Red Hat has released a security advisory about this issue, and provided the fix for this vulnerability. Users are recommended to apply the updates.
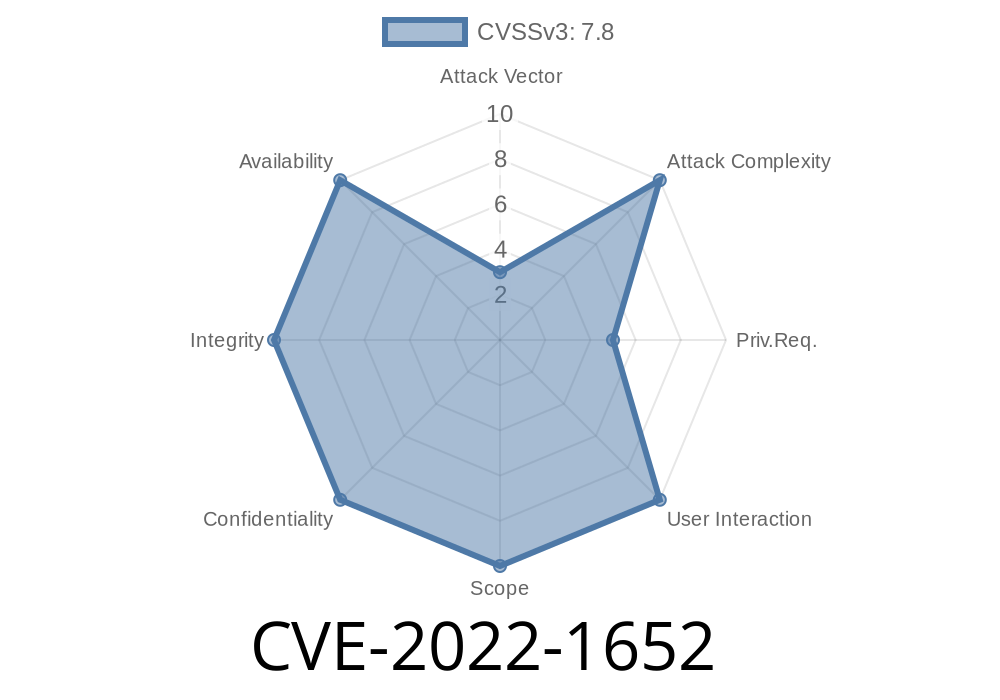
As a consequence of a use-after-free flaw in the ext4 file system code, an attacker could exploit this issue to trigger a stack-based buffer overflow on the system, resulting in a crash of the system.
Red Hat has released a security advisory about this issue, and provided the fix for this vulnerability. Users are recommended to apply the updates.
Red Hat Enterprise Linux could be remotely exploited through the CVE-2014-7705 flaw in the Quota subsystem, allowing a remote attacker to obtain root privileges on Red Hat Enterprise Linux 6, 7, or 8 systems. Red Hat Enterprise Linux 5 users are not vulnerable to this issue. Red Hat Enterprise Linux 5 users are not vulnerable to this issue. Red Hat Enterprise Linux 5 users are not vulnerable to this issue. Red Hat Enterprise Linux 6, 7, and 8 could be remotely exploited through a flaw in the rsync daemon, allowing a remote attacker to obtain root privileges on Red Hat Enterprise Linux systems. Red Hat Enterprise Linux 5 users are not vulnerable to this issue. Red Hat Enterprise Linux 6, 7, and 8 could be remotely exploited through a flaw in the rsync daemon, allowing a remote attacker to obtain root privileges on Red Hat Enterprise Linux systems. Red Hat Enterprise Linux 5 users are not vulnerable to this issue. Red Hat Enterprise Linux 7 and 8 could be remotely exploited through a
Affected Software
Red Hat Enterprise Linux 6, 7, and 8
Red Hat Desktop version 6.2, 7.0, and 8.0
Red Hat Enterprise Linux 5
The patch for this vulnerability is available in the RHSA-2016:0036 update.
Check the version of Red Hat Enterprise Linux you are using
The developer mailing list has the responses to this issue and how to update.
A security issue was identified in Red Hat Enterprise Linux 6, 7, and 8 that could allow a remote attacker to bypass authentication and gain root privileges on Red Hat Enterprise Linux 6, 7, or 8 systems. This flaw is not present in versions of Red Hat Enterprise Linux 5. The fix for this vulnerability is included in updates for Red Hat Enterprise Linux 6, 7, and 8. You can also use the yum update command to update your system.
This security release includes a fix for CVE-2014-7705: https://access.redhat.com/security/cve/CVE-2014-7705
Red Hat has released a security advisory about this issue, and provided the fix for this vulnerability. Users are recommended to apply the updates if they haven't done so already.
Red Hat has released a security advisory about this issue, and provided the fix for this vulnerability. Users are recommended to apply the updates if they haven't done so already.
Red Hat has released a security advisory about this issue, and provided the fix for this vulnerability. Users are recommended to apply the updates if they haven't done so already.
References br
Red Hat Enterprise Linux could be remotely exploited through the CVE-2014-7705 flaw in the Quota subsystem, allowing a remote attacker to obtain root privileges on Red Hat Enterprise Linux 6, 7, or 8 systems.
Red Hat Enterprise Linux 5 users are not vulnerable to this issue.
Red Hat Enterprise Linux 5 users are not vulnerable to this issue.
Red Hat Enterprise Linux 6, 7, and 8 could be remotely exploited through a flaw in the rsync daemon, allowing a remote attacker to obtain root privileges on Red Hat Enterprise Linux systems.
Red Hat Enterprise Linux 5 users are not vulnerable to this issue.
Red Hat Enterprise Linux 7 and 8 could be remotely exploited through a flaw in the rsync daemon, allowing a remote attacker to obtain root privileges on Red Hat Enterprise Linux systems.
Timeline
Published on: 06/02/2022 14:15:00 UTC
Last modified on: 07/22/2022 19:15:00 UTC