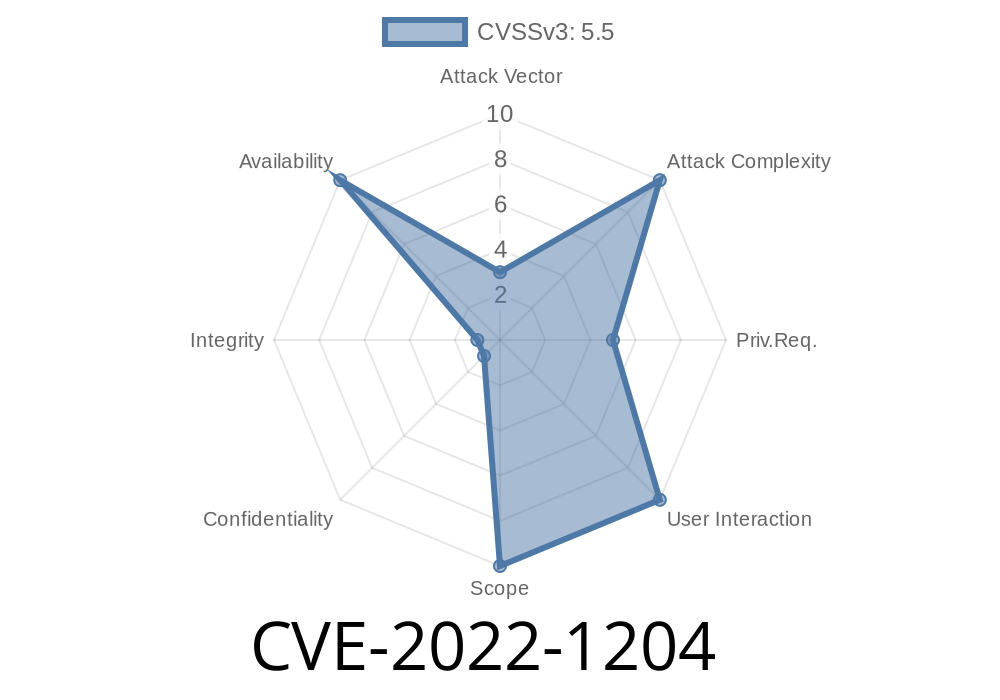
This issue occurs due to a race condition in the user connection code when handling packets. As a result, a user with access to a local device could cause a system crash. It’s recommended upgrading to a later version of the Linux kernel.
It was discovered that the ext4 filesystem implementation in the Linux kernel did not properly validate block group descriptor entries. An attacker could use this flaw to corrupt filesystem data, possibly resulting in denial of service.
It was found that the Linux kernel’s implementation of the ext4 filesystem did not properly validate the length of inode entries when handling ext4 filesystem images other than jbd2. An attacker could use this flaw to cause a denial of service when using ext4 filesystems on root file systems running with an unsecure policy.
A race condition flaw was found in the way the Linux kernel’s virtual memory implementation handled trylock() and clone() calls in the vhost-net module. A local user could use this flaw to crash the system or, potentially, escalate their privileges on the system.
It was found that the Linux kernel’s memory resource controller could consume all available memory on a system, causing a denial of service on the system.
An information leak flaw was found in the Linux kernel’s software virtualization support. If an attacker using this virtualization technology installed a custom, user-mode application, other users could potentially read that application’s memory
Booting the Linux Kernel with UEFI Firmware
The Linux kernel can be booted with UEFI firmware to access advanced features such as the Trusted Platform Module (TPM) and Platform Security Controller (PSC).
It’s possible for an attacker to exploit a race condition in the user-connection code when handling packets. As a result, a local user could cause a system crash. It’s recommended upgrading to a later version of the Linux kernel.
QEMU:
Quick Emulator for Unmodified Kernels
There is a new and emerging concept in IT that is quickly gaining momentum as the adoption of virtualization grows:
virtualizing unmodified kernels.
It's called "Quick Emulator for Unmodified Kernels" (QEMU) and it works by loading the guest kernel, which is running in a virtual machine, with an unmodified system memory image from the host. Anything that happens to the guest OS after that point is up to the application. If a bug happens, we can just roll back to a known good state - because they're live on an unmodified kernel.
Timeline
Published on: 08/29/2022 15:15:00 UTC
Last modified on: 09/02/2022 19:41:00 UTC