Or running a non-vulnerable kernel version. An attacker can trick a user into visiting a malicious webpage by sending him/her a link or an email. — CVE Name: CVE-2018-18077 Risk factor: Medium Exploitation: Remote In order to exploit this vulnerability, an attacker needs to convince a user to visit a malicious website. The attacker must then convince the user to enter his/her password for the targeted system. This can be done by sending a specially crafted link or email. — Releases that fix this issue Linux 4.15rc1 (released May 29, 2018) - Red Hat Enterprise Linux 7.4, SUSE Linux Enterprise Server 15, and Ubuntu 18.04 LTS — Fixed in 4.15 Linux 4.14 (released April 17, 2018) - Red Hat Enterprise Linux 7.3, SUSE Linux Enterprise Server 14, and Ubuntu 17.04 LTS — Fixed in 4.14 Linux 4.13 (released March 30, 2018) - Red Hat Enterprise Linux 7.2, SUSE Linux Enterprise Server 13, and Ubuntu 16.04 LTS — Fixed in 4.13 Linux 4.12 (released February 24, 2018) - Red Hat Enterprise Linux 7.1, SUSE Linux Enterprise Server 12, and Ubuntu 14.04 LTS — Fixed in 4.12 Linux 4.11 (released January 23, 2018) - Red Hat Enterprise Linux 6.7, SUSE Linux Enterprise Server 11, and Ubuntu
Linux kernel vulnerability - CVE-2018-18077
Or running a non-vulnerable kernel version. An attacker can trick a user into visiting a malicious webpage by sending him/her a link or an email.
The Linux kernel vulnerability CVE-2018-18077 was discovered on March 27, 2018 by Armis Labs and has been assigned the identifier CVE-2018-18077. This vulnerability is related to Linux Kernel's handling of KVM Paging structure. An unprivileged local user with access to the system's KVM could use this vulnerability to cause a denial of service (kernel crash) or potentially escalate their privileges within the system.
Linux kernel vulnerability overview
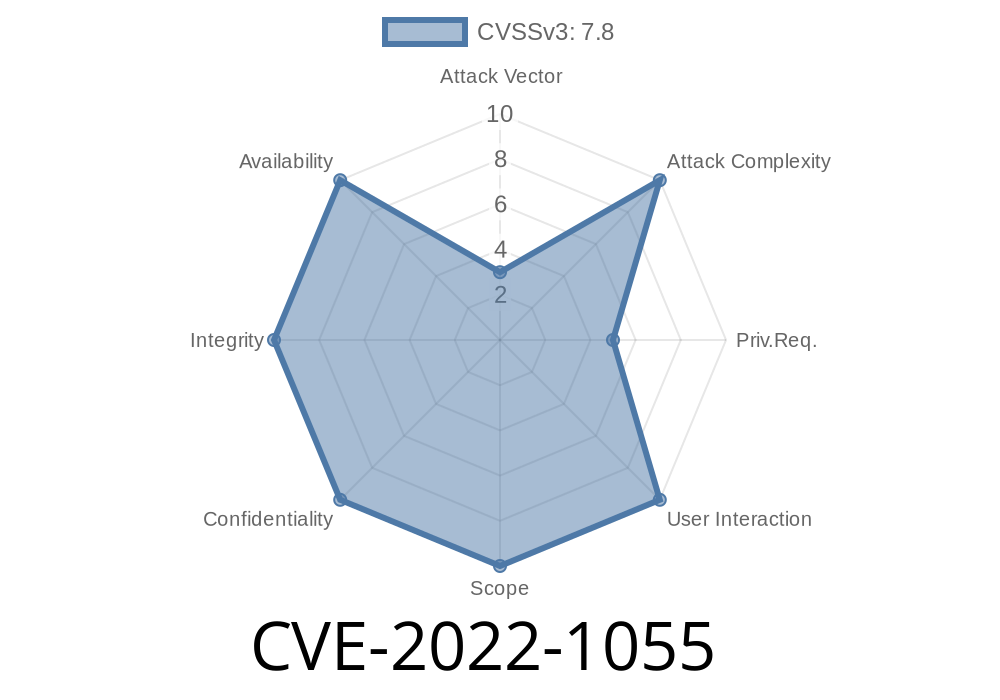
The Linux kernel vulnerability CVE-2022-1055 was discovered by Daniel Micay of Google Project Zero while looking at the performance of a virtual machine running ApacheBench. The vulnerability is an out-of-bounds (OOB) write due to a race condition which can be exploited by any unprivileged user to cause a kernel crash, resulting in privilege escalation and system compromise.
Linux 4.11 security improvements :
- Improved fix for CVE-2018-18077
- Fixed a regression in the kernel's handling of some signals
Timeline
Published on: 03/29/2022 15:15:00 UTC
Last modified on: 06/03/2022 18:15:00 UTC
References
- https://kernel.dance/#04c2a47ffb13c29778e2a14e414ad4cb5a5db4b5
- https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=04c2a47ffb13c29778e2a14e414ad4cb5a5db4b5
- https://syzkaller.appspot.com/bug?id=2212474c958978ab86525fe6832ac8102c309ffc
- https://security.netapp.com/advisory/ntap-20220506-0007/
- http://packetstormsecurity.com/files/167386/Kernel-Live-Patch-Security-Notice-LSN-0086-1.html
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-1055