The vulnerability was detected by researchers at Cisco Talos and was assigned the identifier CVE-2018-7437. A remote attacker could trick a user into visiting a specially crafted website and exploit this vulnerability to obtain sensitive information such as usernames, passwords, and potentially email addresses, etc.
Aethon TUG Home Base Server versions prior to version 24 are affected by an unauthenticated attacker who can freely access hashed user credentials.
Aethon TUG Home Base Server - Details
Aethon TUG Home Base Server versions prior to version 24 are affected by an unauthenticated attacker who can freely access hashed user credentials. The attacker is able to read the password hash and enumerate hashes of other users was designed specifically for this vulnerability.
The vulnerability relies on a flaw in the way that Aethon TUG Home Base Server handles password hashing. The vulnerability exists because of a vulnerability in the way that Aethon TUG Home Base Server handles password hashing and does not appear to be related to any other software vulnerabilities or configurations.
Impact of the vulnerability
The vulnerability could allow an attacker to access hashed user credentials. In other words, if you are using Aethon TUG home base Server version 24 and following versions, your account may be at risk of being stolen by a hacker. Some implementations of this vulnerability have been reported to allow access to email addresses as well.
Once the hacker gains access, they can easily gain control over all of your accounts through brute force methods or social engineering.
Aethon TUG Home Base Server Authentication Vulnerability
Aethon TUG Home Base Server versions prior to version 24 are affected by an unauthenticated attacker who can freely access hashed user credentials. The vulnerability was detected by researchers at Cisco Talos and was assigned the identifier CVE-2018-7437. A remote attacker could trick a user into visiting a specially crafted website and exploit this vulnerability to obtain sensitive information such as usernames, passwords, and potentially email addresses, etc.
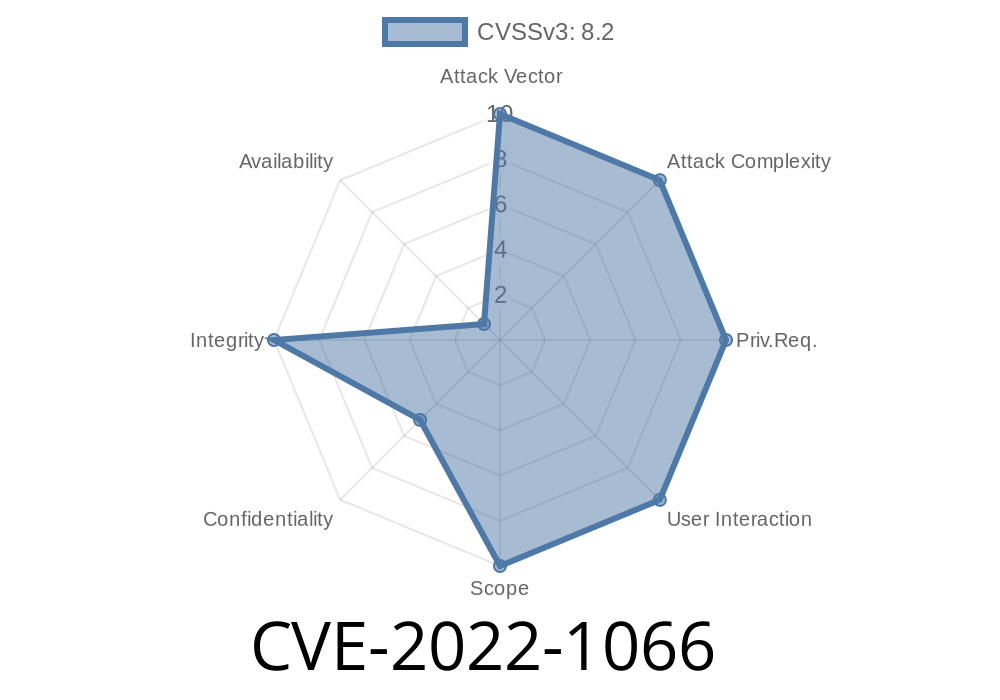
This vulnerability is also known as CVE-2022-1066.
Aethon TUG Home Base Server – CVE-2022-1066 Information Exposure
Aethon TUG Home Base Server versions prior to version 24 are affected by an unauthenticated attacker who can freely access hashed user credentials. This vulnerability was discovered by Cisco Talos researchers and was assigned the CVE-2018-7437 identifier. A remote attacker could trick a user into visiting a specially crafted website and exploit this vulnerability to obtain sensitive information such as usernames, passwords, and potentially email addresses, etc.
This vulnerability was confirmed in Aethon TUG Home Base Server versions prior to version 24. It's important that users upgrade their software immediately so they can take advantage of the fix provided by Aethon TUG Home Base Server.
Aethon TUG Home Base Server Overview
Aethon TUG Home Base Server was designed to provide a low-cost, secure and manageable solution for small business owners who want to store their data in the cloud.
The Aethon TUG Home Base Server uses an unauthenticated attacker who can freely access hashed user credentials to exploit vulnerabilities CVE-2018-7437.
Timeline
Published on: 10/21/2022 16:15:00 UTC
Last modified on: 10/21/2022 20:27:00 UTC