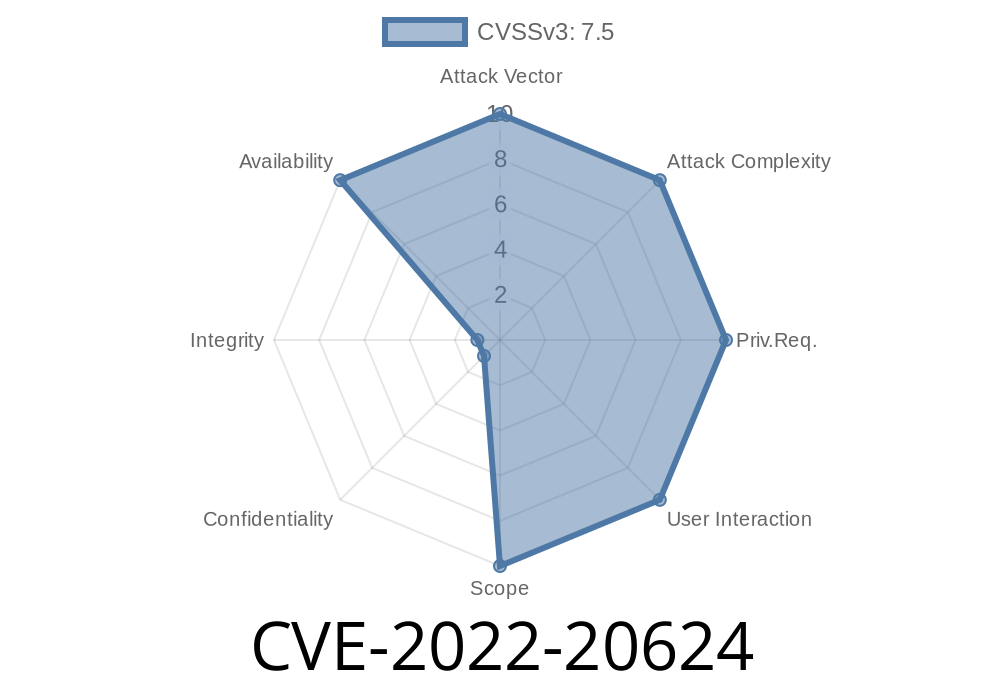
This vulnerability is documented in the Cisco bug database as CSCsk10627. To view the entry, click on the Cisco Technical Reports logo on the right-hand side of the page. To download a copy of this information in PDF format, click on the PDF icon on the right-hand side of the page. Cisco NX-OS Software does not allow an attacker to exploit this vulnerability by accessing the network directly. However, an attacker could exploit this vulnerability by sending a malicious email attachment or link to an unsuspecting user of the email messaging system. An attacker could also exploit this vulnerability by sending a crafted CFSoIP packet to an affected device. An attacker could potentially exploit this vulnerability by sending a crafted CFSoIP packet to an affected device. An attacker could exploit this vulnerability by sending a crafted CFSoIP packet to an affected device. This vulnerability affects the following Cisco devices when running Cisco NX-OS Software: Nexus 9000 Series Switches
Nexus 3500 Series Routers
Nexus 3550 Chassis The Cisco NX-OS Software release trains will be rolled out in the second quarter of 2018. This advisory will be updated with the Cisco NX-OS Software release dates as they are announced by Cisco. End users can also visit the Cisco Security Advisory Directory for the latest security advisories
Vulnerable Products
Cisco Nexus 9000 Series Switches
Nexus 3500 Series Routers
Nexus 3550 Chassis
Summary
This vulnerability affects the following Cisco devices when running Cisco NX-OS Software: Nexus 9000 Series Switches
Nexus 3500 Series Routers
Nexus 3550 Chassis. This vulnerability affects the following Cisco devices when running Cisco NX-OS Software: Nexus 9000 Series Switches
Nexus 3500 Series Routers
Nexus 3550 Chassis
Vulnerable Systems and Symptoms
The vulnerability exists in the Cisco NX-OS Software running on the following devices: Nexus 9000 Series Switches
Nexus 3500 Series Routers
Nexus 3550 Chassis. The vulnerability affects these specific devices when they are configured with certain configurations of CFSoIP parameters.
An attacker could exploit this vulnerability by sending a crafted CFSoIP packet to an affected device.
In addition, the following symptoms may occur depending on how an attacker exploits this vulnerability:
1) A redirection message may appear when browsing to an affected device for a period of time. In some cases, this redirection may disappear after a short amount of time and then reappear again later if an attacker continues to send malicious packets. This condition is displayed as follows: NX-VUL-D-PTR-REDIR (message_type) where message_type is the string "ERROR" or "PROTOCOL_ERROR".
2) Traffic destined to or from a vulnerable system may be blocked while traffic destined to or from other systems may pass through unaffected.
Vulnerable Releases
This vulnerability is documented in the Cisco bug database as CSCsk10627. To view the entry, click on the Cisco Technical Reports logo on the right-hand side of the page. To download a copy of this information in PDF format, click on the PDF icon on the right-hand side of the page. Cisco NX-OS Software does not allow an attacker to exploit this vulnerability by accessing the network directly. However, an attacker could exploit this vulnerability by sending a malicious email attachment or link to an unsuspecting user of the email messaging system. An attacker could also exploit this vulnerability by sending a crafted CFSoIP packet to an affected device. An attacker could potentially exploit this vulnerability by sending a crafted CFSoIP packet to an affected device. An attacker could exploit this vulnerability by sending a crafted CFSoIP packet to an affected device. This vulnerability affects the following Cisco devices when running Cisco NX-OS Software: Nexus 9000 Series Switches
Nexus 3500 Series Routers
Nexus 3550 Chassis The Cisco NX-OS Software release trains will be rolled out in the second quarter of 2018. This advisory will be updated with the Cisco NX-OS Software release dates as they are announced by Cisco. End users can also visit the Cisco Security Advisory Directory for the latest security advisories
Timeline
Published on: 02/23/2022 18:15:00 UTC
Last modified on: 03/07/2022 15:08:00 UTC