Cisco Discovery Protocol is a proprietary protocol that is used to optimize the communication flow between Cisco devices. Cisco Discovery Protocol is enabled on Cisco ATA devices by default, and it is enabled on all devices with a Cisco license. Cisco Discovery Protocol can be disabled on Cisco ATA devices through the interface configuration. An attacker could exploit these vulnerabilities by sending a malicious Cisco Discovery Protocol packet to an affected device. A successful exploit could allow the attacker to cause an out-of-bounds read of the valid Cisco Discovery Protocol packet data, which could allow the attacker to cause corruption in the internal Cisco Discovery Protocol database of the affected device. Cisco ATA 190 series devices running Cisco ATA 190 Series Analog Telephone Adapter Cisco Discovery Protocol firmware version 1.0.0.5 is vulnerable. Cisco ATA 190 series devices running Cisco ATA 190 Series Analog Telephone Adapter Cisco Discovery Protocol firmware version 1.0.0.6 is vulnerable. Cisco ATA 190 series devices running Cisco ATA 190 Series Analog Telephone Adapter Cisco Discovery Protocol firmware version 1.0.0.7 is vulnerable. Cisco ATA 190 series devices running Cisco ATA 190 Series Analog Telephone Adapter Cisco Discovery Protocol firmware version 1.0.0.8 is vulnerable. Cisco ATA 190 series devices running Cisco ATA 190 Series Analog Telephone Adapter Cisco Discovery Protocol firmware version 1.0.0.9 is vulnerable
Cisco Discovery Protocol Remote Code Execution Vulnerability
The Cisco Discovery Protocol (CDP) is a proprietary protocol that is used to optimize the communication flow between Cisco devices. Cisco Discovery Protocol is enabled on Cisco ATA devices by default, and it is enabled on all devices with a Cisco license.
An attacker could exploit these vulnerabilities by sending a malicious Cisco Discovery Protocol packet to an affected device. A successful exploit could allow the attacker to cause an out-of-bounds read of the valid Cisco Discovery Protocol packet data, which could allow the attacker to cause corruption in the internal Cisco Discovery Protocol database of the affected device.
Cisco ATA 190 series devices running Cisco ATA 190 Series Analog Telephone Adapter CDP firmware version 1.0.0.5 is vulnerable.
Installation of Cisco Discovery Protocol
The Cisco Discovery Protocol is a proprietary protocol that is used to optimize the communication flow between Cisco devices. The Cisco Discovery Protocol is enabled on Cisco ATA devices by default and it is enabled on all devices with a Cisco license. The following steps are executed during the installation process of Cisco Discovery Protocol:
1) During step 2, the device checks for an un-updated version of the protocol. If one exists, then the installation pauses.
2) During step 3, if it has not yet been checked, then the device performs a check of its current version against any available updates from other devices within range. If no updates exist, then the installation proceeds.
3) If there exist updates for this device and those updates are identified as being "compatible", then the installation proceeds with downloading and installing them. At this point, before proceeding with updating to new software, the current software version is upgraded in case there was an upgrade update available as well.
4) After all updates have been installed successfully on this device, it checks to see if any updated versions have become available since installation has finished and prompts for download if so.
Cisco Discovery Protocol Nodes
The Cisco Discovery Protocol is composed of at least one master node and a certain number of slave nodes. The master node initiates the discovery process when it scans the network for Cisco Discovery Protocol devices. The master node then sends out a discovery packet that includes its own identity, MAC address, and timestamp information, which is received by the slave nodes in succession.
Each time a new device joins the network, it becomes a slave node to the master node. Each slave node responds to the master with its own identity, MAC address, and timestamp information.
Cisco Discovery Protocol is an insecure protocol
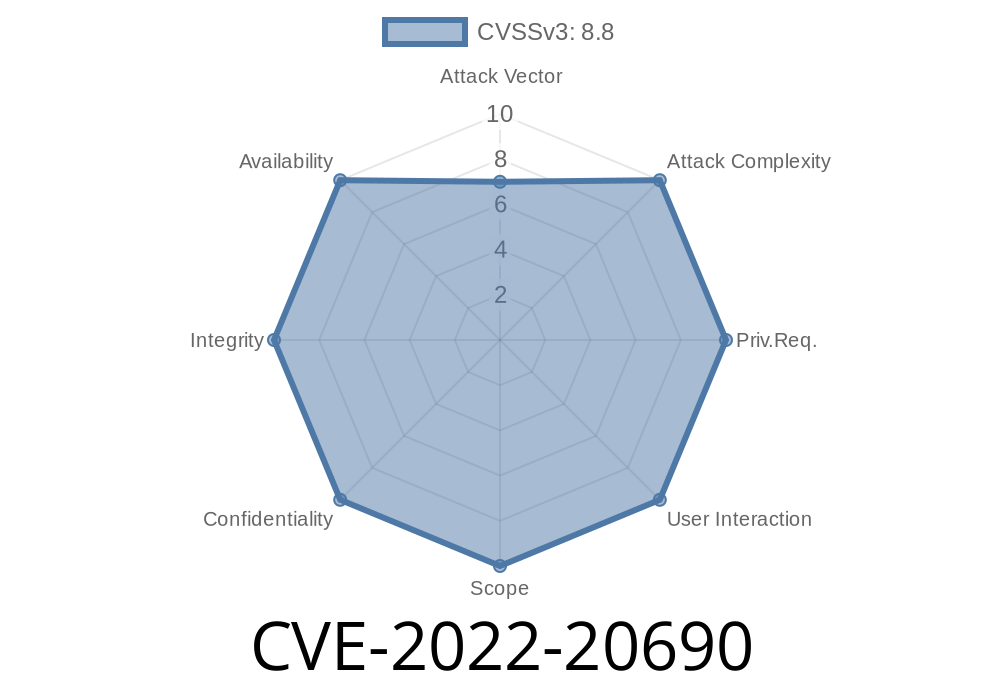
CVE-2022-20690 is a vulnerability that could be exploited by attackers to bypass authentication and gain unauthorized access to an affected device.
Cisco Discovery Protocol is an insecure protocol. It has the potential for attacks like denial of service (DoS) and eavesdropping on communication between Cisco devices. While the vulnerabilities require a valid Cisco Discovery Protocol packet to exploit, an attacker could send malicious packets to an affected device in order to cause corruption in the internal Cisco Discovery Protocol database of the affected device, which could allow them to bypass authentication. This vulnerability affects all versions of Cisco ATA 190 models running variants of Cisco Discovery Protocol firmware.
Timeline
Published on: 12/12/2022 09:15:00 UTC
Last modified on: 12/14/2022 16:22:00 UTC