The attacker could also access data or perform actions that require administrative privileges, if the administrative user has enabled those functions on the device. The attacker could have accessed the desired data if the administrative user had enabled remote management of the device. Cisco has released software updates to address this vulnerability. To be certain that your device is running the latest software version, check the versions displayed in the output of the show version command. Cisco recommends that administrators review the security configuration of their devices and consider implementing the following best practices to help protect against exploitation of this vulnerability. Be aware that there is a difference between authentication controls of a network device and the authentication controls of the device’s management interface. When validating user credentials for management access, administrators should follow the same credentials validation rules as for the entire network.
Ensure that the management interface of the device is not accessible from the Internet.
Disable remote management of the device, if it is enabled.
Disable remote management of the device, if it is enabled. Restrict administrative access of the device, if required.
Cisco Intrusion Prevention System (IPS)
Cisco IPS is a security solution that provides proactive protection against cyber attacks. Cisco IPS products include stateful inspection firewall appliances and intrusion prevention solutions that inspect all network traffic to identify malicious activity. The information gathered by the IPS is then used to further protect data and systems. Cisco IPS products are designed for organizations with networks of any size because they can scale to handle large or complex environments with thousands of devices, applications, and users.
With Cisco IPS, you can:
- Protect your organization from cyber attacks before they happen
- Reduce risks from zero day exploits
- Mitigate denial of service (DoS) attacks
- Detect unauthorized device access or changes
- Monitor SSL encrypted traffic in your network
Cisco ASA and Firepower software vulnerability summary
Cisco has released software updates to address a vulnerability affecting certain Cisco ASA and Firepower products. The vulnerability could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition or to execute arbitrary code on the affected system.
Cisco has been informed of one documented exploit of this vulnerability.
The vulnerability is caused by improper input validation in the management interface of some Cisco ASA and Firepower products. An attacker could exploit this vulnerability by sending malicious input to the Cisco ASA or Firepower device via the management interface.
Cisco has released software updates that address this vulnerability and are available at https://www.cisco.com/c/en/us/support/docs/security-vulnerability-policy-tsd-00116979/.
Cisco Device Type
Authentication Controls
If a device is running Cisco IOS Software or Cisco IOS XE Software, administrators can use the login authentication command to protect against remote exploitation of this vulnerability.
The login authentication command prevents unauthorized access to the privileged EXEC mode of a device by requiring users to authenticate themselves before they can execute management commands on the device. By default, the login command uses usernames and passwords configured on the device. If you want to authenticate users with an SSH key instead of a username and password, use one of these options:
- Use ssh keys in /etc/ssh/ssh_config for server-side authentication and ssh keys in ~/.ssh/authorized_keys for client-side authentication.
- Use SSH public keys in ~/.ssh/authorized_keys for server-side authentication and SSH public keys in authorized_keys2 for client-side authentication.
Cisco Product Transparency:
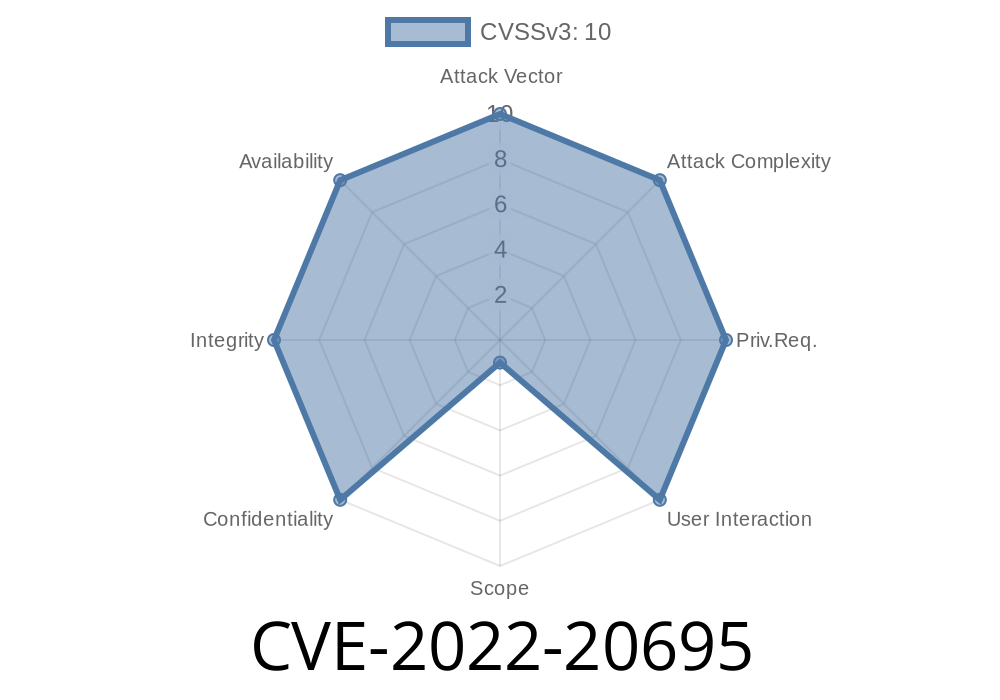
How to Protect Against CVE-2022-20695
To protect against the vulnerability, Cisco recommends that administrators review the security configuration of their devices and consider implementing the following best practices to help protect against exploitation:
Be aware that there is a difference between authentication controls of a network device and the authentication controls of the device’s management interface. When validating user credentials for management access, administrators should follow the same credentials validation rules as for the entire network.
Enable remote management of the device, if it is enabled.
Disable remote management of the device, if it is enabled. Restrict administrative access of the device, if required.
Timeline
Published on: 04/15/2022 15:15:00 UTC
Last modified on: 05/13/2022 18:13:00 UTC