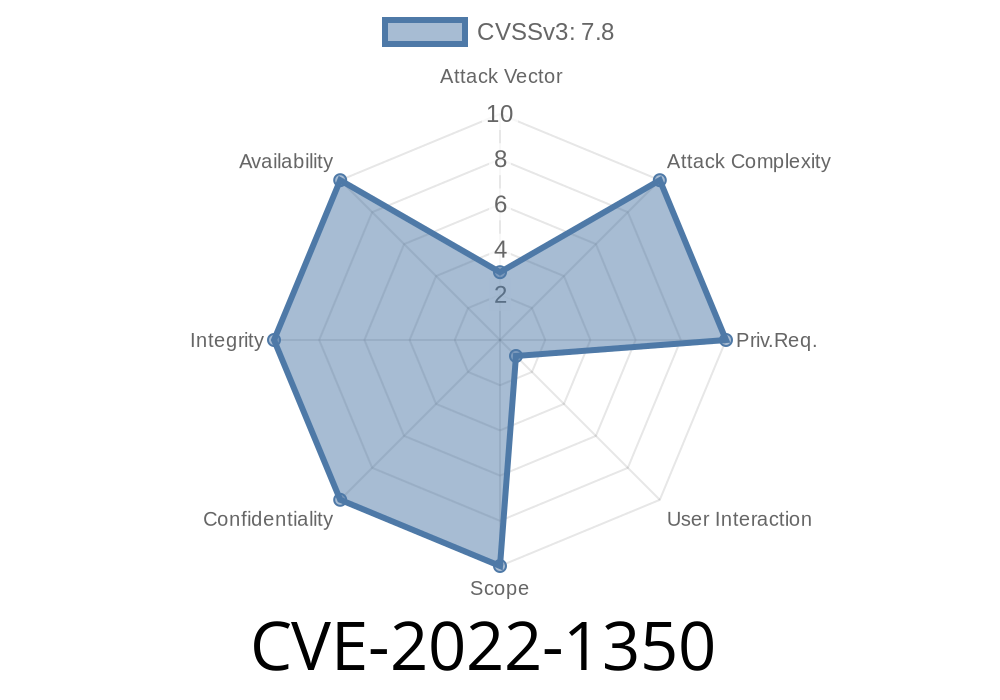
A new vulnerability (CVE-2022-1350) classified as problematic has been discovered in GhostPCL, version 9.55.. The GhostPCL library, part of the Ghostscript suite, is an open-source tool for converting PostScript and PDF files into common raster image formats. This vulnerability affects the chunk_free_object function in the gsmchunk.c file and can lead to memory corruption. The attack can be initiated remotely but requires user interaction with a malicious file. A Proof of Concept (POC) exploit has been disclosed to the public and may be used, making it crucial to apply patches to fix this issue.
Code Snippet
The affected function, chunk_free_object, is meant to free a chunk of memory in GhostPCL. The vulnerability occurs in this specific code snippet within the gsmchunk.c file:
void
chunk_free_object(gs_memory_t *mem, void *data, gs_memory_type_ptr_t pstype)
{
gs_memory_chunk_t *cmc = (gs_memory_chunk_t *)mem;
chunk_locator_t cl;
/* ... */
cl.cp = data;
if (data != )
CLEAR_FREE_OBJECT(mem, data, pstype);
// ... Additional code ...
}
Exploit Details
Attackers exploiting this vulnerability leverage a specifically crafted file that, when processed by an unsuspecting user, leads to memory corruption. By manipulating this file, attackers can potentially execute arbitrary code or cause a Denial of Service (DoS) attack on the targeted system.
The exploit POC released to the public demonstrates how an attacker can create a malicious file to trigger the memory corruption. While the POC does not show a full weaponization of the exploit, it does highlight the need to address this issue urgently.
Mitigation Steps
To protect against this vulnerability (CVE-2022-1350), it is recommended to apply the available patch provided by the Ghostscript developers. The patch can be found at the following link:
- Ghostscript Patches
It is crucial to keep the Ghostscript suite and GhostPCL up to date to minimize any potential risks. Always be cautious when opening files from unknown sources and ensure that your system is protected with the latest security patches and updates.
Conclusion
The CVE-2022-1350 memory corruption vulnerability in GhostPCL 9.55. poses a risk to users and systems that need to process PostScript and PDF files with the affected library. As always, it is essential to keep software up to date by applying security patches as they become available. By staying informed about this issue and taking appropriate mitigation steps, users can limit the potential impact of this vulnerability on their systems.
Timeline
Published on: 04/14/2022 07:15:00 UTC
Last modified on: 04/23/2022 02:20:00 UTC