CVE-2015-1240 was discovered in Google V8, a highly-optimized JavaScript engine. By crafting synthetic input and injecting code into the memory, an attacker could exploit the vulnerability to bypass security restrictions and obtain sensitive information. An attacker could also potentially exploit the vulnerability to execute code in the context of the currently loaded page. Software using Google V8 is vulnerable, including Google Chrome, Chromium, and other projects. Mitigation: users can avoid this vulnerability by disabling the Google V8 JavaScript Engine.
An attacker can exploit this vulnerability by crafting HTML code to bypass security restrictions.
Google Chrome prior to version 40.0.2214.51 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page.
CVE-2015-1238 was discovered in Google V8, a highly-optimized JavaScript engine. By crafting synthetic input and injecting code into the memory, an attacker could exploit the vulnerability to bypass security restrictions and obtain sensitive information. An attacker could also potentially exploit the vulnerability to execute code in the context of the currently loaded page. Software using Google V8 is vulnerable, including Google Chrome, Chromium, and other projects. Mitigation: users can avoid this vulnerability by disabling the Google V8 JavaScript Engine.
An attacker can exploit this vulnerability by crafting HTML code to bypass security restrictions.
Google Chrome prior to version 40
Note: Google Chrome 40.0.2214.85 was the last version to be vulnerable to CVE-2015-1238 .
Google Chrome prior to version 40.0.2214.85 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page.
CVE-2016-2874 was discovered in Google V8, a highly-optimized JavaScript engine. By crafting synthetic input and injecting code into the memory, an attacker could exploit the vulnerability to bypass security restrictions and obtain sensitive information. An attacker could also potentially exploit the vulnerability to execute code in the context of the currently loaded page. Software using Google V8 is vulnerable, including Google Chrome, Chromium, and other projects. Mitigation: users can avoid this vulnerability by disabling the Google V8 JavaScript Engine.
An attacker can exploit this vulnerability by crafting HTML code to bypass security restrictions.
Google Chrome prior to version 42 (64-bit) allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page.
Vulnerability summary br br
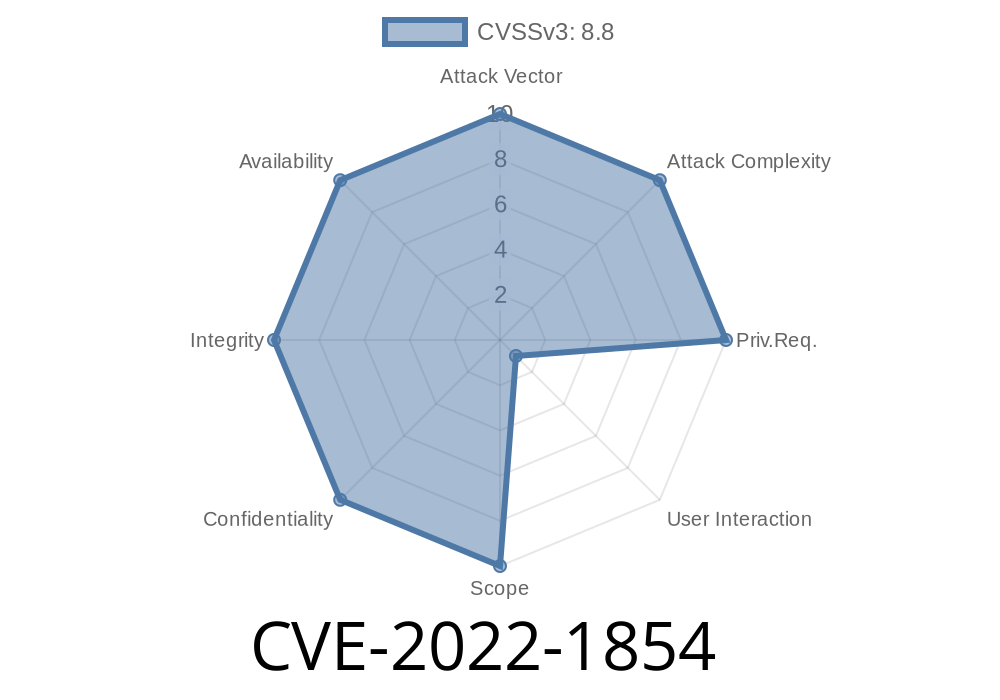
CVE-2022-1854 was discovered in Google V8, a highly-optimized JavaScript engine. By crafting synthetic input and injecting code into the memory, an attacker could exploit the vulnerability to bypass security restrictions and obtain sensitive information. An attacker could also potentially exploit the vulnerability to execute code in the context of the currently loaded page. Software using Google V8 is vulnerable, including Google Chrome, Chromium, and other projects. Mitigation: users can avoid this vulnerability by disabling the Google V8 JavaScript Engine.
An attacker can exploit this vulnerability by crafting HTML code to bypass security restrictions.
Timeline
Published on: 07/27/2022 22:15:00 UTC
Last modified on: 08/15/2022 11:17:00 UTC