Cisco Adaptive Security Device Manager (ASDM) could allow an unauthenticated, remote attacker to perform a denial of service (DoS) condition against the device. This vulnerability is due to improper validation of the HTTP requests that are sent by the user interface when enabling/disabling features. An attacker could exploit this vulnerability by sending crafted HTTP requests to the user interface. A successful exploit could allow the attacker to disable the device, preventing it from using its remote access VPN features. Cisco Security Manager (CSM) could allow an unauthenticated, remote attacker to perform a denial of service (DoS) condition against the device. This vulnerability is due to improper validation of the HTTP requests that are sent by the user interface when enabling/disabling features. An attacker could exploit this vulnerability by sending crafted HTTP requests to the user interface. A successful exploit could allow the attacker to disable the device, preventing it from using its remote access VPN features. Cisco ASA Software could allow an authenticated, remote attacker to elevate privilege level 15 access to the device. This vulnerability is due to improper separation of authentication and authorization scopes. An attacker could exploit this vulnerability by sending crafted HTTPS messages to the web management interface of an affected device
Cisco FirePower Management Module is Vulnerable
Cisco FirePower Management Module is vulnerable to HTTP request injection, which could allow an unauthenticated, remote attacker to perform a denial of service (DoS) condition against the device. This vulnerability is due to improper validation of the HTTP requests that are sent by the user interface when enabling/disabling features. An attacker could exploit this vulnerability by sending crafted HTTP requests to the user interface. Cisco ASA Software is vulnerable to HTTP request injection, which could allow an authenticated, remote attacker to elevate privilege level 15 access to the device. This vulnerability is due to improper separation of authentication and authorization scopes. An attacker could exploit this vulnerability by sending crafted HTTPS messages to the web management interface of an affected device
Cisco ASA Software Could Allow In-Progress Denial of Service
Cisco Adaptive Security Device Manager (ASDM) could allow an authenticated, remote attacker to elevate privilege level 15 access to the device. This vulnerability is due to improper separation of authentication and authorization scopes. An attacker could exploit this vulnerability by sending crafted HTTPS messages to the web management interface of an affected device. Cisco Security Manager (CSM) could allow an authenticated, remote attacker to elevate privilege level 15 access to the device. This vulnerability is due to improper separation of authentication and authorization scopes. An attacker could exploit this vulnerability by sending crafted HTTPS messages to the web management interface of an affected device.
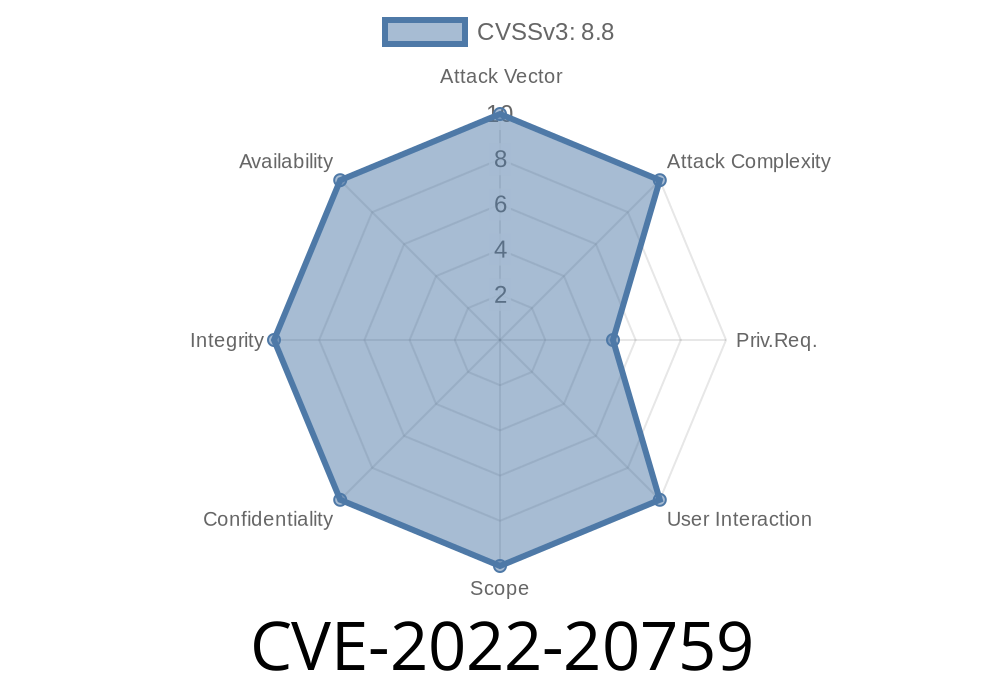
Cisco ASA Software could allow an authenticated, remote attacker to elevate privilege level 15 acces to the device. This vulnerability is due to improper separation of authentication and authorization scopes. An attacker could exploit this vulnerability by sending crafted HTTPS messages to the web management interface of an affected device.
Cisco Adaptive Security Device Manager (ASDM) could allow an unauthenticated, remote attacker to perform a denial of service (DoS) condition against the device. This vulnerability is due to improper validation of the HTTP requests that are sent by the user interface when enabling/disabling features. An attacker could exploit this vulnerability by sending crafted HTTP requests to the user interface. A successful exploit could allow the attacker to disable the device, preventing it from using its remote access VPN features. Cisco Security Manager (CSM) could allow an unauthenticated, remote attacker to perform a denial of service (DoS) condition against the device. This vulnerability is due to improper validation of the HTTP requests that are sent by the user interface when enabling/disabling features. An attacker could exploit this vulnerability by sending crafted HTTP requests to the user interface. A successful exploit could allow the attacker to disable the device, preventing it from using its remote access VPN features.
Cisco Adaptive Security Device Manager (ASDM) could allow an unauthenticated, remote attacker to perform a denial of service (DoS) condition against the device. This vulnerability is due to improper validation of the HTTP requests that are sent by the user interface when enabling/disabling features. An attacker could exploit this vulnerability by sending crafted HTTP
Cisco Adaptive Security Device Manager (ASDM)
The vulnerability is caused by improper validation of the HTTP requests that are sent from the user interface when enabling/disabling features. An attacker could exploit this vulnerability by sending crafted HTTP requests to the user interface. A successful exploit could allow the attacker to disable the device, preventing it from using its remote access VPN features.
Timeline
Published on: 05/03/2022 04:15:00 UTC
Last modified on: 05/13/2022 18:03:00 UTC