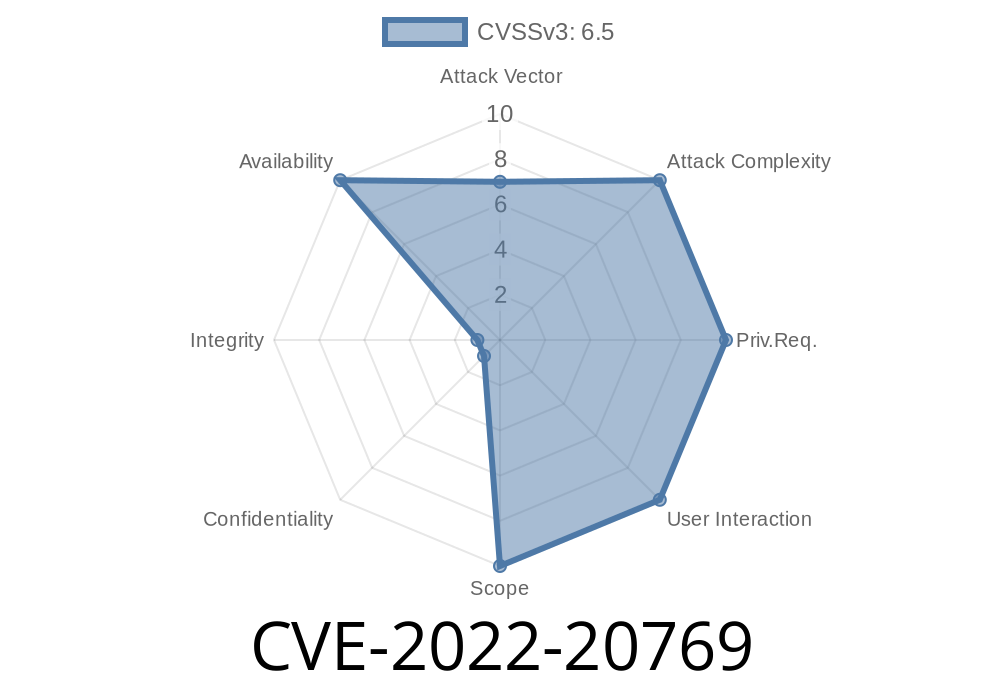
To exploit this vulnerability, an attacker must be within the wireless range of the device and access the management interface of the device. Access to the management interface can be gained by using social engineering tactics or by using a rogue wireless access point. Cisco has assigned this vulnerability a severity rating of High. CVSS Scores: Summary: CVSS v3 Scores Critical Impact 6/10 Exploitability 6/10 Exploitability Putting aside the fact that this is a wireless controller, AireOS is a very secure wireless controller. The fact that the controller can be exploited at all is a good sign. Exploitation of a wireless controller is not something to be taken lightly. Cisco has a very good track record when it comes to security, so you can be assured that this is a very serious vulnerability. Cisco has provided a patch for this vulnerability to reduce the risk of exploitation. Note: Cisco has provided a patch for this vulnerability with AireOS version 2.3.12. AireOS version 3.0 is not vulnerable. Cisco has provided a patch for this vulnerability with AireOS version 2.3.12. AireOS version 3.0 is not vulnerable. Cisco has provided a patch for this vulnerability with AireOS version 2.3.12. AireOS version 3.0 is not vulnerable. Cisco has provided a patch for this vulnerability with AireOS version 2.3.12. AireOS version 3.0 is not vulnerable. Cisco has provided
What is AireOS?
AireOS is a wireless controller that manages the Wi-Fi network. It monitors and adjusts the network bandwidth to ensure smooth performance of Wi-Fi applications, such as video streaming, on mobile devices. AireOS is often used in enterprise networks by companies such as retailers who want to offer the best possible customer service experience.
Cisco AireOS Vulnerability Summary
A major vulnerability in AireOS version 2.3.12 has been found and exploited. The vulnerability is CVE-2022-20769, and it is assigned a severity rating of High by Cisco. This vulnerability affects all devices that use AireOS version 2.3.12 and can be exploited without authentication, but needs to be within the wireless range of the device and access the management interface of the device. There are three different ways this vulnerability can be exploited: using social engineering tactics or using a rogue wireless access point, which Cisco has given a severity rating of High as well
Understanding the AireOS Vulnerability
AireOS is a wireless controller that provides connectivity to the Aire family of wireless products. This vulnerability could allow an attacker on the same network as the device to take control of it remotely. To exploit this vulnerability, an attacker must be within the wireless range of the device and access the management interface of the device. Access to the management interface can be gained by using social engineering tactics or by using a rogue wireless access point.
Cisco AireOS Version 3.0 (released 2017-11-21)
The AireOS version 3.0 exploit is not vulnerable to this attack.
Cisco has provided a patch for this vulnerability with AireOS version 2.3.12. AireOS version 3.0 is not vulnerable
Timeline
Published on: 09/30/2022 19:15:00 UTC
Last modified on: 10/04/2022 18:58:00 UTC