CVE-2018-5712 was discovered by Eric Chan of Tencent's Vulnerability Research team. The vulnerability occurs because the code of the browser inlines certain functions. In particular, when a user attempts to load a malicious website, the code of the browser attempts to load the content of this site into memory. However, if the loaded function happens to trigger a memory allocation error, the memory allocation error will be handled by a system library function called “Heap32Free”, which may lead to the execution of arbitrary code.
To exploit the vulnerability, an attacker would have to convince a user to visit a malicious website that is hosted on a server with an affected version of Chrome. This may be done through various methods, such as social engineering, tricking the user into visiting a malicious website, or infecting the user’s device with malware. After the user visits a malicious website, the browser may attempt to load data from this site into memory. However, if the loaded data triggers a memory allocation error, the memory allocation error will be handled by “Heap32Free”, which allows attackers to potentially exploit heap corruption via a crafted HTML page. In the case that this occurs, an attacker may be able to execute arbitrary code on the user’s system. Because this vulnerability occurs in the browser, users are encouraged to update to the latest version of Chrome as soon as possible
Vulnerability Details
“Heap32Free” handles memory allocation errors by freeing up the appropriate amount of memory. This function is called when the allocated memory cannot be freed via a normal mechanism.
In the case of “CVE-2018-5712”, “Heap32Free” will free up the memory for the same function that caused the error, leading to an arbitrary write in process space that can allow attackers to execute code on a user's system.
Vulnerability Information
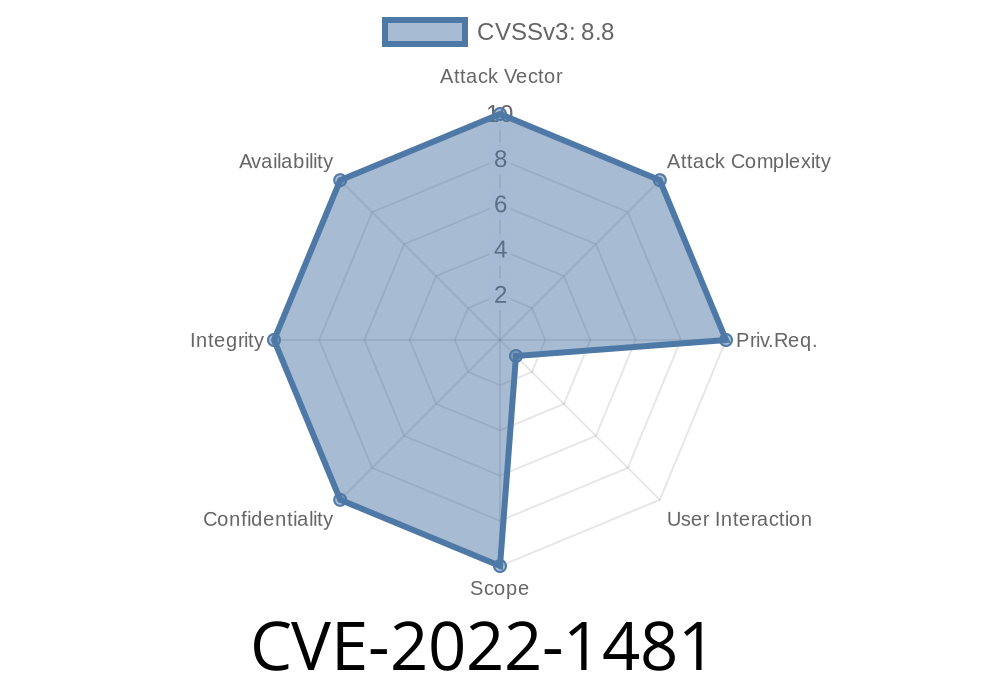
The vulnerability CVE-2022-1481 was discovered by Eric Chan of Tencent's Vulnerability Research team. The vulnerability occurs because the code of the browser inlines certain functions. In particular, when a user attempts to load a malicious website, the code of the browser attempts to load the content of this site into memory. However, if the loaded function happens to trigger a memory allocation error, the memory allocation error will be handled by a system library function called "Heap32Free". This may lead to the execution of arbitrary code.
To exploit this vulnerability, an attacker would have to convince a user to visit a malicious website that is hosted on a server with an affected version of Chrome. This may be done through various methods, such as social engineering, tricking the user into visiting a malicious website, or infecting their device with malware. After the user visits a malicious website, they may attempt to load data from this site into memory. If they do so and these bytes happen to trigger heap corruption via a crafted HTML page then an attacker may be able to execute arbitrary code on users' systems. Because this vulnerability occurs in Chrome and it's extension content (such as JavaScript), users are encouraged update Chrome as soon as possible.
Vulnerability Description
There is a vulnerability in Chrome which can be exploited by an attacker to execute arbitrary code on the user's system. The attack vector is social engineering, but also compromised devices are susceptible.
Timeline
Published on: 07/26/2022 22:15:00 UTC
Last modified on: 08/15/2022 11:16:00 UTC