Cisco has determined that the majority of the Internet population is running the latest software releases. However, as many users upgrade their software, there might be a small number of users who have not updated their software. These users are likely to be on older releases such as Cisco IOS XE Software or Cisco IOS Software if they are running Cisco ESA Software. Cisco has observed ongoing attempts to exploit this vulnerability as shown in the following email example. Exploitation attempts could involve sending email messages that are crafted to exploit this vulnerability. Cisco ESA does not validate whether incoming email messages are safe or unsafe before processing them. As a result, an attacker could send a crafted email message to an affected Cisco ESA device and the Cisco ESA device could accept that message and process that email message, resulting in a DoS condition. Cisco has accounted for all email messages that are sent to Cisco ESA devices, and they are handled in a secure manner before they are handled by the Cisco ESA software.
Cisco Security Vulnerability Disclosure Guidelines
Cisco Security Vulnerability Disclosure Guidelines
Vulnerable Software and Versions
The vulnerability is present in the Cisco ESA Software running on Cisco IOS XE Software or Cisco IOS Software.
Cisco ASA Software
- Endpoint Security
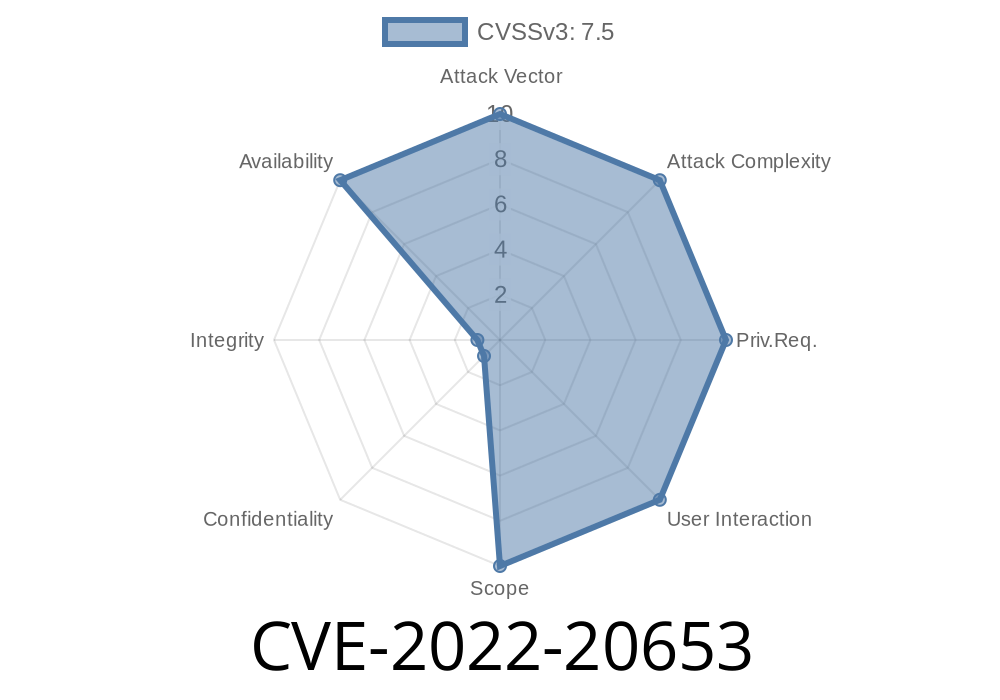
CVE-2022-20653 has been assigned to this vulnerability. An individual or group of individuals could exploit this vulnerability by sending a crafted email message to an affected Cisco ASA Software device and the Cisco ASA Software device could accept that message and process that email message, resulting in a DoS condition. Cisco has accounted for all email messages that are sent to Cisco ASA Software devices, and they are handled in a secure manner before they are handled by the Cisco ASA Software software.
Vulnerability Details
What is the vulnerability?
The Cisco ESA Software is vulnerable to a denial-of-service condition that could be exploited when receiving email messages. There are no specific conditions needed for this, but rather any message with a malicious payload could cause the device to crash or be unable to process legitimate email messages. This could result in critical service disruption for users of the device.
How could an attacker exploit this vulnerability?
An attacker could send a crafted email message that is meant to exploit this vulnerability and then the Cisco ESA device would accept and process the malicious email message under certain circumstances.
Why should you fix this vulnerability?
Cisco has determined that all of its customers are running software releases where they are not vulnerable to exploitation. As such, this vulnerability should not impact customers who have not been impacted by their software release or upgrade cycle.
Timeline
Published on: 02/17/2022 15:15:00 UTC
Last modified on: 02/25/2022 16:36:00 UTC