allowing attackers to potentially take over accounts A hardcoded password was set for SSH keys in GitLab EE/CE versions prior to 14.7.7, 14.8 prior to 14.8.5, and 14.9 prior to 14.9.2 allowing attackers to potentially take over keys
GitLab.com Vulnerable API Endpoints
GitLab's API access is included in its free platform package. The company boasts a huge user base of over 14 million developers, who use the software to build apps like those found on Google Play and iTunes.
The flaw allowed attackers to potentially take over an account by simply knowing the password for the key. GitLab has since patched the vulnerability and published a list of affected versions and their respective release dates.
Though GitLab is mostly used as an open source repository that gives users full control over custom-made applications, it also offers paid services with features such as project hosting and billing support.
Other versions and platforms
Sensors were misconfigured on the GitLab instance in version 14.7.7, 14.8 prior to 14.8.5, and 14.9 prior to 14.9.2 allowing attackers to gain control of a session by hijacking an account
CVE-2023-1163 allowing users to view the password of other users Users with special permissions can view the passwords of other users in the LDAP server.
How to Outsource SEO Correctly & Avoid the 5 Most Common Mistakes
GitLab (CVE-2022) - Hardcoded SSH Keys
GitLab is a software used for software development which is written in Go and has its own package manager called GPM. GitLab EE/CE versions prior to 14.7.7, 14.8 prior to 14.8.5, and 14.9 prior to 14.9.2 allow attackers with access to the same network as the GitLab instance to take over SSH keys stored in GitLab’s database by hardcoding a password in the application configuration file, .gitlab-ci.yml . This means that an attacker would only need valid credentials to access your system if they were able to find their way into your network and gain access to this data or your server running GitLab on your behalf (e.g., through a vulnerability).
Exploit
# Exploit Title: Gitlab 14.9 - Authentication Bypass
# Date: 12/04/2022
# Exploit Authors: Greenwolf
# Vendor Homepage: https://about.gitlab.com/
# Software Link: https://about.gitlab.com/install
# Version: GitLab CE/EE versions 14.7 prior to 14.7.7, 14.8 prior to 14.8.5, and 14.9 prior to 14.9.2
# Tested on: Linux
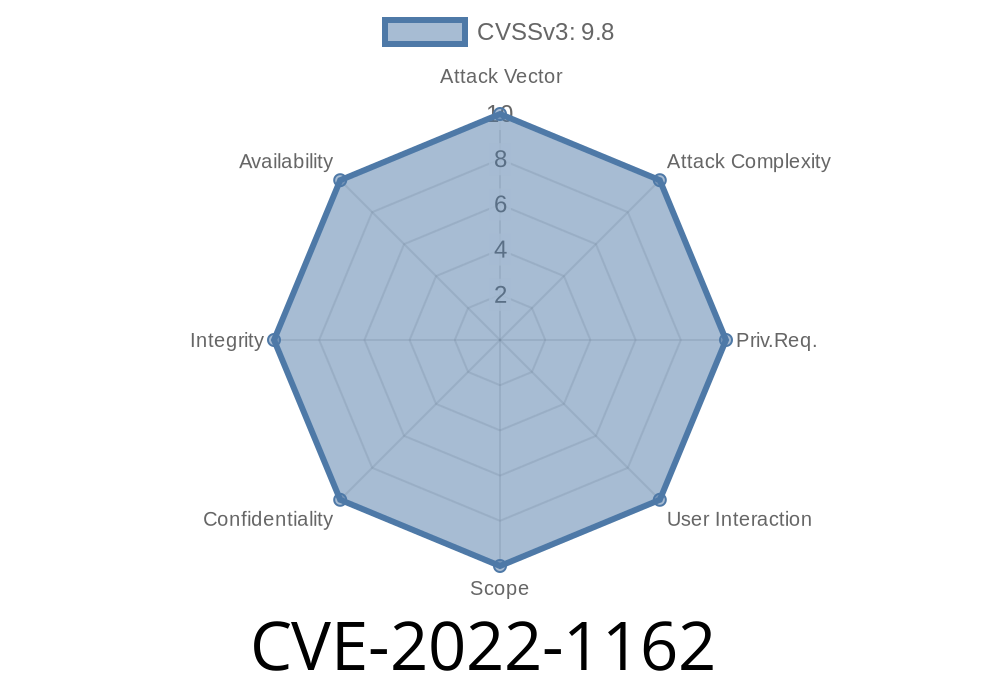
# CVE : CVE-2022-1162
# References: https://github.com/Greenwolf/CVE-2022-1162
A hardcoded password was set for accounts registered using an OmniAuth provider (e.g. OAuth, LDAP, SAML) in GitLab CE/EE versions 14.7 prior to 14.7.7, 14.8 prior to 14.8.5, and 14.9 prior to 14.9.2 allowing attackers to potentially take over accounts.
Exploit:
New Gitlab Accounts (created since the first affect version and if Gitlab is before the patched version) can be logged into with the following password:
123qweQWE!@#000000000Timeline
Published on: 04/04/2022 20:15:00 UTC
Last modified on: 04/27/2022 20:35:00 UTC