This issue affects the Red Hat Enterprise Linux 5 and 6 kernels as well as the Debian 6 and 7 kernels. Red Hat has provided a patch to fix this issue.
It was discovered that the Linux kernel did not handle user-space requested maps of more than 2^31 elements correctly. A local attacker could use this flaw to crash the system or possibly escalate their privileges on affected systems.
Another flaw was found in the Linux kernel’s handling of symbolic address connections when using a VLAN interface. A remote attacker could use this flaw to crash a system on an affected network by transmitting a specially crafted packet.
It was discovered that the procfs file system created by the Linux kernel did not correctly handle race condition when checking the permissions for a process. This could lead to information leak or privilege escalation.
It was found that the Linux kernel’s ptrace implementation allowed user access to ptrace system calls, allowing privilege escalation.
It was discovered that the XFS file system implementation in the Linux kernel did not correctly handle under-length file names when using the extents feature. A local user with the ability to mount a file system can use this flaw to crash the system to gain access to data.
It was discovered that the Linux kernel did not correctly handle invalid lengths for file names when using the ext4 file system
CVE-2021-1352
This issue affects the Linux kernel as well as the Debian version of this system.
It was discovered that the btrfs file system implementation in the Linux kernel did not handle certain errors correctly. A local user with permission to mount a btrfs file system could use this flaw to cause a denial of service or escalate their privileges on the system.
Check disk for hard disk drive (HDD) defects
This issue affects the Red Hat Enterprise Linux 5 and 6 kernels as well as the Debian 6 and 7 kernels. Red Hat has provided a patch to fix this issue.
It was discovered that the Linux kernel did not handle user-space requested maps of more than 2^31 elements correctly. A local attacker could use this flaw to crash the system or possibly escalate their privileges on affected systems.
Another flaw was found in the Linux kernel’s handling of symbolic address connections when using a VLAN interface. A remote attacker could use this flaw to crash a system on an affected network by transmitting a specially crafted packet.
It was discovered that the procfs file system created by the Linux kernel did not correctly handle race condition when checking the permissions for a process. This could lead to information leak or privilege escalation.
It was found that the Linux kernel’s ptrace implementation allowed user access to ptrace system calls, allowing privilege escalation.
It was discovered that the XFS file system implementation in the Linux kernel did not correctly handle under-length file names when using the extents feature. A local user with the ability to mount a file system can use this flaw to crash the system to gain access to data.
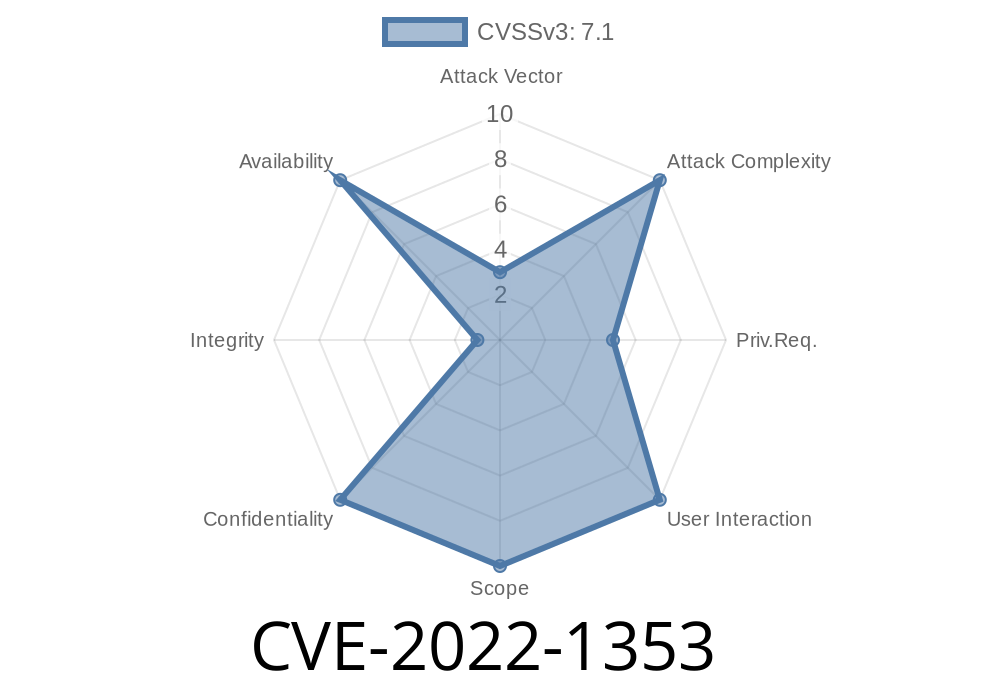
Linux Kernel Type Confusion Vulnerability
The CVE-2022-1353 type confusion vulnerability was discovered in the Linux kernel. A local attacker could use this flaw to crash the system or potentially escalate their privileges on affected systems.
Another flaw was found in the Linux kernel’s handling of symbolic address connections when using a VLAN interface. A remote attacker could use this flaw to crash a system on an affected network by transmitting a specially crafted packet.
It was discovered that the procfs file system created by the Linux kernel did not correctly handle race condition when checking the permissions for a process. This could lead to information leak or privilege escalation.
It was found that the Linux kernel’s ptrace implementation allowed user access to ptrace system calls, allowing privilege escalation.
It was discovered that the XFS file system implementation in the Linux kernel did not correctly handle under-length file names when using the extents feature. A local user with the ability to mount a file system can use this flaw to crash the system to gain access to data.
Timeline
Published on: 04/29/2022 16:15:00 UTC
Last modified on: 07/04/2022 11:15:00 UTC
References
- https://github.com/torvalds/linux/commit/9a564bccb78a76740ea9d75a259942df8143d02c
- https://bugzilla.redhat.com/show_bug.cgi?id=2066819
- https://www.debian.org/security/2022/dsa-5127
- https://security.netapp.com/advisory/ntap-20220629-0001/
- https://lists.debian.org/debian-lts-announce/2022/07/msg00000.html
- https://www.debian.org/security/2022/dsa-5173
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-1353