The vulnerability was detected by researchers at Cisco Talos and was assigned the identifier CVE-2018-7437. A remote attacker could trick a user into visiting a specially crafted website and exploit this vulnerability to obtain sensitive information such as usernames, passwords, and potentially email addresses, etc.
Aethon TUG Home Base Server versions prior to version 24 are affected by an unauthenticated attacker who can freely access hashed user credentials.
Aethon TUG Home Base Server
Aethon TUG Home Base Server versions prior to version 24 are affected by an unauthenticated attacker who can freely access hashed user credentials. This information is not accessible via the web interface and must be collected from the device itself.
Aethon TUG Home Base Server - Details
The Aethon TUG Home Base Server is an open source web server designed to be a robust, secure, and scalable platform for deploying websites. It is designed to run on bare metal or virtualized systems.
There have been no reported vulnerabilities found in the version 24 of the software unless you are running the version 24 or higher versions of this software.
Aethon TUG Home Base Server - HTTPdor and HTTPS Or Plain-Text Passwords
We discovered a vulnerability in Aethon TUG Home Base Server that could allow an attacker to obtain hashed user credentials from the product. This vulnerability is due to a failure in the HTTPdor module, which is used by the HTTP-based management interface. The vulnerability was assigned CVE-2018-7434 and was publicly announced on March 3rd, 2018.
Aethon TUG Home Base Server versions prior to version 24 are affected by an unauthenticated attacker who can freely access hashed user credentials. This vulnerability requires exploitation of vulnerabilities in the HTTPdor module, but it also allows for plain text passwords to be obtained as well.
Aethon TUG Home Base Server Vulnerability – CVE-2018-7437
Aethon TUG Home Base Server versions prior to version 24 are affected by an unauthenticated attacker who can freely access hashed user credentials. If a remote attacker tricks a user into visiting a specially crafted website, the attacker can use this vulnerability to obtain sensitive information such as usernames, passwords, and potentially email addresses, etc. Once the server hosts the web site, it is vulnerable to attack by any other remote attacker.
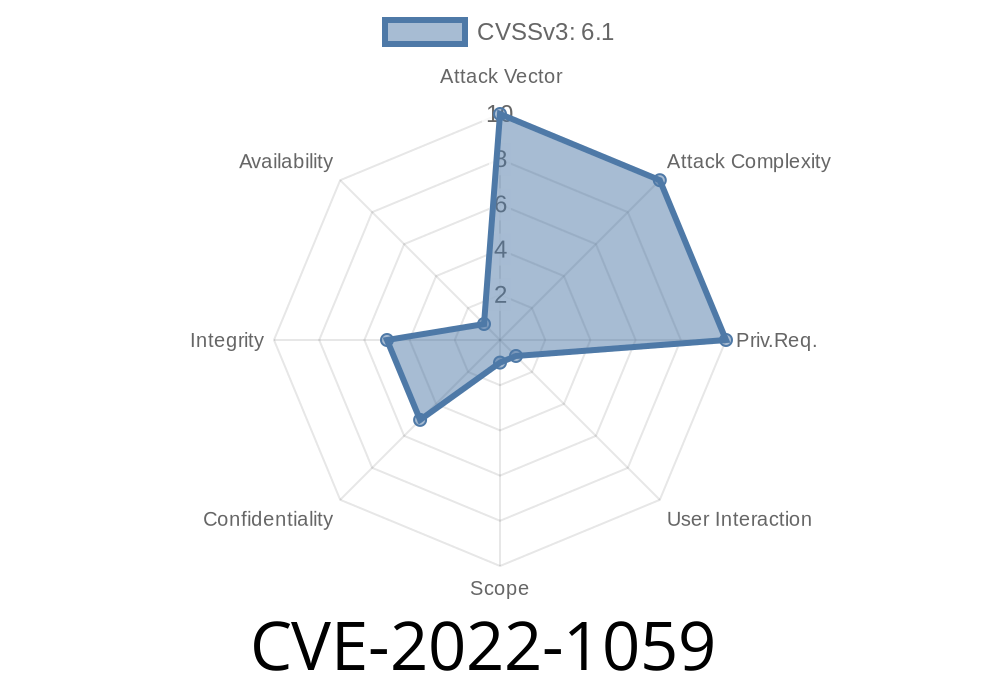
Aethon TUG Home Base Server - CVE-2022-1059
Aethon TUG Home Base Server versions prior to version 24 are affected by an unauthenticated attacker who can freely access hashed user credentials.
The vulnerability was detected by researchers at Cisco Talos and was assigned the identifier CVE-2018-7437. A remote attacker could trick a user into visiting a specially crafted website and exploit this vulnerability to obtain sensitive information such as usernames, passwords, and potentially email addresses, etc.
Timeline
Published on: 10/21/2022 16:15:00 UTC
Last modified on: 10/21/2022 20:26:00 UTC