This issue affects e2fsprogs versions 1.40 to 1.46.4. Red Hat Enterprise Linux and CentOS 7 users are advised to upgrade to a patched version. e2fsck might also be useful for recovering from this issue. Details about this issue are provided in the Red Hat advisory. Out of bound reads in e2fsprogs are dangerous, as they can lead to arbitrary code execution. This can be achieved via a specially crafted filesystem, which will be covered in the next section. Fortunately, a quick fix is available. Users of Red Hat Enterprise Linux 7 can update to patched e2fsprogs version 1.46.5 via the Red Hat Network.
A vulnerable filesystem example
An example of a vulnerable disk layout is shown below.
+-----+ | root | | / | +-----+
| /home1 |
| /home2 |
+-----+
| /tmp/portage-stable-v5.1.0_p1-x86_64/root | +-----+
| /tmp/portage-stable-v5.1.0_p1-x86_64/bin |
| /tmp/portage-stable-v5.1.0_p1-x86_64/sbin |
| /tmp/portage-stable-v5.1.0_p1-x86_64/libexec |
| /tmp/portage-stable-v5.1.0_p1-x86_64/etc |
| /tmp/portage-stable-v5.1.0_p1-x86_64/bootstrap*.* |
+-----+ > ffffffff80000000:ffffffffbdd3d000 ffffffff80000000:ffffffffbf7d5000 ffffffff829f9c88:fefefe7f89e0000 ffffffff83bceff:ffadeeffa090000 ffffffff83bcefc:fea6eef87010000
Custom Filesystem
The issue lies in the e2fsprogs binary, which is responsible for managing ext2/3/4 filesystems. The bug can be triggered by creating a specially crafted filesystem and mounting it with fuzzed offsets. There are many other options for exploiting this issue as well.
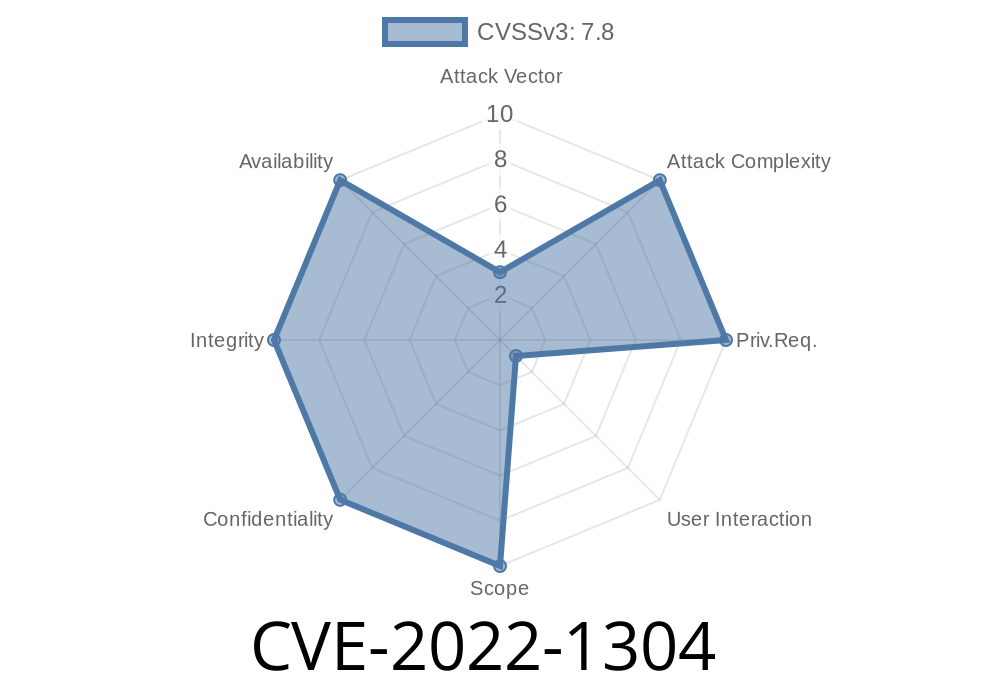
For example, there is also an OOB write flaw (CVE-2022-1304) that can lead to arbitrary code execution on kernel 4.14.0-24 or greater if you give it sufficient permissions via a specially crafted block device. This bug was fixed in Red Hat Enterprise Linux 7 with the update to version 3.10 or later of the kernel package.
E2fsprogs Issues
Versions of e2fsprogs before 1.46.5 do not properly enforce a read count limit on the number of bytes that are allowed to be read from a file descriptor in a single call; this could allow an attacker to cause arbitrary code execution by making many small calls to functions within the e2fsck program, for example.
Dissecting an out-of-bound read issue in e2fsprogs
An out-of-bound read issue in e2fsprogs is an error caused by reading beyond the end of a buffer or when memory that should not be touched is accessed. These errors can lead to arbitrary code execution if the attacker can control where to put that code.
This issue affects e2fsprogs versions 1.40 to 1.46.4, which are shipped with Red Hat Enterprise Linux 7 and CentOS 7 and below.
Timeline
Published on: 04/14/2022 21:15:00 UTC
Last modified on: 04/21/2022 15:36:00 UTC