To exploit this vulnerability, an attacker would need to send a UDP packet to the device that has a specific payload. The device would respond by sending a UDP packet back to the source of the original request. An attacker could exploit this vulnerability by sending specially crafted packets to an affected device. An exploit could allow the attacker to cause the device to reload, resulting in a DoS condition. Cisco IOS XE Software for Embedded Wireless Controllers does not process TCP traffic. This vulnerability does not affect Cisco IOS XR Software. Cisco XR Series Software can be installed on the same device as Cisco IOS XE Software for Embedded Wireless Controllers. Cisco XR Series Software does not process UDP traffic. Cisco XR Series Software cannot be exploited to exploit this vulnerability. Cisco IOS XE Software for Embedded Wireless Controllers is not enabled by default. To exploit this vulnerability, an attacker must have the ability to send a UDP packet to an affected device. This can be achieved through either remote access or through the implementation of a malicious DDNS server. End users cannot exploit this vulnerability. Cisco IOS XE Software for Embedded Wireless Controllers is not enabled by default. To enable the feature, the following command must be issued from an operational Cisco IOS XE Software for Embedded Wireless Controllers device: feature enable ips_uap_enable=enable
Vulnerability Characterization
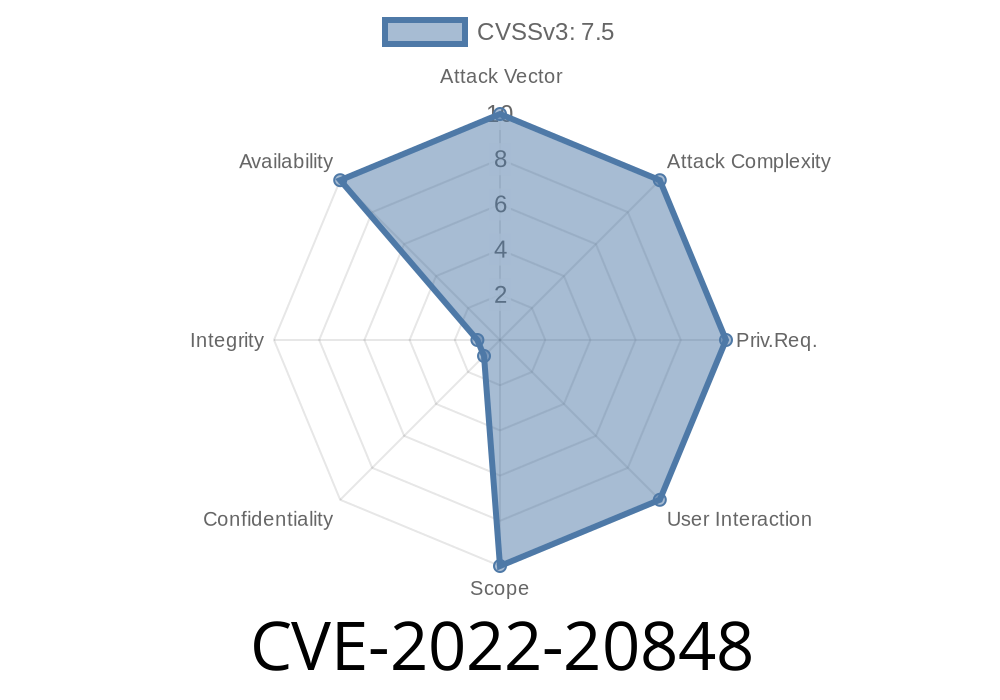
CVE-2022-20848 is a UDP packet injection vulnerability that affects Cisco IOS XE Software for Embedded Wireless Controllers. The vulnerability allows an attacker to exploit a DoS condition by sending specially crafted packets to an affected device. An exploit could allow the attacker to cause the device to reload, resulting in a DoS condition. Cisco XR Series Software can be installed on the same device as Cisco IOS XE Software for Embedded Wireless Controllers. Cisco XR Series Software does not process UDP traffic, therefore this vulnerability cannot be exploited by users of the software.
Cisco IOS XE Software for Embedded Wireless Controllers is not enabled by default. To exploit this vulnerability, an attacker must have the ability to send a UDP packet to an affected device through either remote access or through the implementation of a malicious DDNS server.
Vulnerable Evolved Packet System Software
The Cisco IOS XE Software for Embedded Wireless Controllers is vulnerable to this vulnerability. The Cisco IOS XE Software for Embedded Wireless Controllers is not enabled by default on any device. To enable the feature, the following command must be issued from an operational Cisco IOS XE Software for Embedded Wireless Controllers device: feature enable ips_uap_enable=enable
Timeline
Published on: 09/30/2022 19:15:00 UTC
Last modified on: 10/05/2022 16:17:00 UTC