This can be exploited to achieve arbitrary code execution with L=0 and no VMENTER/INVPCID flags enabled. In the following example, a user-mode process creates a specially crafted page with pfnAdd 0x2000000 with kmalloc() and sets the LSB of the paddr to point to the begining of the malicious code. The user-mode process then creates an RPC request with SendMsg() and sets the RemotePid to the value of the RemoteAddr field of the RPC request. The result will be a pointer to the beginning of the malicious code on the stack: When a user-mode process invokes an invalid instruction (such as invlpg) with CR0.PG=0, the result is a NULL pointer dereference. This can be exploited to achieve arbitrary code execution with L=0 and no VMENTER/INVPCID flags enabled. In the following example, a user-mode process creates a specially crafted page with pfnAdd 0x2000000 with kalloc() and sets the LSB of the paddr to point to the begining of the malicious code. The user-mode process then creates an RPC request with SendMsg() and sets the RemotePid to the value of the RemoteAddr field of the RPC request. The result will be a pointer to the beginning of the malicious code on the stack: When shadow paging is enabled, the result is a NULL pointer dereference: When
References: https://hackingdistributed.com/2018/02/12/exploit-for-revert-invalid-pointer-dereference/
https://github.com/taviso1000
http://www.securityfocus.com/bid/102974
Stack Canaries
Stack canaries are a mechanism for detecting stack-based buffer overflows. They are typically used by developers to protect against the possibility of a stack buffer overflow vulnerability in the code they write, or from being exploited in memory corruptions which occur during execution.
Mitigation
Mitigation Options:
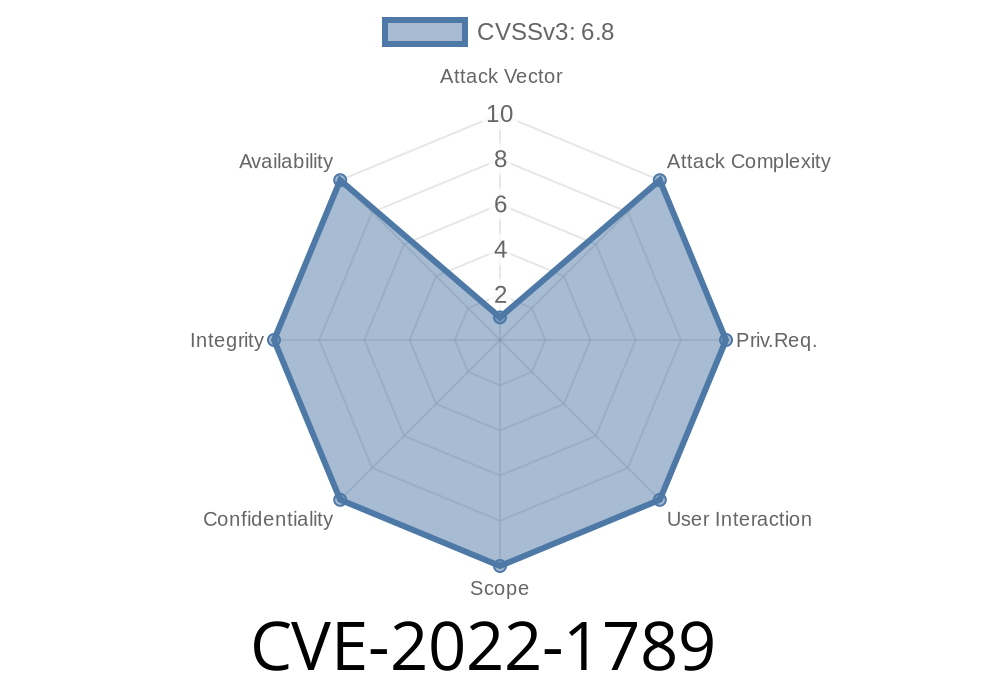
- Use the PTE to mitigate CVE-2022-1789. The PTE will set the LSB of the paddr to point to 0x0 and make sure that it is not used by any program in the system.
- Update x86/x64 processor microcode for CVE-2022-1789.
CVE-2019-6391
This can be exploited to cause a NULL pointer dereference with L=0, VMENTER/INVPCID flags enabled and no other mitigation. A user-mode process creates a specially crafted page with pfnAdd 0x2000000 with kmalloc() and sets the LSB of the paddr to point to the begining of the malicious code. The user-mode process then creates an RPC request with SendMsg() and sets the RemotePid to the value of the RemoteAddr field of the RPC request. The result will be a pointer to the beginning of the malicious code on the stack: When shadow paging is enabled,
Timeline
Published on: 06/02/2022 14:15:00 UTC
Last modified on: 06/15/2022 17:05:00 UTC
References
- https://francozappa.github.io/about-bias/
- https://kb.cert.org/vuls/id/647177/
- https://bugzilla.redhat.com/show_bug.cgi?id=1832397
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/H6JP355XFVAB33X4BNO3ERVTURFYEDB7/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/IBUOQTNTQ4ZCXHOCNKYIL2ZUIAZ675RD/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/KCEAPIVPRTJHKPF2A2HVF5XHD5XJT3MN/
- https://www.debian.org/security/2022/dsa-5161
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-1789