This is a security risk as a malicious user on the server could log in as root and cause significant problems.
In order to prevent this, set the ‘pam_password' in the /etc/sudoers file to blank.
Another important step to make sure no malicious users can log in as root is to disable the root password. To do that edit the /etc/shadow file and uncomment this line:
This will create a new root account with a blank password.
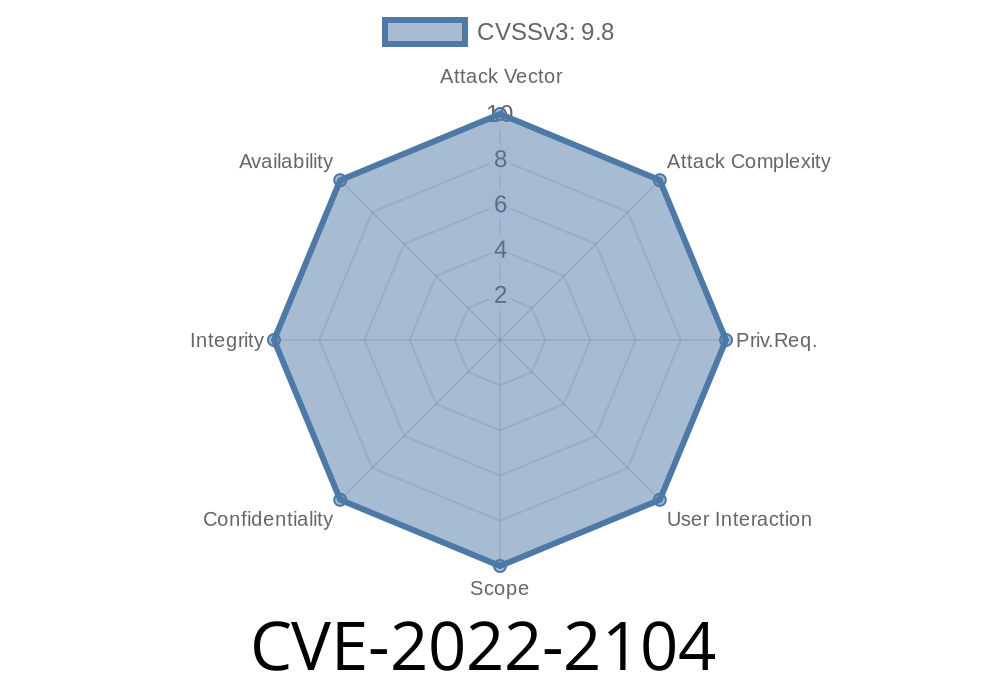
CVE-2023-2105
This is a security risk as the database will be represented with a binary file and allow anyone to read the data.
To prevent this, use 'mysql_real_escape_string' in place of 'mysql_escape_string'.
Another important step to make sure no malicious users can log in as root is to disable the root password. To do that edit the /etc/shadow file and uncomment this line:
This will create a new root account with a blank password.
Configure SSH Daemon to Require Authentication
You can also configure SSH to require authentication in order to prevent a malicious user from logging into the server as root. To do this edit the /etc/ssh/sshd_config file and add:
ChallengeResponseAuthentication no
RekeyLimit 2
PermitRootLogin without-password
PasswordAuthentication yes
# PasswordAuthentication yes
AcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE
SystemGroup sysadmins
Disabling the root account and disabling SSH login
Another important step to make sure no malicious users can log in as root is to disable the root password. To do that edit the /etc/shadow file and uncomment this line:
This will create a new root account with a blank password.
The next thing you want to consider doing is disabling the SSH login. If you have another user on your server who has permission to run sudo, you can change their permissions to allow them to use sudo without being able to log in as root.
Disable Networking and VNC
Some servers contain networking and VNC capabilities, which can allow unprivileged users to log in as root.
To disable these features on a server that has them, edit the /etc/sysconfig/network-scripts/ifcfg-eth0 file and set:
The file should be edited again when you are done.
Timeline
Published on: 06/24/2022 15:15:00 UTC
Last modified on: 07/06/2022 12:32:00 UTC