CVE-2022-21247 is a security vulnerability found within the Core RDBMS component of Oracle Database Server, specifically affecting supported versions 12.2..1 and 19c. While its CVSS 3.1 Base Score is a modest 2.7, which might not seem alarming at first glance, the vulnerability can allow high-privileged users to access sensitive data without proper authorization. This article unpacks the vulnerability, shows code snippets to demonstrate risk, explains how it can be exploited, and points you to key resources for further reading.
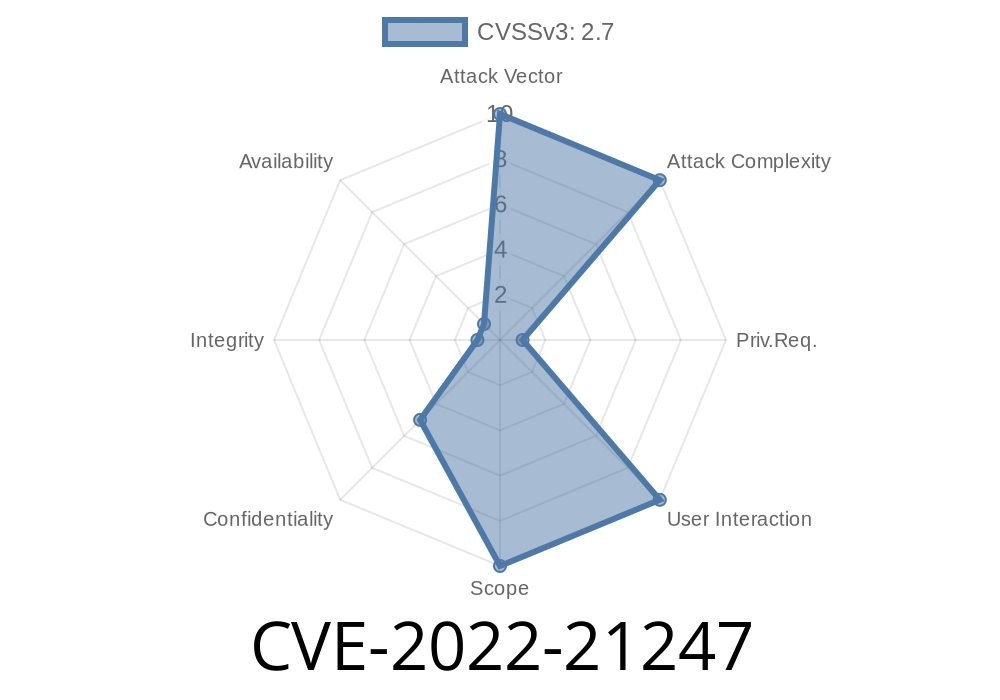
CVSS: 2.7 (Confidentiality impact only)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:N/A:N
In a nutshell: An attacker *already* trusted on the network and database (with elevated privileges) can easily exploit this vulnerability to read data they shouldn’t see.
Under the Hood: Why Does This Vulnerability Exist?
The core of CVE-2022-21247 is a flaw in how Core RDBMS processes certain privileged operations. Incorrect privilege checks mean that a user with EXECUTE CATALOG ROLE can invoke specific procedures or access catalog objects to leak data—data that should be off-limits.
Who is at risk?
If your database allows multiple high-privileged users (like DBAs, or app users with catalog access), and you rely on strict separation of duties, this vulnerability could enable credentialed users to snoop beyond their intended scopes.
Example Exploit: Unauthorized Data Read via Catalog Procedure
Suppose there’s a packaged procedure in the Oracle data dictionary that exposes data from internal tables. An attacker might do something like this:
-- Connect as malicious user with required privileges
CONNECT attacker/password@oracledb
-- Check granted roles and access
SELECT * FROM SESSION_ROLES;
-- Attempt to access data dictionary views, maybe expecting failure
SELECT * FROM DBA_USERS WHERE USERNAME = 'SYS';
-- Use a PL/SQL procedure (available due to EXECUTE CATALOG ROLE) to fetch restricted data
DECLARE
l_user_info VARCHAR2(100);
BEGIN
SYS.DBMS_METADATA.GET_XML('USER', 'SYS', 'SYS');
-- or another SYS-owned package accessible via the catalog role
END;
/
> NOTE: The actual procedure for exploit may vary, depending on grants and Oracle patching. The key idea is the misuse of privileged system packages via catalog role.
If unpatched, this would allow ATTACKER to read details about the SYS account (or others), which should *never* be available.
Mitigating the Issue
Oracle has published a patch. As always, the best defense is to apply the latest Oracle Critical Patch Update (CPU) that addresses CVE-2022-21247. You can find these at Oracle’s official sources:
- Oracle Critical Patch Update Advisory - April 2022
- Oracle Database Security Updates
References & Further Reading
- Oracle CVE-2022-21247 Advisory
- NIST National Vulnerability Database: CVE-2022-21247
- Oracle CPU Advisory - April 2022
- Oracle Documentation on Grants, Roles, and Catalogs
Conclusion
While CVE-2022-21247 isn't a remote, unauthenticated RCE, it highlights why least privilege is so important—even for users who are inside your organization. Anyone granted catalog access on Oracle Database Server versions 12.2..1 and 19c can quietly bypass information barriers and snoop on protected data. Patch early, audit often, and keep privileges minimal to prevent data exposure via vulnerabilities like this one.
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 01/22/2022 03:42:00 UTC