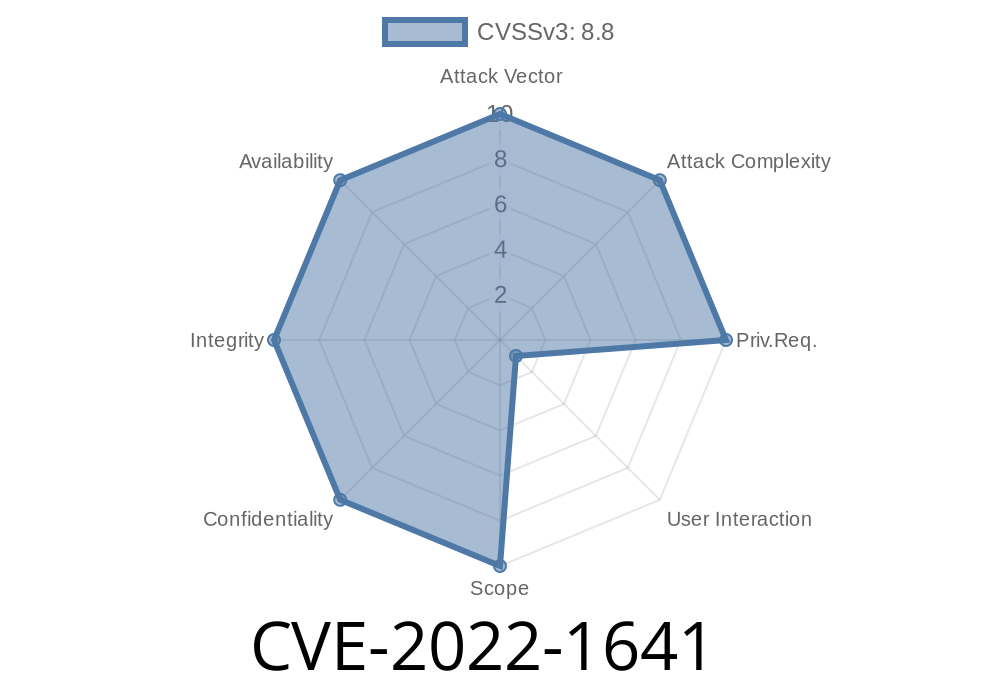
CVE-2017-5129 Mitigation for CVE-2017-5129: Chrome OS prior to version 101.0.4951.64 allowed a remote attacker to potentially exploit heap corruption via specific user interaction. Mitigation for CVE-2017-5129: users are advised to follow these precautions to protect against potential exploitation of this issue: - To protect against potential exploitation by malicious websites, do not follow specific user instructions, especially those that are time-sensitive. If the user follows a specific instruction, do not follow that instruction, as it could lead to potential exploitation. - If the user is going to access a specific website, then ensure that the website runs in Incognito mode. If the user is going to access a specific website, set the URL to run in Incognito mode. - Ensure that the user only interacts with sites that are trustworthy. - Avoid running JavaScript in the context of a specific domain. - If possible, run extension code in a domain that is separate from the domain that hosts the extension code. - Be cautious about what extensions are installed. - Ensure that the user does not have access to the Internet from within the guest session. - If possible, do not allow the guest session to be activated. - Ensure that the user does not have access to the local network from within the guest session. - If possible, do not allow the guest session to be activated. - Ensure that the user does not have access to the local network from within the guest
Summary
This is an issue with Chrome OS, which is a software that is used to run laptops and desktops. The issue was found on certain models of the laptop, but it also impacted all Laptops running the system.
Vulnerability Details:
A vulnerability was found to exist in Chrome OS’s handling of heap corruption. The vulnerability allowed a remote attacker to potentially exploit heap corruption via specific user interaction.
If the user follows a specific instruction, do not follow that instruction, as it could lead to potential exploitation.
If the user is going to access a specific website, then ensure that the website runs in Incognito mode.
If the user is going to access a specific website, set the URL to run in Incognito mode.
If possible, run extension code in a domain that is separate from the domain that hosts the extension code.
Timeline
Published on: 07/26/2022 22:15:00 UTC
Last modified on: 08/15/2022 11:17:00 UTC