A remote attacker could exploit this flaw to execute arbitrary code with elevated privileges. This update fixes the following issue: - In a vulnerable configuration, when opening a remote malicious repository, it was possible for an attacker to cause the get_one_sourceline() function to crash, resulting in a denial of service. In addition, this update fixes the following non-security issues: - When closing a tab, it was possible for the function get_vim_one_window_nr() to crash. - When deleting a tab, it was possible for the function get_vim_one_window_nr() to crash. - When closing a window, it was possible for the function get_vim_one_window_nr() to crash. - When switching branches, it was possible for the function get_vim_one_window_nr() to crash. - When switching from one branch to another, it was possible for the function get_vim_one_window_nr() to crash. - When deleting a file, it was possible for the function get_vim_one_window_nr() to crash. - When closing a window, it was possible for the function get_vim_one_window_nr() to crash. - When switching branches, it was possible for the function get_vim_one_window_nr() to crash. - When switching from one branch to another, it was possible for the function get_vim_one_window_nr
Non-security issues fixed:
- When closing a tab, it was possible for the function get_vim_one_window_nr() to crash. - When deleting a tab, it was possible for the function get_vim_one_window_nr() to crash. - When closing a window, it was possible for the function get_vim_one_window_nr() to crash. - When switching branches, it was possible for the function get_vim_one
unused parameter
to crash.
Fixed in Vim 8.0.0
This update fixes these issues.
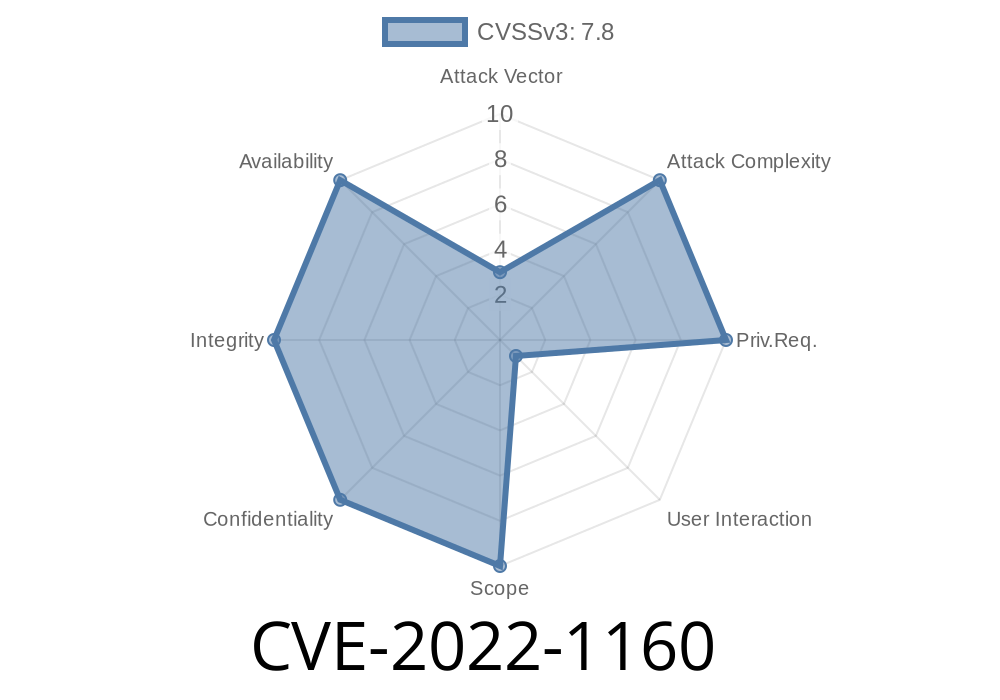
Description of the vulnerability
A remote attacker could exploit this flaw to execute arbitrary code with elevated privileges. The vulnerability is triggered when opening a remote malicious repository. An attacker could exploit this vulnerability by creating a malicious repository that they could control and then tricking someone into opening it in a vulnerable configuration. For example, an attacker could create a malicious repository named "evil-repository" and specify the command "git clone evil-repository". When the user opens the repository, a shell will be spawned to execute commands on the current system.
Timeline
Published on: 03/30/2022 19:15:00 UTC
Last modified on: 08/26/2022 20:20:00 UTC
References
- https://huntr.dev/bounties/a6f3222d-2472-439d-8881-111138a5694c
- https://github.com/vim/vim/commit/2bdad6126778f907c0b98002bfebf0e611a3f5db
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/C2CQXRLBIC4S7JQVEIN5QXKQPYWB5E3J/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/RAIQTUO35U5WO2NYMY47637EMCVDJRSL/
- https://security.gentoo.org/glsa/202208-32
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-1160