This vulnerability does not allow an attacker to inject and run arbitrary code on an affected device. However, if the attacker has privileged access to the device, they could exploit this vulnerability to gain administrative access to the device and move laterally between devices. Cisco IOS XE Software releases 16.11.1 and later are not vulnerable to this issue. Workarounds There are no known workarounds for this issue. Fixed Software Cisco released fixed software for these vulnerabilities. Customers should upgrade to the latest releases.
4. Vulnerability – Unauthenticated, Physical Attackers Could Gain Administrative Access to Cisco IOS XE Software for Cisco Catalyst 9200 Series Switches In some cases, unauthenticated, physical attackers could gain administrative access to Cisco IOS XE Software for Cisco Catalyst 9200 Series Switches. This issue is due to insufficient auditing of the privileged commands in the code that manages the login process of privileged mode. An attacker could exploit this vulnerability by being physically close to the device to log in. To exploit this vulnerability, the attacker needs either unauthenticated physical access to the device or privileged access to the root shell on the device. Note: In Cisco IOS XE Software releases 16.11.1 and later, root shell access is protected by the Consent Token mechanism. This vulnerability does not allow an attacker to inject and run arbitrary code on an affected device
Description of the Cisco IOS Software Software Vulnerability
A vulnerability in Cisco IOS Software could allow an unauthenticated, physical attacker to gain administrative access to the device if they are physically close to the device. The issue is due to insufficient auditing of the privileged commands in the code that manages the login process of privileged mode. An attacker could exploit this vulnerability by being physically close to a targeted device and log in.
Overview
Cisco IOS XE Software releases 16.11.1 and later are not vulnerable to this issue.
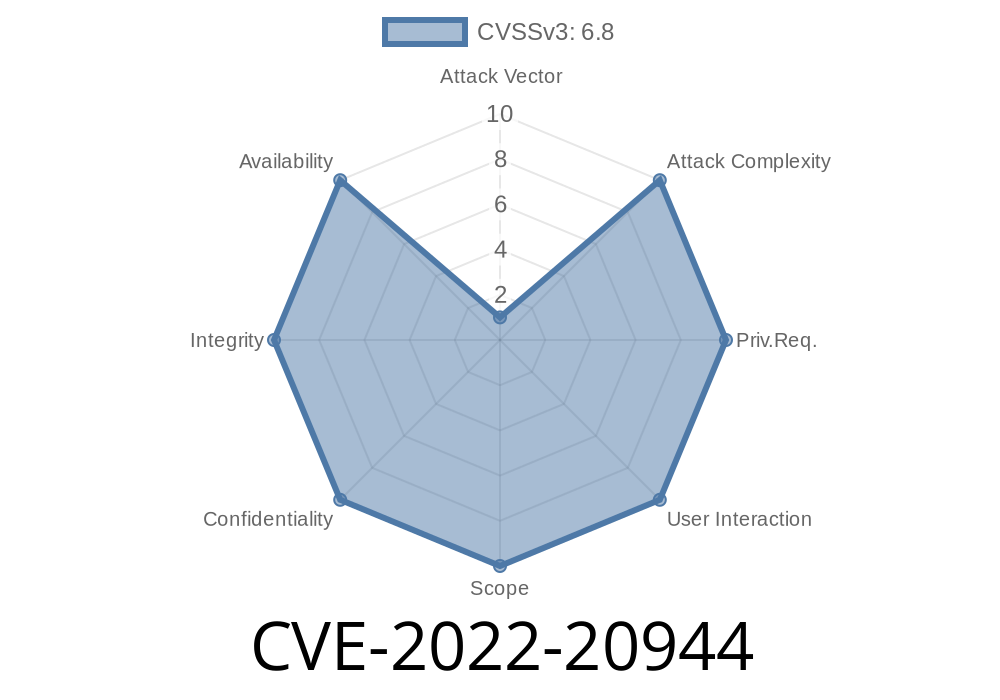
CVE-2022-20944
This vulnerability does not allow an attacker to inject and run arbitrary code on an affected device. However, if the attacker has privileged access to the device, they could exploit this vulnerability to gain administrative access to the device and move laterally between devices. Cisco IOS XE Software releases 16.11.1 and later are not vulnerable to this issue. Workarounds There are no known workarounds for this issue. Fixed Software Cisco released fixed software for these vulnerabilities. Customers should upgrade to the latest releases.
Timeline
Published on: 10/10/2022 21:15:00 UTC
Last modified on: 10/13/2022 19:43:00 UTC