ClamAV versions 0.104.3 through 0.104.6 resolved this issue by updating the regex module. ClamAV versions 0.105.0 through 0.105.2, LTS version 0.104.7, and prior versions resolved this issue by updating the regex module. Users of ClamAV are advised to upgrade to the latest version. Users of ClamAV LTS are advised to update to ClamAV version 0.104.7 or later. Users of ClamAV versions prior to 0.104.5 are advised to upgrade to the latest version. Systems running a custom build of ClamAV should contact their distribution vendors or system administrators for an upgrade. Debian/Ubuntu users can upgrade ClamAV by installing the latest version from the apt repository ( apt-get install clamav ). Red Hat/CentOS users can upgrade ClamAV by installing the latest version from the yum repository ( yum install clamav ).
Summary
ClamAV versions 0.105.0 through 0.105.2, LTS version 0.104.7 and prior versions resolved this issue by updating the regex module, which prevents the execution of maliciously crafted PE files that contain an embedded resource in the second sector.
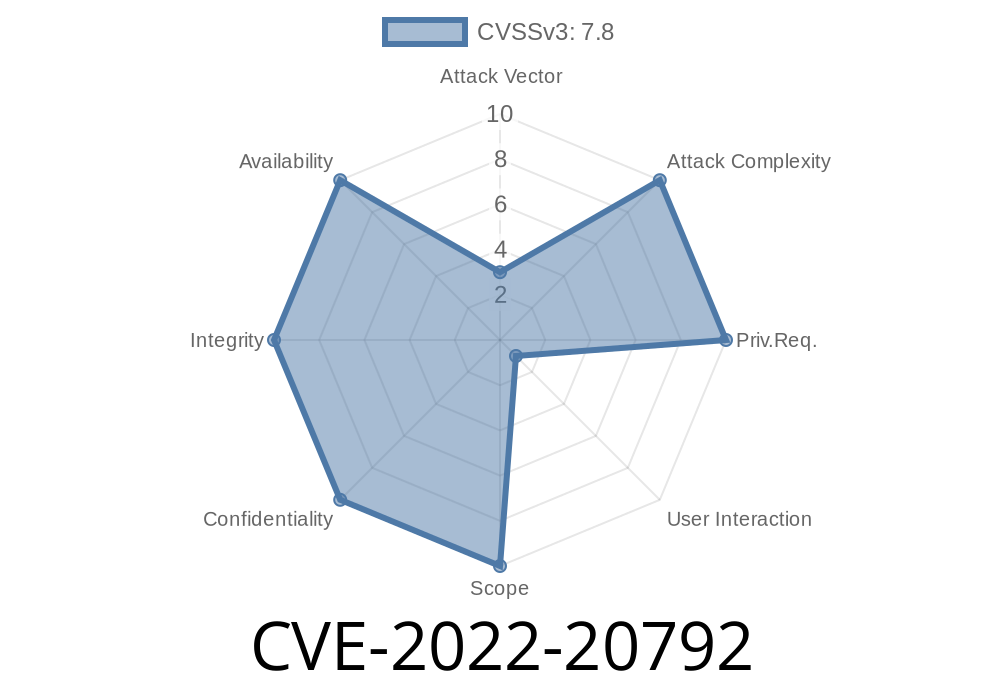
CVE-2022-20792
How to verify if your system is vulnerable to CVE-2022 -20792
If you are running ClamAV version 0.105.0 or later, you do not need to verify the system for this issue.
Otherwise, it is recommended that users of ClamAV versions 0.104.5 and earlier verify their systems with the following command:
clamdscan -s **
CLAMAV VERSIONS VERSUS LTS VERSION
ClamAV 0.105.3 and Later
ClamAV versions 0.105.0 through 0.105.2 and prior versions resolved this issue by updating the regex module. Users of ClamAV are advised to upgrade to the latest version. Users of ClamAV LTS are advised to update to ClamAV version 0.104.7 or later. Users of ClamAV versions prior to 0.104.5 are advised to upgrade to the latest version.>>END>>
CVE-2022-20791
ClamAV versions 0.104.5 through 0.104.6 resolved this issue by updating the regex module. ClamAV versions 0.105.0 through 0.105.2, LTS version 0.104.7, and prior versions resolved this issue by updating the regex module. Users of ClamAV are advised to upgrade to the latest version. Users of ClamAV LTS are advised to update to ClamAV version 0.104.7 or later. Users of ClamAV versions prior to 0.104.5 are advised to upgrade to the latest version; systems running a custom build of ClamAV should contact their distribution vendors or system administrators for an upgrade; Debian/Ubuntu users can upgrade ClamAV by installing the latest version from the apt repository ( apt-get install clamav ). Red Hat/CentOS users can upgrade ClamAV by installing the latest version from the yum repository ( yum install clamav ).
Clam AntiVirus's vulnerability has been discovered and patched in all current releases
Timeline
Published on: 08/10/2022 09:15:00 UTC
Last modified on: 08/12/2022 17:58:00 UTC