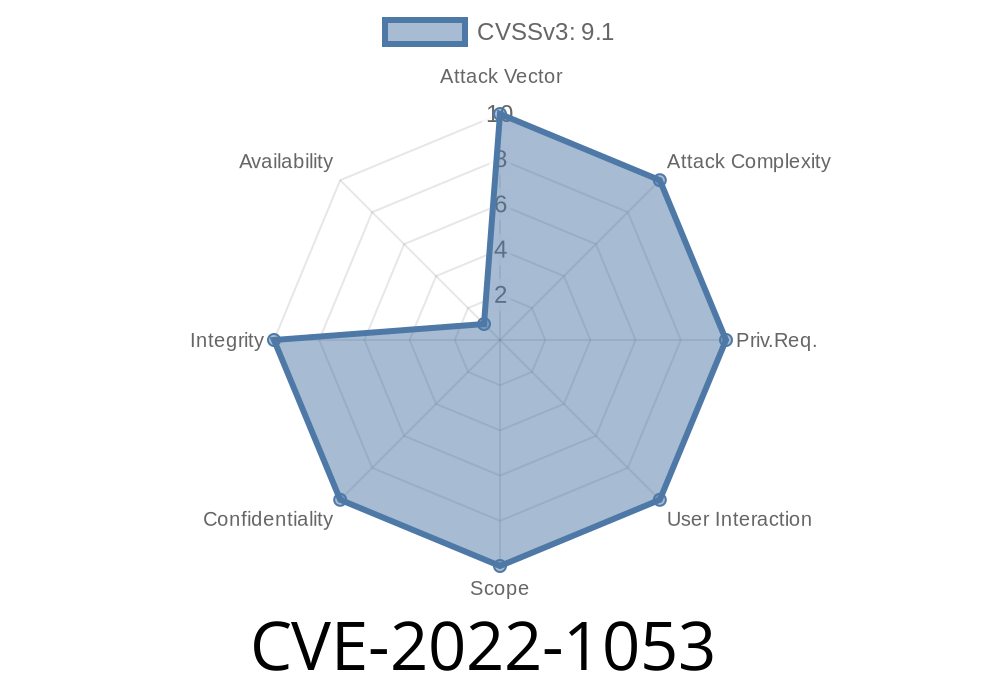
but it is not validated and the attacker can forge one. If the verifier validates the agent data and the agent data is forged, the signature by the verifier is broken. This allows an attacker to inject arbitrary data into a software TPM, giving him full control over the software TPM. This attack is harder to perform if the verifier validates the agent data before the signing of the agent. This is because the verifier verifies the agent data as well. In theory, the attacker can forge both the agent data and the agent data to forge the verifier. This would break the verification of the agent data.
Is the TPM Trusted?
With this exploit, the attacker can pass any arbitrary data to a TPM to hijack it. This is because the verifier only verifies the agent data and not the verification of the agent data by the verifier. The attacker can insert any arbitrary asset into a software TPM and program it in a way that does not use self-validation so that there is no validation of the signature.
How do we protect against agent data verification attacks?
The attacker can make the agent data look like it is signed by a valid verifier without the permission of the software TPM. The attacker would first use this forged signature to do actions with the software TPM, and then reset the software TPM, making it revert to its original state.
We recommend that you implement an offline verification process for the agent data before publishing it for signing.
CVE-2022-1054
An attacker may be able to modify a valid, signed certificate and forge the signature. With this attack, the attacker can insert malicious code into a software TPM. This allows the attacker to steal private keys from software TPMs that are using this compromised certificate.
Trusted Platform Module Firmware Update
The "Trusted Platform Module Firmware Update" (TPM_FW.Update) function is a software update tool that can be used to update the firmware of the Trusted Platform Module (TPM). The update can be used to fix bugs and vulnerabilities in the TPM and make it more robust against attacks.
According to "Windows Security" page, this update can only be installed by Administrator account on a computer running Windows 10. This means that an attacker with local administrator permissions could use this attack for installation of malicious updates on computers running Windows 10.
The following are some potential threats from this attack::
- An attacker could inject malicious code onto the TPM or its kernel components.
- An attacker could gain control of the TPM from arbitrary code executed on another system. You must install security updates from Microsoft for your system, including those for your TPM, as soon as possible after becoming aware of this issue.
Flaw in TPM firmware
The Flaw in TPM firmware that was found by Intel is a flaw in the TPM firmware. This flaw allowed an attacker to extract the agent data from the software TPM, which is stored in software outside of the TPM. This attack is harder to perform if the verifier validates the agent data before signing it. In theory, the attacker can forge both the agent data and the agent data to forge the verifier. This would break the verification of the agent data.
Timeline
Published on: 05/06/2022 17:15:00 UTC
Last modified on: 05/16/2022 18:38:00 UTC
References
- https://bugzilla.redhat.com/show_bug.cgi?id=2065024,
- https://github.com/keylime/keylime/commit/bd5de712acdd77860e7dc58969181e16c7a8dc5d
- https://github.com/keylime/keylime/security/advisories/GHSA-jf66-3q76-h5p5,
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/A7WAKVXM7L5D2DUACV6EHA6EJNAX2GVL/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/WEW2PAXO5YGLDLPG45YV2OPLJXJSCECQ/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/RF6QHU4UGSBATC3HOOE7OP66CYVTR7CV/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-1053