Cisco Discovery Protocol is a proprietary protocol that is used to optimize the communication flow between Cisco devices. Cisco Discovery Protocol is enabled on Cisco ATA devices by default, and it is enabled on all devices with a Cisco license. Cisco Discovery Protocol can be disabled on Cisco ATA devices through the interface configuration. An attacker could exploit these vulnerabilities by sending a malicious Cisco Discovery Protocol packet to an affected device. A successful exploit could allow the attacker to cause an out-of-bounds read of the valid Cisco Discovery Protocol packet data, which could allow the attacker to cause corruption in the internal Cisco Discovery Protocol database of the affected device. Cisco ATA 190 series devices running Cisco ATA 190 Series Analog Telephone Adapter Cisco Discovery Protocol firmware version 1.0.0.5 is vulnerable. Cisco ATA 190 series devices running Cisco ATA 190 Series Analog Telephone Adapter Cisco Discovery Protocol firmware version 1.0.0.6 is vulnerable. Cisco ATA 190 series devices running Cisco ATA 190 Series Analog Telephone Adapter Cisco Discovery Protocol firmware version 1.0.0.7 is vulnerable. Cisco ATA 190 series devices running Cisco ATA 190 Series Analog Telephone Adapter Cisco Discovery Protocol firmware version 1.0.0.8 is vulnerable. Cisco ATA 190 series devices running Cisco ATA 190 Series Analog Telephone Adapter Cisco Discovery Protocol firmware version 1.0.0.9 is vulnerable
Summary
Cisco Discovery Protocol is enabled on Cisco ATA devices by default. An attacker could exploit these vulnerabilities by sending a malicious Cisco Discovery Protocol packet to an affected device. A successful exploit could allow the attacker to cause an out-of-bounds read of the valid Cisco Discovery Protocol packet data, which could allow the attacker to cause corruption in the internal Cisco Discovery Protocol database of the affected device.
Security Statement:
A vulnerability exists in Cisco Discovery Protocol that could be exploited by an attacker to cause a denial of service or other system impact.
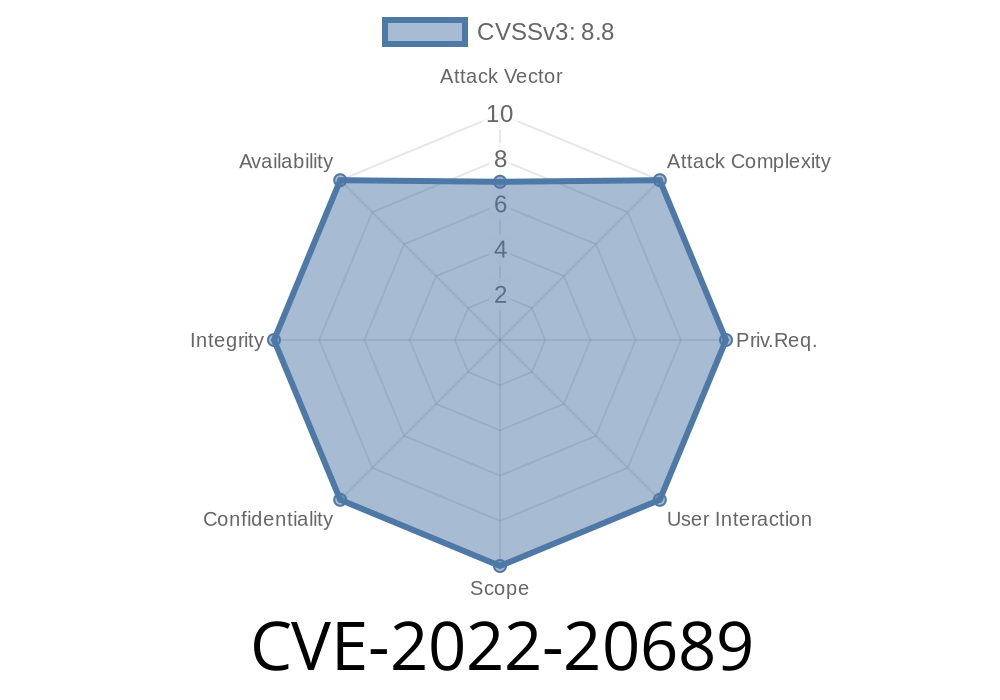
Cisco has assigned CVE-2022-20689 to this issue. Cisco recommends users upgrade to a fixed release or obtain the latest version of Cisco Discovery Protocol.
Cisco Discovery Protocol Vulnerability Overview
Cisco Discovery Protocol 1.0.0.9 is a vulnerability that affects Cisco ATA 190 series devices running Cisco ATA 190 Series Analog Telephone Adapter Cisco Discovery Protocol firmware version 1.0.0.9, CVE-2022-20689. An attacker could exploit these vulnerabilities by sending a malicious Cisco Discovery Protocol packet to an affected device, which could allow the attacker to cause corruption in the internal Cisco Discovery Protocol database of the affected device.
Description of Cisco Discovery Protocol Vulnerabilities
Cisco Discovery Protocol is a proprietary protocol that is used to optimize the communication flow between Cisco devices. Cisco Discovery Protocol is enabled on Cisco ATA devices by default, and it is enabled on all devices with a Cisco license. Cisco Discovery Protocol can be disabled on Cisco ATA devices through the interface configuration. An attacker could exploit these vulnerabilities by sending a malicious Cisco Discovery Protocol packet to an affected device. A successful exploit could allow the attacker to cause an out-of-bounds read of the valid Cisco Discovery Protocol packet data, which could allow the attacker to cause corruption in the internal Cisco Discovery Protocol database of the affected device.
Summary of Cisco Discovery Protocol Cisco Discovery Protocol Cisco Discovery Protocol Cisco Discover Protocol
Cisco Discovery Protocol Cisco Discovery Protocol Cisco Discover Protocol
Cisco Discovery Protocol
Timeline
Published on: 12/12/2022 09:15:00 UTC
Last modified on: 12/14/2022 16:21:00 UTC