The vulnerability was detected by researchers at Cisco Talos and was assigned the identifier CVE-2018-7437. A remote attacker could trick a user into visiting a specially crafted website and exploit this vulnerability to obtain sensitive information such as usernames, passwords, and potentially email addresses, etc.
Aethon TUG Home Base Server versions prior to version 24 are affected by an unauthenticated attacker who can freely access hashed user credentials.
Comma-Separated Values (CSV) file upload vulnerability
CSV files are used for storing data and importing it into a spreadsheet. CSV file upload vulnerability is a vulnerability in Hadoop YARN that existed in versions 0.20.205 to 0.23.0, which could allow an attacker to potentially gain access to confidential information such as user credentials and email addresses.
Comma-separated values (CSV) files are used for storing data and importing it into a spreadsheet and is vulnerable to attack by malicious users who have the technical capability of exploiting this vulnerability on the system where the application is deployed. The attacker can also gain access to emails, usernames and passwords when sending unauthenticated request to a web server using HTTP protocol with crafted parameters in order to exploit and obtain sensitive information including emails, usernames, and passwords.
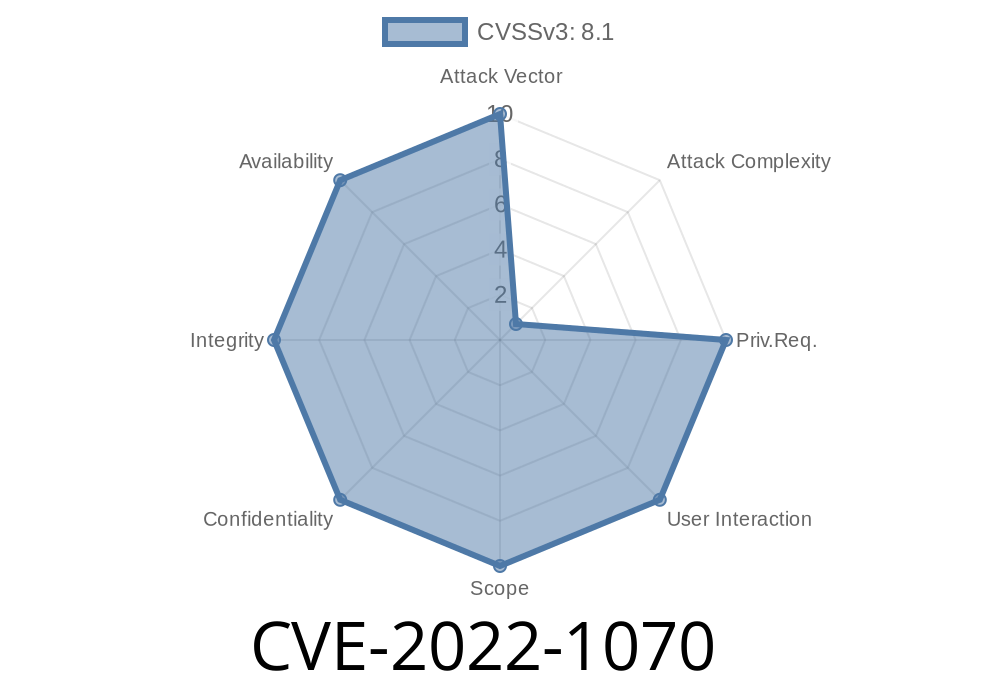
Aethon TUG Home Base Server Authentication Bypass
Aethon TUG Home Base Server versions prior to version 24 are affected by an unauthenticated attacker who can freely access hashed user credentials. This vulnerability was found in the authentication mechanism and is only triggered when a remote attacker tricks a user into visiting a specially crafted website.
Aethon TUG Home Base Server - Authentication Bypass
Aethon TUG Home Base Server versions prior to version 24 are affected by an authenticated attacker who can freely access hashed user credentials. The vulnerability exists because of a missing authentication requirement for certain types of requests. This authentication bypass allows an unauthorized third party to determine the internal IP address and port number of the TUG Home Base Server or to cause a denial-of-service condition on the TUG Home Base Server.
The vulnerability was discovered by researchers at Cisco's Talos Intelligence and Research Group.
Aethon TUG Home Base Server Vulnerability Symptoms and Detection Examples
If you are using the Aethon TUG Home Base Server for your home automation needs, you should update your current software to the latest version and ensure that your devices are always running on the most recent software.
Aethon TUG Home Base Server versions prior to version 24 are affected by an unauthenticated attacker who can freely access hashed user credentials. This vulnerability is caused by a weak hashing algorithm used in the web interface and system files of the application. If a remote attacker were to visit a malicious website, they could trick a user into visiting that site and then exploit this vulnerability to obtain sensitive information such as usernames, passwords, and potentially email addresses, etc.
Timeline
Published on: 10/21/2022 16:15:00 UTC
Last modified on: 10/21/2022 21:00:00 UTC