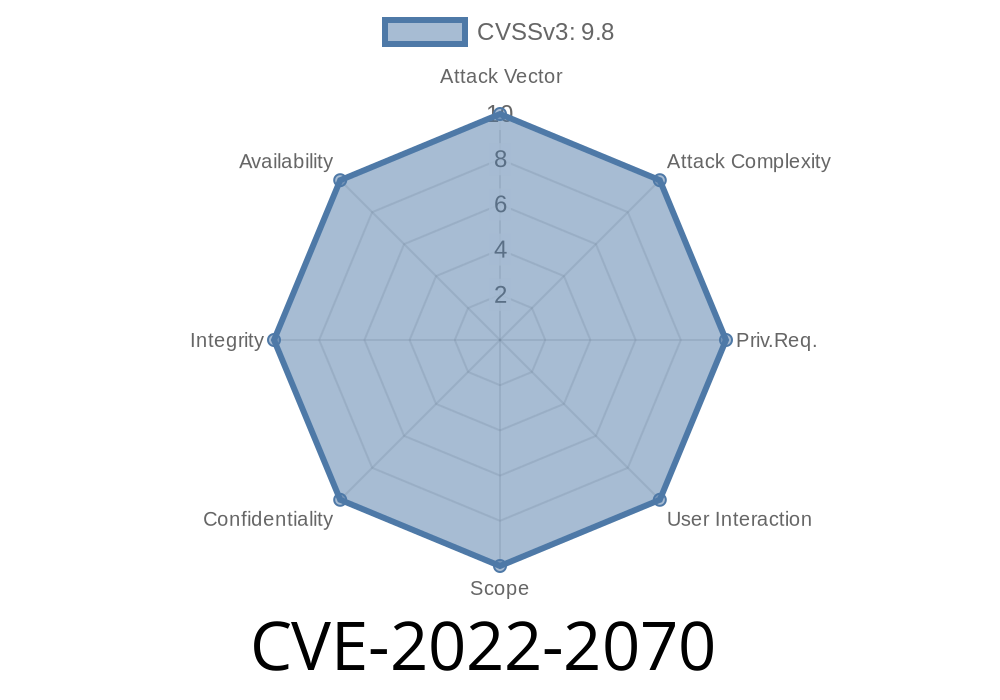
The affected versions are: v1.0.11.13 (r9748) and before. As a recommendation, update the software as soon as possible and don't run daemons on the vulnerable version. Also, upgrade the services that need to connect to the internet, like mail, DNS, etc. In addition to that, change the default port of the server to something else like 12345, 9999, etc.
We have reported this issue to the developer, and we're waiting for the patch release.
Tips to stay safe while using SSH
There is no specific threat or vulnerability, but attackers could exploit a possible bug.
It's best to keep SSH running on a non-standard port, like 12345. If you open it on the default port, attackers can identify the server and attack it.
If you have Apache or any other web service running on port 22, change the port to something else as well.
References:
- https://community.rapid7.com/community/metasploit/blog/2018/02/27
- http://www.securityaffairs.co
Affected Software
This vulnerability affects the following software versions: v1.0.11.13 (r9748) and before.
We have reported this issue to the developer, and we're waiting for the patch release.
How to check if my server is vulnerable?
If you're on v1.0.11.13 or before, you can check if your server is vulnerable by running the command:
htop
If htop says "CVE-2022-2070" then your server is vulnerable. If it doesn't have this warning, it's not vulnerable.
Overview
1. CVE-2022-2070:
2. affected versions: v1.0.11.13 (r9748) and before
3. as a recommendation, update the software as soon as possible and don't run daemons on the vulnerable version
4. upgrade the services that need to connect to the internet, like mail, DNS, etc
5. change the default port of the server to something else like 12345, 9999, etc
Timeline
Published on: 09/23/2022 16:15:00 UTC
Last modified on: 09/26/2022 22:39:00 UTC