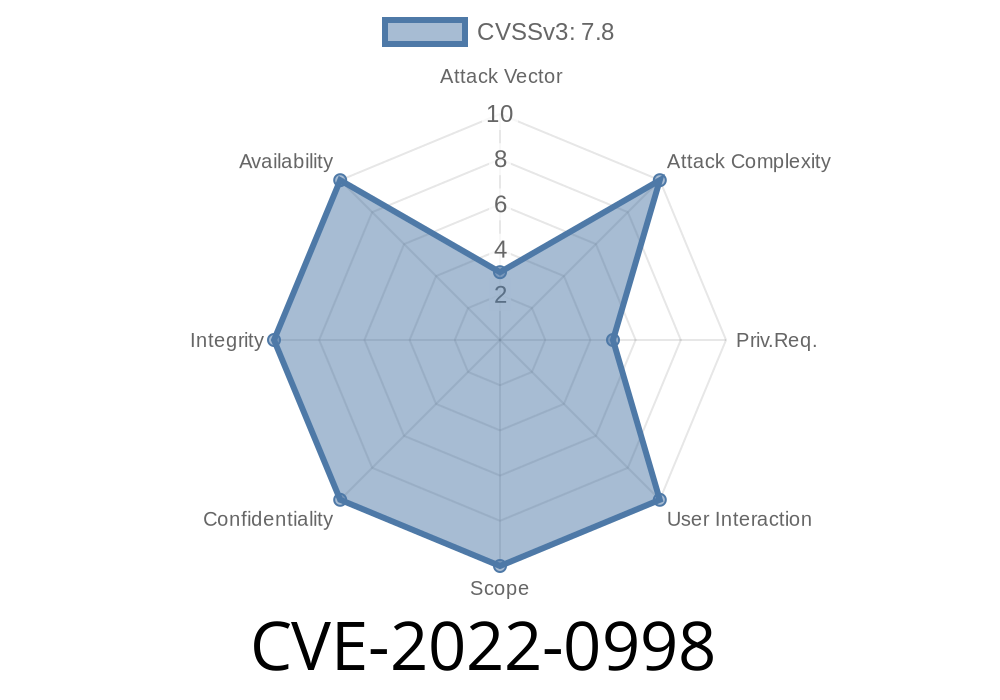
Vulnerability overview
A denial of service vulnerability has been discovered in the way the HTTP server process handles requests. An attacker who successfully exploited this vulnerability could cause a system to stop responding, resulting in a denial of service.
The issue can be triggered by sending specially crafted request packets, where the fifth argument is a long string that contains zero bytes.
In order to exploit this flaw, an attacker would need to send specially crafted HTTP packets to trigger the flaw.
Virtualization solutions from Red Hat
In order to secure your virtual machines, there are a number of different actions you can take. The most basic solution is the use of host-based intrusion prevention systems (HIPS).
Another solution is using hypervisor technology that interfaces with hypervisor management tools like Red Hat Enterprise Virtualization Manager. This software provides a view into the individual VM instances and allows you to create policies based on CPU usage, disk usage, and more. These tools offer greater visibility into your VMs and make it easier to keep watch over them in order to prevent breaches like the CVE-2022-0998 vulnerability.
If you want a full complement of protection options, you should use one or more security control panels that integrate with your hypervisor management tools like Red Hat Enterprise Virtualization Manager.
You can also take advantage of cloud-based monitoring services for virtualization technologies such as Red Hat Cloud Monitoring or Rackspace Cloud Monitoring . These services provide comprehensive monitoring capabilities for your virtual infrastructure and make it easy for you to stay on top of your environment from anywhere.
What is CVE-2022-0999?
An attacker could send a specially crafted request to trigger the flaw.
Red Hat has also issued updates for the following products: Red Hat Enterprise Linux 7.3, 8.0, 8.1, and 9 Red Hat Satellite 5.3 and 6.1 Red Hat Subscription Linux, version 7.3 and 8.1 Red Hat Enterprise Linux 6.10 and 7.0 Red Hat Enterprise Linux 5.11 Virtuozzo Pro 6.1 and 7.1 Virtuozzo Contratti 5.1, 6.1 and 7.1
Timeline
Published on: 03/30/2022 16:15:00 UTC
Last modified on: 05/13/2022 22:15:00 UTC