Cisco has assigned the following CVSS v3 scores based on the criteria below to these vulnerabilities: In addition to unauthorized access, code execution, and DoS, these vulnerabilities could be exploited to cause a remote device to restart, resulting in a denial of service. Cisco has released software updates to address these vulnerabilities. There are no known workarounds at this time. Cisco recommends monitoring for breach of these DoS conditions and implementing prevention techniques (such as firewalling/access control) to prevent unauthorized access to these devices. Cisco recommends monitoring for breach of these DoS conditions and implementing prevention techniques (such as firewalling/access control) to prevent unauthorized access to these devices. Cisco has assigned the following CVSS v3 scores based on the criteria below to these vulnerabilities: In addition to unauthorized access, code execution, and DoS, these vulnerabilities could be exploited to cause a remote device to restart, resulting in a denial of service. Cisco has released software updates to address these vulnerabilities. There are no known workarounds at this time. Cisco recommends monitoring for breach of these DoS conditions and implementing prevention techniques (such as firewalling/access control) to prevent unauthorized access to these devices
Vulnerable Products
Cisco Systems IOS Software
Cisco IOS XE Software
Cisco Nexus 5000 Series Switches, 2000 Series Fabric Extenders, 4000 Series and 4500 Series Switches, 6000 Series Switches
Cisco Networking Devices that contain Cisco IOS Software or Cisco IOS XE Software running on an affected Cisco device
Cisco IP Telephony devices that contain Cisco IOS Software or Cisco IOS XE Software running on an affected Cisco device
Remotely-Controlled Network Appliances that contain a vulnerable version of the Cisco IOS Device Manager application with a vulnerable version of the Cisco OI Module
Models of these devices: ASR 1000 Series Aggregation Services Routers (ASR 1000), ASR 1001/1001-X, ASR 1010/1010-X Chassis Only, ASR 1020/1020-X Chassis Only, ASR 1050/1050-M3-L3 Router with Universal Media Bay (UMB), B2100 Blade Switch w/2x5610 Line Cards, B4300 Blade Switch w/2x5610 Linecards, E1000 Ethernet Services Module (ESM) , E2000 Ethernet Services Module (ESM) , E3000 Multiservice Edge Router for Carrier Ethernet Services (MSER), E4000 Multiservice Edge Routers for Carrier Ethernet Services (MSER)
Vulnerability Finding Tips br >
1. Evaluate the organization’s security posture
2. Look for vulnerabilities that are not related to the infected systems (e.g., passwords, misconfiguration)
3. Identify information that can be used in lateral movement
4. Consider who has access to the network or systems and if trusted users have been compromised
CVSS Criteria
Cisco has assigned the following CVSS v3 scores based on the criteria below to these vulnerabilities: In addition to unauthorized access, code execution, and DoS, these vulnerabilities could be exploited to cause a remote device to restart, resulting in a denial of service. Cisco has released software updates to address these vulnerabilities. There are no known workarounds at this time. Cisco recommends monitoring for breach of these DoS conditions and implementing prevention techniques (such as firewalling/access control) to prevent unauthorized access to these devices
Vulnerability Overview
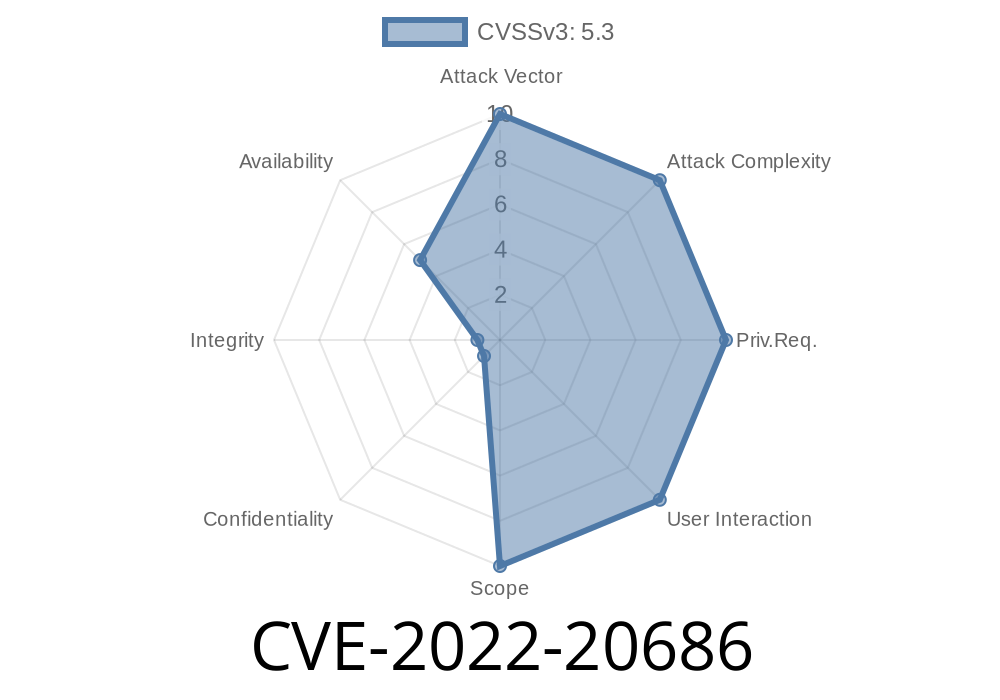
Cisco has discovered that a number of Cisco products are vulnerable to remote denial-of-service attacks. These vulnerabilities have been assigned CVE-2022-20686.
Cisco has discovered that a number of Cisco products are vulnerable to remote denial-of-service attacks. These vulnerabilities have been assigned CVE-2022-20686.
Timeline
Published on: 12/12/2022 09:15:00 UTC
Last modified on: 12/14/2022 17:08:00 UTC