Cisco APs are vulnerable if they are in client-to-client mode and have a wireless interface configured. The following example shows the sequence of events that could occur if a Cisco AP is in client-to-client configuration mode and has a wireless interface configured. The AP receives a frame destined to a wireless client. The AP forwards the frame to the wireless interface. The wireless client receives the frame on the native VLAN. In this configuration, an unauthenticated, adjacent attacker could inject frames from the native VLAN to clients within nonnative VLANs on the affected device. An attacker could exploit this vulnerability by obtaining access to the native VLAN and directing traffic directly to the client through their MAC/IP combination. A successful exploit could allow the attacker to bypass VLAN separation and potentially also bypass any Layer 3 protection mechanisms that are deployed. Cisco APs are vulnerable if they are in client-toRedirection mode and have a wireless interface configured. The following example shows the sequence of events that could occur if a Cisco AP is in client-toRedirection configuration mode and has a wireless interface configured. The AP receives a frame destined to a wireless client. The AP forwards the frame to the wireless Redirection In this configuration, an unauthenticated, adjacent attacker could inject frames from the native VLAN to clients within nonnative VLANs on the affected device
Cisco Catalyst 6500 Series Switch
The Cisco Catalyst 6500 Series Switch is a popular device for businesses and individuals. The switch supports VLANs which allows organizations to segment their network. This is helpful in case you have different departments that need to communicate without interference with each other. However, this divide into segments can also lead to more vulnerabilities such as the one in this blog post.
What is Cisco ASA Software?
Cisco ASA Software is the next-generation firewall and VPN platform from Cisco. It is a next-generation firewall that provides enterprise-class, stateful, application-aware and microsegmentation capabilities. The ASA software includes threat prevention technologies (network behavior monitoring), advanced malware protection, and real-time network intrusion prevention.
The following table describes the key features of Cisco ASA Software:
You can learn more about the features of Cisco ASA Software by visiting http://www.cisco.com/c/en/us/products/collateral/asa-5000-series-next-generation-firewalls_ps377028_Products_Family_Navigator_v1.html
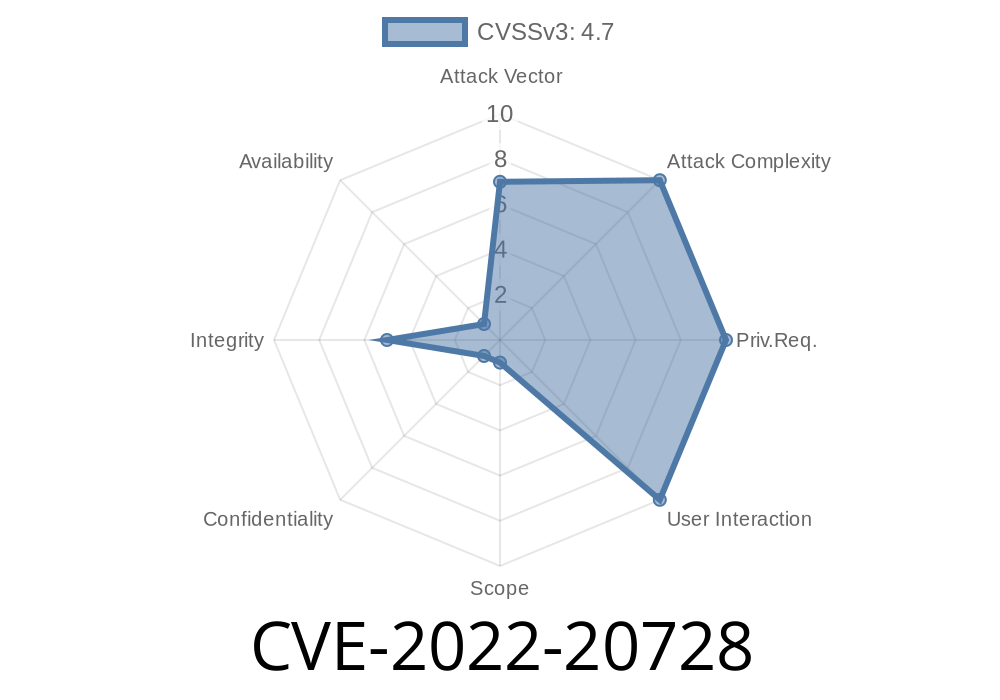
Cisco APs are vulnerable if they are in client-toClient mode and have a wireless interface configured (CVE 2022 - 20728).
Vulnerable Products
The following products have been identified as vulnerable:
Cisco APs in client-to-client mode and with a wireless interface configured.
Overview
Cisco APs are vulnerable if they are in client-to-client mode and have a wireless interface configured. The following example shows the sequence of events that could occur if a Cisco AP is in client-to-client configuration mode and has a wireless interface configured. The AP receives a frame destined to a wireless client. The AP forwards the frame to the wireless interface. The wireless client receives the frame on the native VLAN. In this configuration, an unauthenticated, adjacent attacker could inject frames from the native VLAN to clients within nonnative VLANs on the affected device. An attacker could exploit this vulnerability by obtaining access to the native VLAN and directing traffic directly to the client through their MAC/IP combination. A successful exploit could allow the attacker to bypass VLAN separation and potentially also bypass any Layer 3 protection mechanisms that are deployed
Timeline
Published on: 09/30/2022 19:15:00 UTC
Last modified on: 10/04/2022 18:50:00 UTC