In November 2021, Oracle published a security advisory for CVE-2022-21245, a vulnerability discovered in the MySQL Server product, specifically targeting the “Server: Security: Privileges” component. Affecting widely-used versions—including MySQL 5.7.36 and earlier plus MySQL 8..27 and earlier—this bug enables someone with low-level credentials and network access to change or delete MySQL data they should never be able to touch. This post will guide you through what the vulnerability is, how it works, a generic exploit scenario, and what you can do to stay safe.
The Essentials
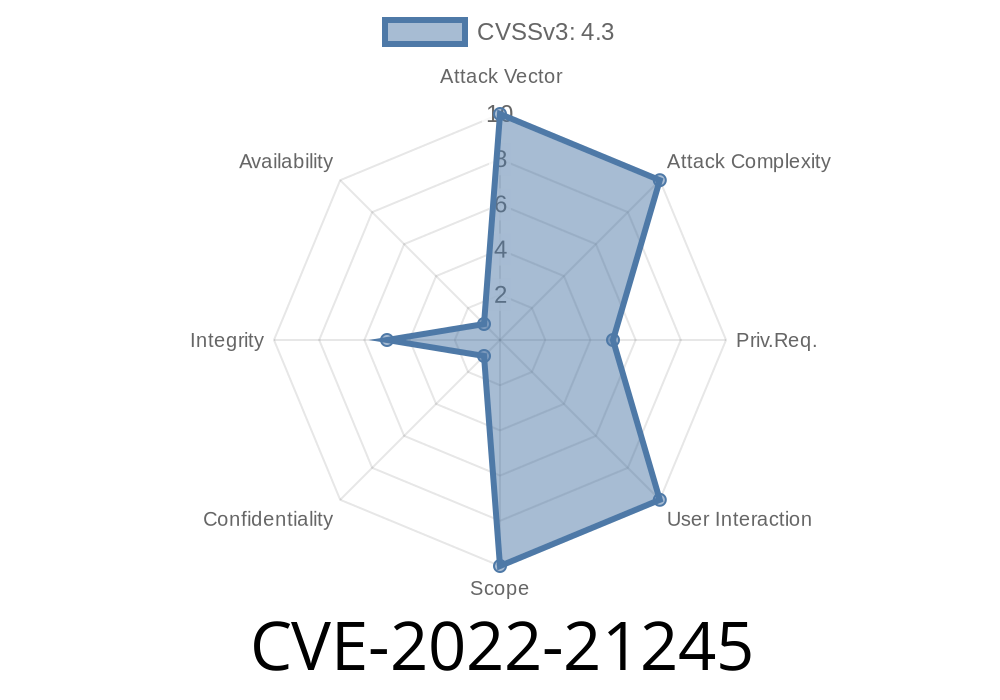
- Vulnerability ID: CVE-2022-21245
User Interaction: None
- Impact: Unauthorized UPDATE/INSERT/DELETE access to MySQL data
What Exactly Is CVE-2022-21245?
The bug exists in the MySQL *privilege checking logic*—code that’s designed to prevent unauthorized users from making database changes. CVE-2022-21245 arises when the privilege system doesn’t correctly restrict access for users with low privileges—like a regular web app or reporting account—but, via certain SQL commands or combinations, they're able to perform UPDATE, INSERT, or DELETE operations on protected tables.
This isn’t a bug that lets anyone just walk right in and become root, but it can let a legit user do things they’re supposed to be blocked from. In effect, someone with a regular (authenticated—but not administrator) account could change or erase rows in database tables that should be off-limits to them.
The full Oracle advisory is here
- Oracle Critical Patch Update Advisory - November 2021
(see MySQL, CVE-2022-21245).
Let’s build a simple scenario
- The Setup: A company gives its sales team access to view the sales_records table but only lets managers update it. The sales team has a read-only account called sales_reader.
The Goal: An attacker with the sales_reader credentials wants to change sales numbers.
- The Flaw: Due to CVE-2022-21245, with some trickery, the attacker can exploit the privilege bypass bug to run unauthorized UPDATE or DELETE queries on sales_records.
Here's how a basic exploitation might look (simplified for illustration)
-- Connect using low privileged account
mysql -h 192.168.1.100 -u sales_reader -p
-- Try forbidden update (should fail in a secure system)
UPDATE sales_records SET total=100 WHERE sale_id=42;
-- On vulnerable server (pre-patch), this could *succeed* even if sales_reader shouldn't have UPDATE privileges!
In many real-world cases, attackers combine this with further SQL trickery, such as using stored procedures, views, or exploiting logic errors in the affected MySQL privilege code to achieve the unauthorized modification.
Real-World Example
Let’s get more technical. Sometimes, certain granular privilege combinations on older MySQL grant tables mistakenly allowed a SELECT privilege to slip into UPDATE or DELETE under specific query constructions. For example:
-- Attacker has a SELECT on a view, but the view exposes an underlying table
SELECT * FROM view_sales; -- Legit
-- Attacker works out a way to craft an UPDATE trick via prepared statements or using multi-table operations
UPDATE view_sales SET total = 900 WHERE sale_id = 42;
Result: Old unpatched MySQL mistakenly executes the update on the underlying table, bypassing intended limitations.
Why Is This So Serious?
- Not a full takeover: The attacker can’t run arbitrary code or dump the entire database—but data integrity is threatened.
- Think about business risk: Tampering with invoices, billing, or user balances could lead to real-world fraud, lawsuits, or compliance penalties.
How Can You Protect Your Business?
1. Patch your MySQL servers!
Upgrade immediately to any version above 5.7.36 or 8..27. Oracle has released a fix in later versions.
2. Review & restrict MySQL privileges:
Check that no “low privileged” accounts have more access than strictly necessary. Run
SHOW GRANTS FOR 'sales_reader'@'%';
3. Monitor for unauthorized changes:
Implement audit logging or triggers to catch unexpected data modifications.
More Technical Resources
- NIST NVD Entry for CVE-2022-21245
- Oracle MySQL Security Notes
- Common Best Practices for MySQL Security
Conclusion
CVE-2022-21245 is a reminder that even basic privilege bugs can have a big impact. If you use Oracle MySQL (especially an older 5.7.x or 8..x release), make sure to check your version and patch ASAP. Don’t let an internal or external attacker get more access than you bargained for!
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 04/19/2022 04:13:00 UTC