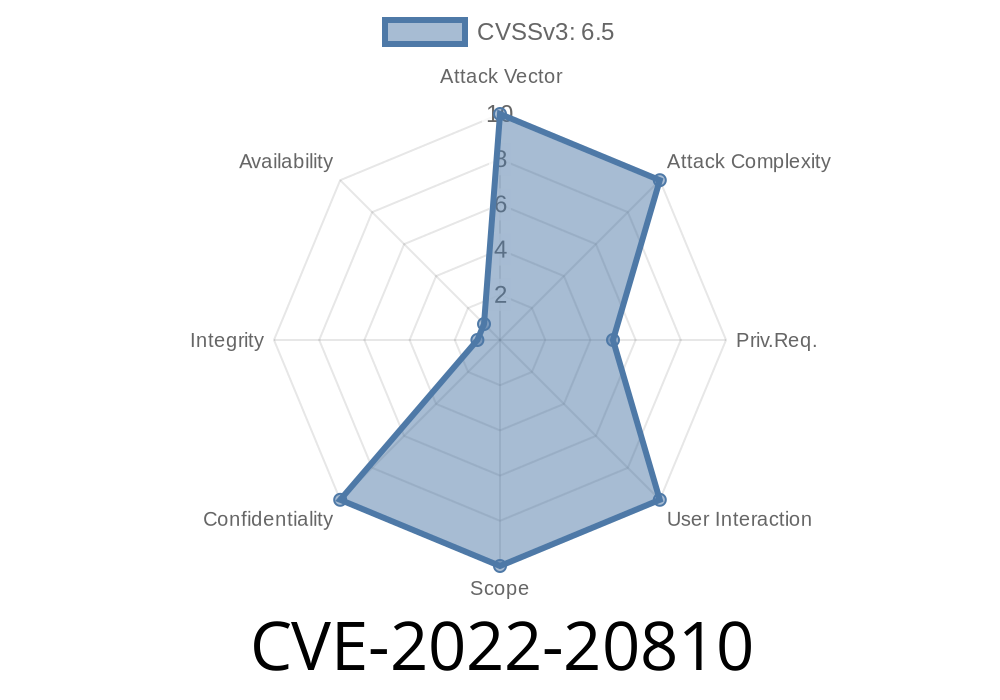
This vulnerability is due to insufficient input validation for configuration parameters. An attacker could exploit this vulnerability by sending crafted SNMP requests to the targeted device. A successful exploit could allow the attacker to determine the version of software running on the targeted device. Cisco has confirmed this vulnerability and released software updates. To prevent network exposure through SNMP, be sure to have SNMP version 3 enabled, and restrict access to the community read-only view. If you are unsure if your device is running SNMP, you can view the configuration of your device through the show version command. What to do if you are affected? If you are using Cisco IOS XE Wireless Controller Software on a Cisco Catalyst 9000 Family switch, there are no actions that need to be taken. Cisco has released software updates and you will receive these through your network device vendor. Work with your network device vendor to ensure that you have applied the appropriate software update. End-users of the Cisco Catalyst 9000 Family switch should contact their network device vendor to determine if they have applied the appropriate software update. If you are using Cisco IOS XE Wireless Controller Software on a Cisco Catalyst 9000 Family switch, there are no actions that need to be taken. Cisco has released software updates and you will receive these through your network device vendor
Cisco IOS Software
Cisco IOS Software is a software that is used by Cisco devices to manage and configure their systems. The software also runs on other types of devices such as routers, switches, and firewalls.
To find out if your device is running Cisco IOS Software, use the show version command.
Cisco IOS XE Software Disruption of Traffic on Certain Cisco Catalyst 9000 Family Switches
A vulnerability exists in the Cisco IOS XE Wireless Controller Software on a Cisco Catalyst 9000 Family switch that could cause disruption of traffic on certain switches. This vulnerability is due to insufficient input validation for configuration parameters. An attacker could exploit this vulnerability by sending crafted SNMP requests to the targeted device. A successful exploit could allow the attacker to determine the version of software running on the targeted device. Cisco has confirmed this vulnerability and released software updates. To prevent network exposure through SNMP, be sure to have SNMP version 3 enabled, and restrict access to the community read-only view. If you are unsure if your device is running SNMP, you can view the configuration of your device through the show version command. What to do if you are affected? If you are using Cisco IOS XE Wireless Controller Software on a Cisco Catalyst 9000 Family switch, there are no actions that need to be taken. Cisco has released software updates and you will receive these through your network device vendor. Work with your network device vendor to ensure that you have applied the appropriate software update. End-users of the Cisco Catalyst 9000 Family switch should contact their network device vendor to determine if they have applied the appropriate software update
Cisco Disruption of Traffic on Certain Switches
A vulnerability exists in one component included with certain Cisco Catalyst 9500 Series switches which could cause disruption of traffic on certain switches. This vulnerability is due to insufficient input validation for configuration parameters in a component included with certain Cisco Catalyst 9500 Series
Timeline
Published on: 09/30/2022 19:15:00 UTC
Last modified on: 10/04/2022 19:18:00 UTC